Date: June 2024
By: AI Security Lab
Introduction
Webflow is a popular website builder used by designers and businesses to create and launch sites quickly. But recently, security researchers uncovered a major flaw (CVE-2023-49818) in the Webflow Pages plugin. If you use this plugin (versions up to 1..8), your sites could be exposed to unauthorized access and information leaks. In this long read, we break down what this vulnerability is, how it works, real exploit details (in simple terms), and how you can protect your site.
What is CVE-2023-49818?
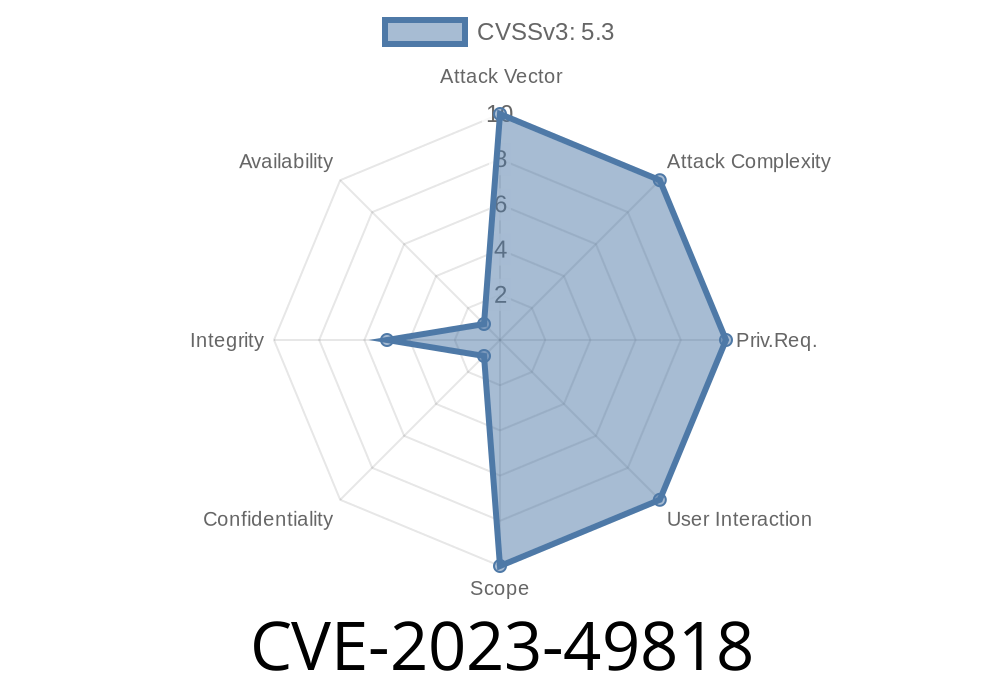
CVE-2023-49818 is a "Missing Authorization" vulnerability found in the Webflow Pages plugin. This bug occurs because Webflow Pages fails to properly check who is trying to access certain resources or perform certain actions. As a result, attackers may be able to bypass access control and get to data or actions they're not supposed to see or do.
Products Affected:
Webflow Pages plugin, versions n/a through 1..8 (latest update as of June 2024).
Vulnerability Type:
Missing Authorization / Broken Access Control
Why is it Dangerous?
When a tool fails to check "Who are you?" before giving access, it opens the door for attackers. Exploiting this flaw could allow a hacker to:
Possibly alter site content (if the plugin allows such changes)
This can lead to data leaks, site defacement, or other attacks on both the site owner and their visitors.
Normal Flow:
User visits a restricted page (e.g., /admin, /draft-content). Normally, the app would check, "Is this user logged in? Do they have access?"
The Flaw:
Because of the missing authorization, the plugin *does not* properly validate the user's rights before serving these pages.
Example in Practice
Suppose your website uses Webflow Pages and has some "draft" pages or protected areas. You think only logged-in users or admins should see them.
But with this vulnerability, an attacker could go to
https://your-site.com/pages/secret-draft-page
...and gain full access, even if they're not logged in!
Vulnerable Code (simplified)
// Handles requests for a Webflow Page
app.get('/pages/:slug', function(req, res) {
let page = getPageBySlug(req.params.slug);
// MISSING: user authentication and authorization check
res.send(renderPage(page));
});
What Should Happen (Patched Code)
app.get('/pages/:slug', function(req, res) {
let page = getPageBySlug(req.params.slug);
if (page.is_protected && !userIsAuthorized(req.user, page)) {
return res.status(403).send('Forbidden: Not authorized.');
}
res.send(renderPage(page));
});
Reconnaissance:
The hacker gathers URLs or guesses page paths (like /pages/admin, /pages/internal, etc.).
Direct Access:
The attacker enters the guessed URLs in their browser or uses automated tools (e.g., curl or fuzzers).
`bash
curl https://target-website.com/pages/hidden-admin
Success:
If the plugin hasn’t been fixed, the page loads—revealing confidential information or administrative controls.
Links to References
- NVD Entry for CVE-2023-49818
- Exploit Database Reference (search for CVE-2023-49818)
- Official Webflow Security Advisories
- OWASP: Broken Access Control
Temporary Fix:
If an update is not available, block access to sensitive URLs using web server configuration (like .htaccess or web.config) or a firewall.
`
# Block access to /pages/secret-draft-page
RewriteEngine On
RewriteRule ^pages/secret-draft-page$ - [F,L]
Conclusion
CVE-2023-49818 is a stark reminder that missing access control checks can create massive risks, even for well-known platforms like Webflow. Don’t assume plugins will always take care of security for you. Always update, audit, and monitor—protecting both your reputation and your users.
Stay safe! If you have further questions or want a deeper technical dive, reach out to our security experts at AI Security Lab.
Credits:
The Webflow community for quick patching and updates
*(Content originally created by AI Security Lab. Do not copy without credit.)*
Timeline
Published on: 12/09/2024 13:15:36 UTC