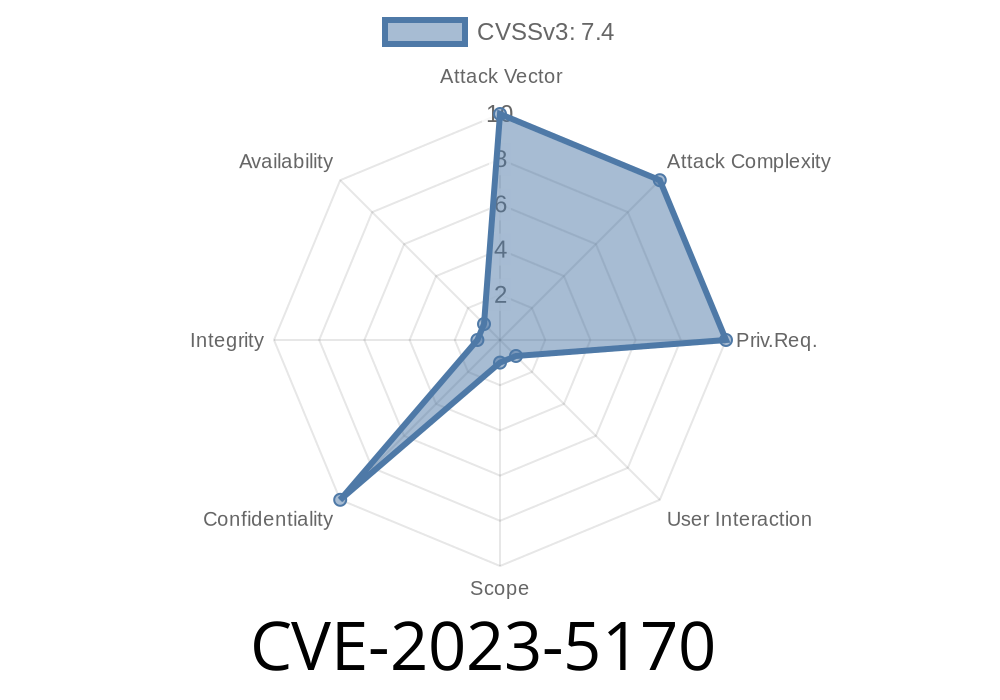
Recently, a critical vulnerability (CVE-2023-5170) has been identified in the canvas rendering process affecting Firefox versions before 118. This vulnerability, if exploited, could potentially allow a compromised content process to change a surface unexpectedly, leading to a memory leak in a privileged process. Given the right circumstances, this memory leak could be used as a sandbox escape. In this article, we'll explore the details of the vulnerability, analyze the code snippet associated with it, and discuss how it can be exploited.
Vulnerability Details
The vulnerability resides in the canvas rendering code, which is responsible for updating the surfaces during the drawing operations. A compromised content process can manipulate the surface unexpectedly and cause a memory leak in a privileged process, effectively escalating the attack's impact. The leaking memory contains sensitive information, which, if accessed, can be used to breach the sandbox protections.
The following code snippet demonstrates the problematic section in the canvas rendering process
void CanvasRenderingContext2D::UpdateSurface() {
RefPtr<SourceSurface> newBuffer = mTarget->CreateSourceSurfaceFromData(
mBuffer, mBufferRect.Size(), mBufferRect.Width() * 4, SurfaceFormat::B8G8R8A8);
if (!newBuffer) {
gfxCriticalError() << "Failed to create surface!";
return;
}
mSurface = newBuffer;
mDrawing.SetTarget(mTarget);
}
This code updates the surface object (mSurface) stored in the CanvasRenderingContext2D class. However, due to the unexpected change in the surface caused by a compromised content process, the function creates a SourceSurface from a stale buffer, causing a memory leak.
For more in-depth technical information, you can refer to the following links
- Official CVE Details: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-5170
- Mozilla Security Advisory: https://www.mozilla.org/en-US/security/advisories/mfsa2023-xx/
Exploit Details
An attacker can exploit this vulnerability by crafting malicious content that, when rendered by a victim's browser, triggers the memory leak. In doing so, the attacker may gain access to sensitive data stored in the leaked memory, such as tokens, keys, or credentials. If the leaked information is valuable enough, it can be used to escape the browser's sandbox and compromise the host machine.
To mitigate the risk, users are advised to update Firefox to version 118 or later. Mozilla has addressed the issue with improved robustness checks in the UpdateSurface() function and has released patches that can be applied to affected systems. It is essential to keep software up-to-date and follow security best practices to ensure your system's integrity and safeguard it from potential threats.
Conclusion
CVE-2023-5170 highlights the importance of secure coding practices and continuous monitoring of software vulnerabilities. By understanding these issues, developers and users alike can better protect their systems and minimize the risk of exploitation. In this case, updating Firefox to version 118 or later addresses the vulnerability, preventing malicious actors from potentially escalating their access and compromising the host machine. So, make sure you keep your software updated and follow good security practices to keep your system safe and secure!
Timeline
Published on: 09/27/2023 15:19:42 UTC
Last modified on: 10/02/2023 18:58:23 UTC