A critical vulnerability with an associated identifier of VDB-240883 has been recently discovered in the Best Courier Management System 1., an open-source software system developed by SourceCodester. The vulnerable functionality is located in the file view_parcel.php, and it can be manipulated by attackers to perform an SQL injection when the argument id is tampered with.
This article will provide a detailed analysis of the exploit disclosure, include a code snippet to illustrate the vulnerability, and offer important links to original references. Please note that while the exploit is now public knowledge and may be used for malicious purposes, it is important for developers and system administrators to take necessary precautions and apply security patches.
Source of Vulnerability
The vulnerability lies within the Best Courier Management System 1.'s view_parcel.php file, which shows parcel information. Attackers can exploit this vulnerability by manipulating the id argument, giving them unauthorized access to the SQL database.
An attacker can abuse this critical vulnerability to their advantage by injecting malicious SQL queries into the vulnerable parameter. This can lead to unauthorized access, data manipulation, or even deleting critical information.
Code Snippet - Vulnerable Part of the Code
The vulnerable code snippet from the view_parcel.php file is as follows
<?php
$conn = mysqli_connect("localhost", "root", "", "elms");
$id = $_GET["id"];
$sql = "SELECT * FROM tblparcels WHERE Parcel_ID = $id";
$result = mysqli_query($conn, $sql);
while ($row = mysqli_fetch_assoc($result)) {
// Display parcel data
}
?>
As seen in the code above, the $id value is directly taken from the $_GET array without performing any input validation or sanitization. This allows attackers to craft malicious URLs to trigger the SQL injection.
Exploit Information
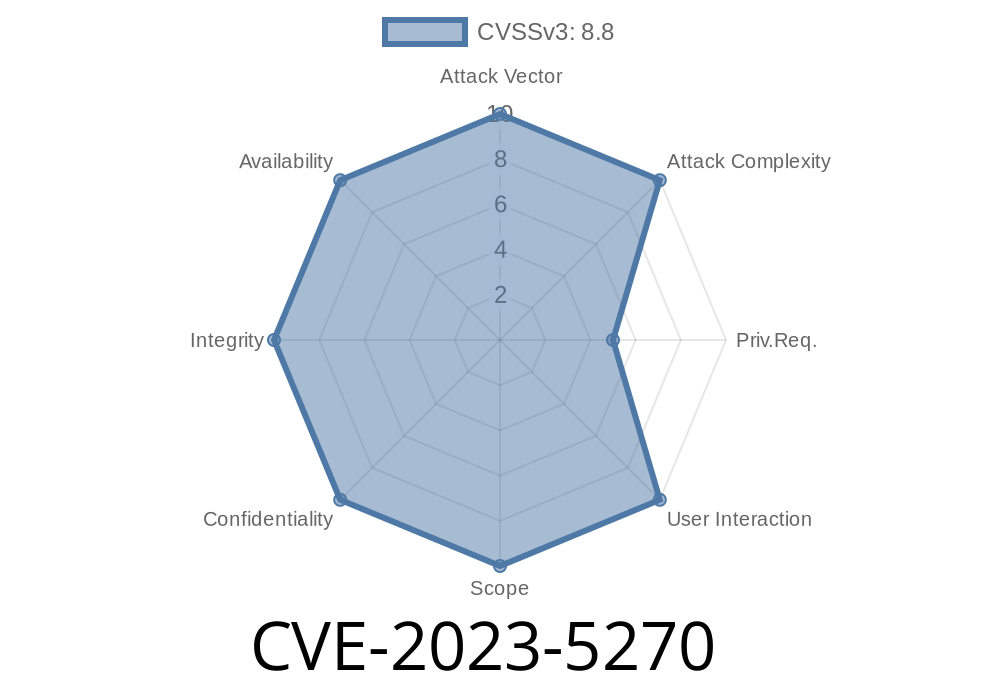
The exploit has been disclosed to the public and is now available for use, making it extremely important for developers and system administrators to apply necessary patches. The vulnerability has been assigned the CVE-2023-5270 identifier, and it has been classified as critical in severity.
Mitigation
To fix this vulnerability, input validation and sanitization techniques should be used to ensure that only valid data is processed. For instance, you can use the mysqli_real_escape_string() function to escape potentially harmful characters or the intval() function to ensure the input is treated as an integer.
<?php
$conn = mysqli_connect("localhost", "root", "", "elms");
$id = intval($_GET["id"]);
$sql = "SELECT * FROM tblparcels WHERE Parcel_ID = $id";
$result = mysqli_query($conn, $sql);
while ($row = mysqli_fetch_assoc($result)) {
// Display parcel data
}
?>
Adding either of these functions can significantly reduce the risk of experiencing an SQL injection via the id parameter.
Original References
For more information regarding this vulnerability, please refer to the following resources
1. SourceCodester Best Courier Management System 1. Source Code
2. CVE-2023-5270 Information
3. Vulnerability Database Entry (VDB-240883)
Conclusion
It is highly recommended that developers and administrators using SourceCodester's Best Courier Management System 1. review their implementation of the software and apply necessary security measures to protect against potential attacks exploiting the CVE-2023-5270 vulnerability. Implementing proper input validation and sanitization techniques can act as an effective defense against SQL injections and other similar security threats.
Timeline
Published on: 09/29/2023 16:15:10 UTC
Last modified on: 11/07/2023 04:23:44 UTC