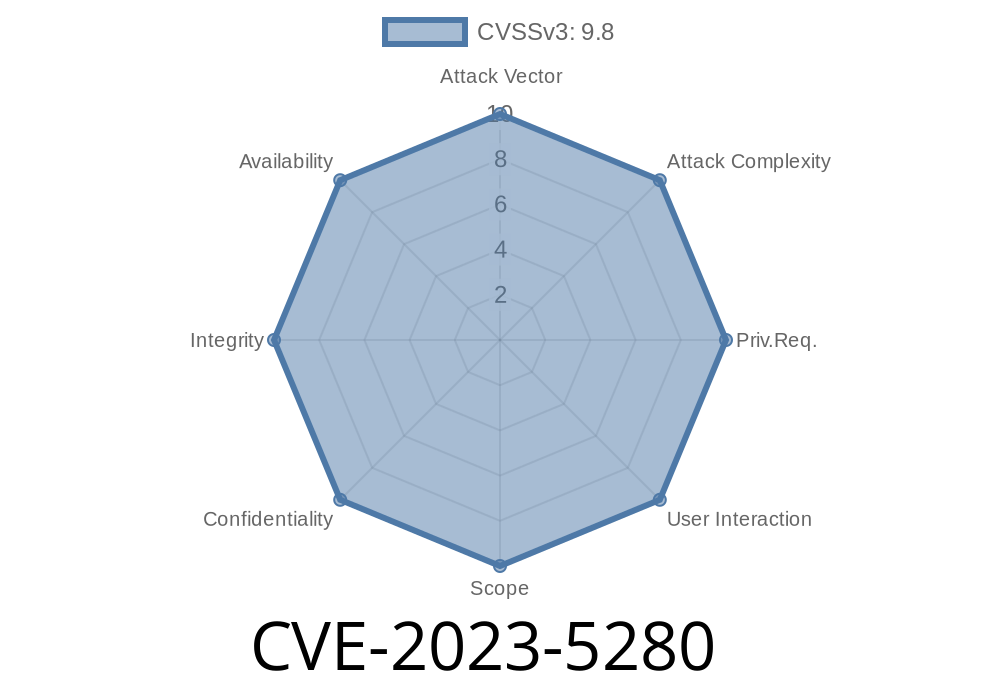
A newly discovered vulnerability (CVE-2023-5280) has been found in the SourceCodester Engineers Online Portal 1., which has been classified as critical. This vulnerability affects an unknown feature of the file my_students.php. The manipulation of the 'id' argument can lead to an SQL injection attack, potentially compromising the entire online portal. It is pertinent that users update their systems to mitigate any potential risks associated with this vulnerability.
Details of the Vulnerability
The vulnerability exists due to insufficient sanitization of the 'id' argument in the 'my_students.php' file. This allows attackers to inject and execute arbitrary SQL code to perform actions on the server. As this attack can be remotely launched, this poses a significant threat to any engineers utilizing the online portal.
The vulnerability identifier is VDB-240908, as documented in the following original reference: VDB-240908.
An example of the vulnerable code is shown below
// my_students.php
$id = $_GET['id'];
$query = "SELECT * FROM students WHERE id = $id";
$result = mysqli_query($con, $query);
In the above code snippet, the $id variable is directly retrieved from the $_GET array without proper input validation or sanitization. This leaves the door open for potential SQL injection attacks.
Exploit Details
An attacker can exploit this vulnerability by sending a crafted HTTP request to the targeted Engineers Online Portal. This request can include malicious SQL code, which will manipulate the database as desired by the attacker.
To demonstrate the exploit, an attacker could craft a URL similar to the one shown below
http://example.com/my_students.php?id=1'UNION SELECT 1,2,3,4,5...
In this example, the attacker injects SQL code to execute a UNION SELECT statement, which could potentially retrieve sensitive information stored in the web application.
Remediation
To resolve this vulnerability, ensure proper input validation and sanitization is implemented for any user-supplied data. One possible solution is to modify the vulnerable code snippet as shown below:
// my_students.php (fixed)
$id = mysqli_real_escape_string($con, $_GET['id']);
$query = "SELECT * FROM students WHERE id = $id";
$result = mysqli_query($con, $query);
In this revised snippet, the $id variable is now sanitized using mysqli_real_escape_string to prevent any SQL injection attacks.
Conclusion
CVE-2023-5280 is a critical vulnerability discovered in SourceCodester Engineers Online Portal 1. that affects the my_students.php file. Attackers can exploit this vulnerability through SQL injections launched remotely, posing a significant risk to the integrity and confidentiality of the online portal. Users should ensure their systems are updated to mitigate any potential threats associated with this vulnerability.
Timeline
Published on: 09/29/2023 18:15:10 UTC
Last modified on: 11/07/2023 04:23:46 UTC