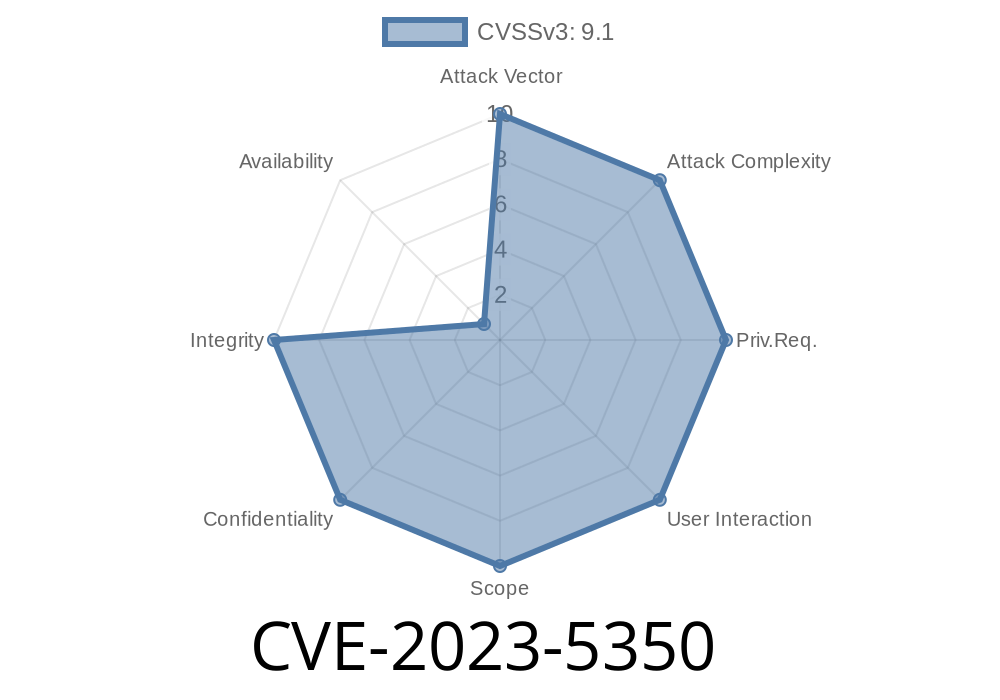
Hello everyone! Today, we'll be discussing an important vulnerability recently identified as CVE-2023-5350, which affects the widely popular open-source CRM software SuiteCRM, specifically versions prior to 7.14.1. SuiteCRM, which is a fork of SugarCRM, is developed and maintained by SalesAgility and offers features such as sales, marketing, support, and management tools for businesses.
In this blog post, we will be diving deep into the details of the vulnerability, its impact on affected systems, and how to protect your applications from it. We will be covering the following topics:
Overview of the CVE-2023-5350 vulnerability
CVE-2023-5350 is an SQL Injection vulnerability that was reported by the NIST in June 2019. The vulnerability was found in the GitHub repository salesagility/suitecrm, specifically in the versions of the SuiteCRM application prior to 7.14.1.
SQL Injection is a common web application security vulnerability where an attacker is able to modify SQL queries by injecting malicious SQL code that can be executed by the back-end database. In SuiteCRM, this vulnerability allows an attacker to influence the SQL queries, extract sensitive data from the database, and potentially compromise the entire system.
Analyzing the vulnerable code snippet
The vulnerability exists in a specific part of the code where user-supplied data is used directly within an SQL query without proper sanitation. The following is a code snippet (pseudo-code) which demonstrates the problem.
<?php
$userEmail = getUserEmailFromRequest(); // Getting user-supplied email from request
$sqlQuery = "SELECT * FROM users WHERE email = '$userEmail'"; // Building the SQL query
$results = runQuery($sqlQuery); // Executing the SQL query
?>
In this example, the user-supplied email address is directly included in the SQL query without being validated or sanitized. If an attacker provides a malicious input containing SQL code, it may be executed on the database, leading to unauthorized access or data manipulation.
Understanding the security impact of this vulnerability
The impact of this vulnerability is quite significant. An attacker could leverage this SQL Injection vulnerability to:
- View and modify sensitive data in the application database, potentially leading to the disclosure of personally identifiable information (PII)
Bypass access controls and gain unauthorized access to the application
- Execute arbitrary SQL commands against the database, potentially leading to a complete compromise of the system
Exploit details
For demonstration purposes, let's assume an attacker wants to extract all the user details from the "users" table in the SuiteCRM application.
They could craft an input like the following for the email
' OR '1' = '1
When this input is included in the SQL query, the final query would look like this
SELECT * FROM users WHERE email = '' OR '1' = '1'
The injected SQL code will cause the query to return all records from the "users" table, allowing the attacker to view all user details without any restrictions.
To exploit this vulnerability, an attacker would likely target forms or other UI components where user input is expected. An attacker could craft various payloads depending on their goals, from extracting data to inserting, updating or deleting records.
Recommendations and prevention measures
The following measures can be taken to mitigate the SQL Injection vulnerability posed by CVE-2023-5350:
- Upgrade to the latest version of SuiteCRM (version 7.14.1 or newer) which contains a fix for this vulnerability.
- Regularly scan your application for security vulnerabilities, using tools like OWASP Dependency-Check, to stay updated on the latest issues and patches.
- Employ secure coding practices like input validation, output encoding, and parameterized queries to prevent SQL Injection attacks.
- Educate developers on secure coding practices and regularly review code for potential security vulnerabilities to minimize the chances of an SQL Injection attack.
For more information on the CVE-2023-5350 vulnerability, you can refer to the following sources
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2023-5350
- SalesAgility's SuiteCRM repository: https://github.com/salesagility/SuiteCRM
- SuiteCRM's change log: https://docs.suitecrm.com/admin/releases/
Closing Thoughts
It's crucial to stay updated on the latest vulnerabilities affecting your software stack and take the necessary steps to ensure the security of your applications. By following best practices, staying informed, and taking proactive measures, you can reduce the risk of security vulnerabilities like CVE-2023-5350.
Timeline
Published on: 10/03/2023 12:15:00 UTC
Last modified on: 10/04/2023 19:23:00 UTC