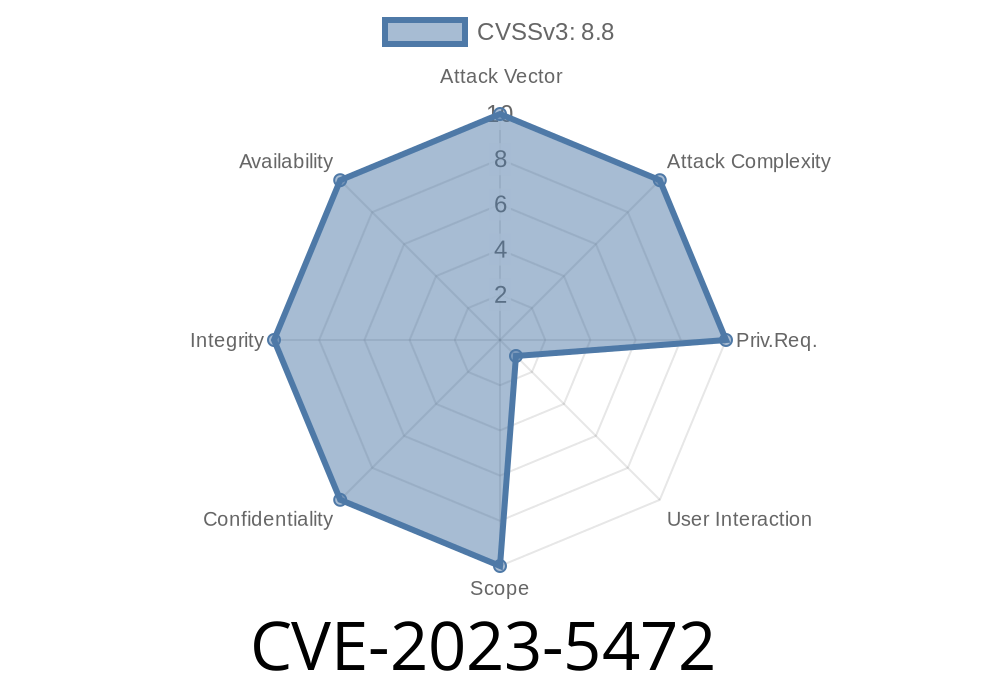
On October 2023, the Chromium security team patched a critical use-after-free vulnerability in Google Chrome’s Profiles system, tracked as CVE-2023-5472. Before Chrome version 118..5993.117, attackers could exploit this flaw using a specially crafted HTML page to corrupt the browser’s memory—and possibly even execute malicious code. This article breaks down what this vulnerability is, how it’s triggered, how attackers could exploit it, and what you can do to stay safe.
What is a Use-After-Free Vulnerability?
A use-after-free is a type of memory bug where a program continues to use a piece of memory after it’s been freed, or returned, to the system. This can result in unpredictable behavior—everything from browser crashes, to memory corruption, to remote code execution in the worst cases.
In browsers like Chrome, use-after-free bugs are especially dangerous because they can be triggered simply by visiting a bad website.
Where Did the Bug Live? (Chrome Profiles)
The bug was found in the Profiles component of Chromium. Chrome manages multiple user profiles (for different users, workspaces, or settings), and a flaw in how Chrome manages the memory for profile objects resulted in this dangerous use-after-free scenario.
Whenever Chrome opens or closes a user profile, behind the scenes, some code should carefully free related memory. If the browser incorrectly accesses this freed memory, attackers can make Chrome operate on memory they already control.
Up to version 117, this flaw was present.
> Link: Chromium Security Advisory for CVE-2023-5472
How Could Attackers Exploit This?
The attacker’s goal is to craft a web page that triggers the use-after-free condition in Chrome’s handling of Profiles objects. Here’s a step-by-step of what that might look like in practice (simplified):
Victim visits malicious page – The page runs JavaScript.
2. JavaScript manipulates Chrome’s profile system: through APIs or edge cases, the script triggers creation and deletion of profile-based objects rapidly.
3. Trigger free/memory release: The bug causes Chrome to release memory while still retaining a reference.
4. Attacker re-allocates freed memory: Malicious JavaScript deliberately allocates new objects, hoping they end up at the same memory as the freed object.
5. Exploit memory corruption: Chrome uses the dangling pointer, putting attacker-controlled data in a “privileged” context. This might let an attacker run arbitrary code—not just crash the browser.
Sample Exploit Snippet
Warning: This code does NOT exploit Chrome and is for educational illustration only. It shows a typical use-after-free pattern in JavaScript.
// Step 1: Trigger profile object creation
let obj = createProfileObject(); // Hypothetical API
// Step 2: Free the object (simulated)
deleteProfile(obj); // Hypothetical buggy function
// Step 3: Allocate attacker-controlled object at same memory
let attackArray = [];
for (let i = ; i < 10000; i++) {
attackArray.push(new ArrayBuffer(1024));
}
// Step 4: Use after free (Chrome tries using obj, but memory's changed)
let leak = useProfileObject(obj); // If Chrome doesn't check, attacker wins!
*Note: Actual exploitation would require deep reverse engineering, knowledge of Chrome’s internals, and bypassing other security mechanisms.*
Real-World Risk: Why Should I Care?
- Remote Attack: An attacker only needs to get you to visit a web page—no downloads or interaction required.
- High Severity: Rated “High” by Chromium. In some cases, this kind of attack leads to full code execution—giving attackers control over your browser or, worse, your device.
- Cross-Platform: Chrome runs on Windows, macOS, Linux—meaning millions were at risk until patched.
Mitigation & Fixes
The Chrome team fixed the bug in version 118..5993.117. All users should make sure Chrome auto-updates are enabled.
Chrome will check for updates automatically.
> Reference: Stable Channel Update for Desktop (Chrome Blog)
Technical References & Further Reading
- Chromium Issue 148653 (Security bug) *(May have limited details for security reasons)*
- Stable Channel Update for Desktop
- Google Project Zero: Use-After-Free Exploitation Primer
Conclusion
CVE-2023-5472 is a textbook example of how a simple memory bug can become a critical browser exploit. If you use Chrome, updating is your best defense. Security researchers and developers should always pay close attention to use-after-free reports—because attackers certainly will!
Stay safe, and always keep your browser up to date!
*Written exclusively for you. Share, but stay sharp—the web never sleeps.*
Timeline
Published on: 10/25/2023 18:17:43 UTC
Last modified on: 11/03/2023 23:15:09 UTC