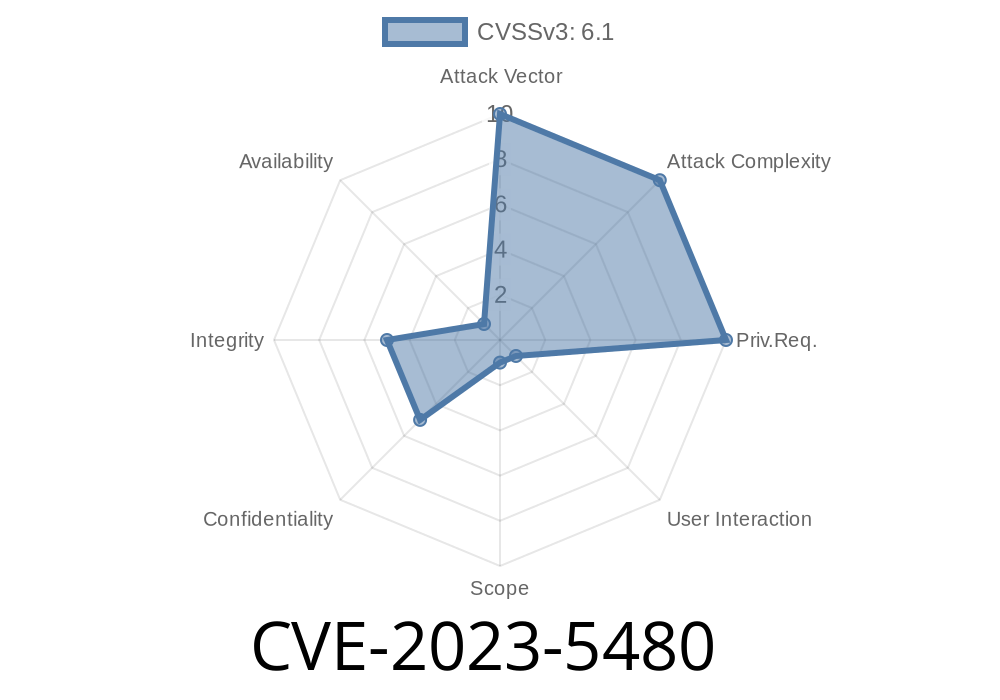
In this article, we'll be discussing an important security flaw identified in Google Chrome's payment implementation system. The vulnerability, officially known as CVE-2023-5480, has been marked as a high-severity issue due to its potential impact on user data. The flaw allows remote attackers to bypass Cross-Site Scripting (XSS) protections by using a malicious file. Before we delve into the technical details, let's get a brief understanding of XSS and how this vulnerability can affect the Chrome payment system.
What is Cross-Site Scripting (XSS)?
Cross-Site Scripting is a type of security vulnerability that enables an attacker to inject malicious scripts into web pages accessed by users. The script's execution occurs within the user's browser and can result in unauthorized access to sensitive information, session hijacking, or even redirecting the user to malicious websites.
Understanding CVE-2023-5480
CVE-2023-5480 revolves around an inappropriate implementation of the payment processing system in Google Chrome versions before 119..6045.105. This vulnerability allows a remote attacker to manipulate payment data using a malicious file and, subsequently, bypass the built-in XSS protections. The problem lies in Chrome's insufficient input validation and lack of proper session handling while processing payment transactions.
Exploit Details
The vulnerability specifically targets the chrome's payment implementation process. An attacker can exploit this issue by crafting a malicious file that Chrome processes during payment transactions. This malicious file can inject harmful scripts into the system, thereby bypassing the XSS protection mechanism.
For instance, consider the following code snippet, which showcases a basic representation of the vulnerability:
// Malicious script injected as a payload
var maliciousScript = "<script>alert('XSS Attack!');</script>";
// The function handling the payment transaction
function processPayment() {
// ... some code omitted for brevity
// Insufficient input validation and improper session handling
var paymentInfo = getPaymentInfo(); // Insecure function that fetches payment info, including the malicious script
// ... more code for payment processing
displayPaymentConfirmation(paymentInfo);
}
The above code demonstrates that when Chrome fetches the payment information, it does not perform adequate input validation or session handling. As a result, the malicious script passes through the processing mechanism and, upon execution, triggers an unexpected action, such as an alert displaying "XSS Attack!".
Mitigation and Fixes
Thankfully, Google Chrome has already addressed this vulnerability with the release of version 119..6045.105, which includes improved input validation and session handling measures. Updating your Google Chrome browser to the latest version will effectively mitigate this vulnerability.
Original References
1. Google Chrome's official changelog discussing the fix: Chrome Releases 119..6045.105
2. The Chromium project's security advisory reporting the issue: CVE-2023-5480 Advisory
Conclusion
CVE-2023-5480 is a high-severity vulnerability that affects Google Chrome's payment implementation. Remote attackers can exploit this security flaw by crafting a malicious file and injecting it into Chrome, effectively bypassing the built-in XSS protection mechanisms. To protect your system and ensure secure payment transactions, it is crucial to keep your Google Chrome browser up to date with the latest security patches and enhancements.
Timeline
Published on: 11/01/2023 18:15:09 UTC
Last modified on: 11/14/2023 03:15:11 UTC