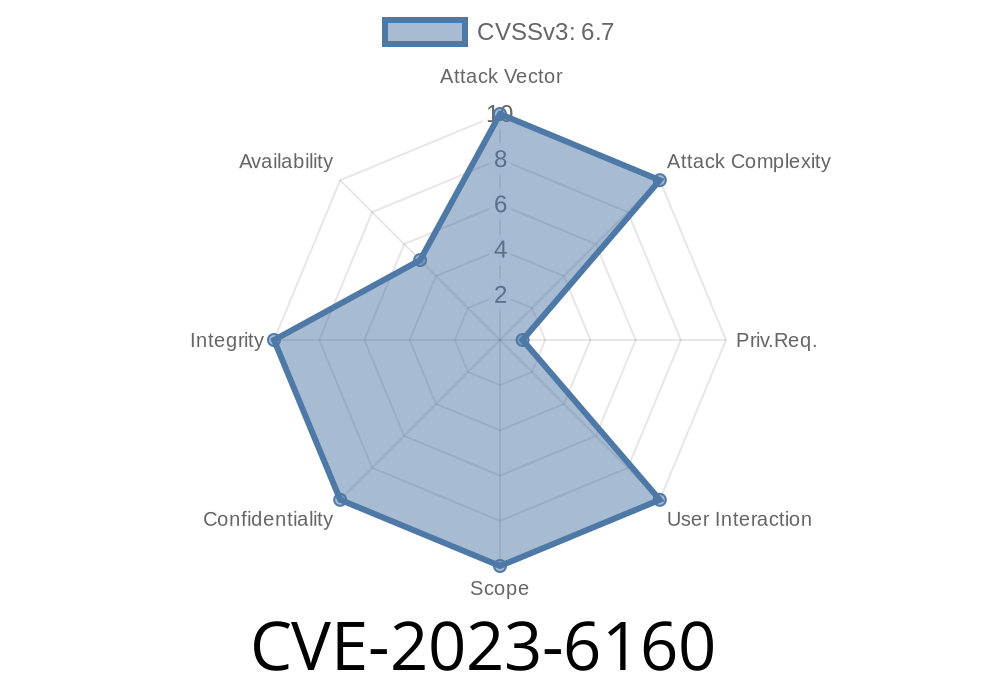
The popular LifterLMS – WordPress LMS Plugin for eLearning has been found to have a security vulnerability affecting versions up to and including 7.4.2. The vulnerability has been identified as a Directory Traversal which can be exploited by authenticated attackers with administrator or LMS manager access. This post will discuss the details of the vulnerability, provide a code snippet, and provide links to the original references.
Vulnerability Details
The vulnerability exists in the maybe_serve_export function of the LifterLMS plugin. Attackers with administrator or LMS manager access can exploit this vulnerability to read the contents of arbitrary CSV files on the server. These CSV files can contain sensitive information like user details, course data, and more. Furthermore, attackers can also remove these files from the server, causing data loss for the website owner.
The Directory Traversal vulnerability is a type of vulnerability that allows an attacker to navigate through the directories on a server, potentially gaining unauthorized access to sensitive information or even modifying or deleting files.
Code Snippet
The following code snippet demonstrates the vulnerability in the maybe_serve_export function of the LifterLMS plugin:
public function maybe_serve_export( $template ) {
$action = isset( $_GET['llms_export'] ) ? $_GET['llms_export'] : '';
$nonce = sanitize_text_field( $_REQUEST['_wpnonce'] );
if ( $action && wp_verify_nonce( $nonce, 'export_' . $action ) ) {
$product_category_slug = sanitize_text_field( $_REQUEST['llms_export_category_slug'] );
$filepath = LLMS_PLUGIN_DIR . 'exports/' . $product_category_slug . '.csv';
if ( file_exists( $filepath ) ) {
header( 'Content-Type: text/csv' );
header( 'Content-Disposition: attachment;filename="' . $product_category_slug . '.csv' . '";' );
header( "Pragma: no-cache" );
header( "Expires: " );
readfile( $filepath );
unlink( $filepath );
exit;
}
}
}
As seen in the code above, the product category slug, which is part of the filepath, is taken directly from the user input without sufficient validation or sanitization. This allows an attacker to modify the filepath to traverse directories on the server and read arbitrary CSV files.
Original References
1. LifterLMS plugin website - https://lifterlms.com/
2. WordPress Plugin Repository - https://wordpress.org/plugins/lifterlms/
3. CVE Details - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-6160
Exploit
To exploit this vulnerability, an attacker with administrator or LMS manager access must send a malicious request with a modified product category slug pointing to an arbitrary CSV file on the server. The server would then respond with the contents of the targeted CSV file.
Mitigation
To mitigate this security issue, users of the LifterLMS – WordPress LMS Plugin should update their plugin to version 7.4.3 or later, which contains a fix for the vulnerability. Additionally, ensure that all user input is properly sanitized and validated to prevent any unauthorized access to sensitive information or files.
Timeline
Published on: 11/22/2023 16:15:15 UTC
Last modified on: 11/29/2023 18:58:52 UTC