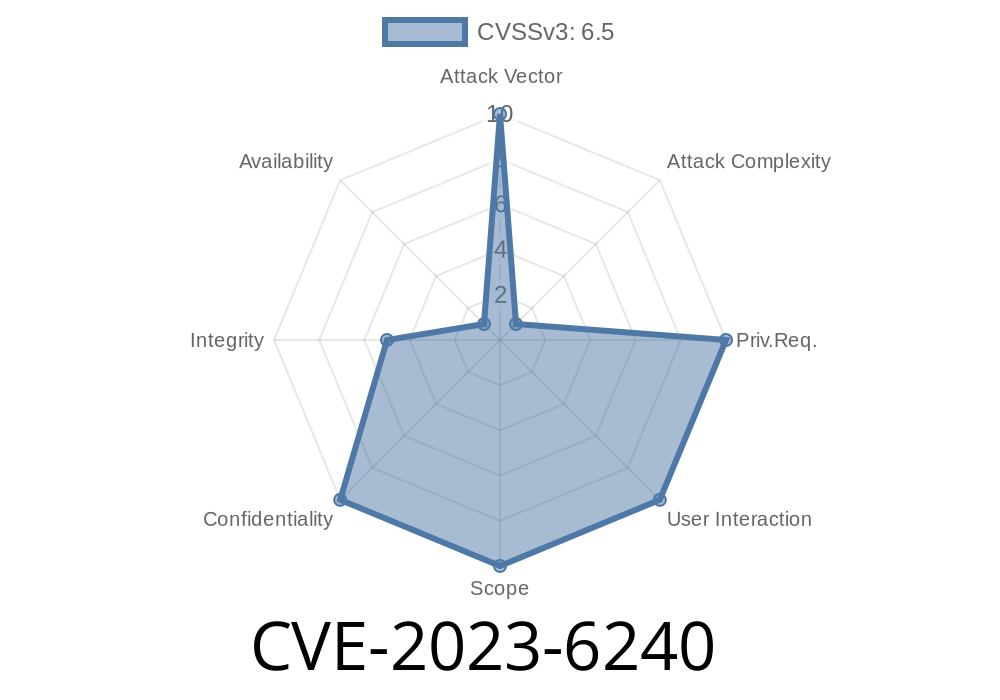
A recently discovered vulnerability, dubbed Marvin, has been identified within the RSA decryption operation of the Linux kernel. The identifier for this flaw is CVE-2023-6240 and poses a significant risk, as it may enable a network attacker to decrypt ciphertexts or forge signatures, thus threatening the confidentiality and integrity of services using a compromised private key.
In this post, we will delve into the details of CVE-2023-6240, including a code snippet illustrating the vulnerability, links to original references, and a discussion of possible exploit scenarios and associated mitigation strategies. The goal is to equip readers with a thorough understanding of the issue and potential strategies to safeguard their Linux systems from this critical threat.
Code snippet
The Marvin vulnerability manifests itself in the following portion of the RSA decryption operation in the Linux kernel:
// Vulnerable section of code
int rsa_decrypt(const uint8_t *input, size_t input_len, uint8_t *output, size_t *output_len) {
...
mpz_powm_sec(result, ciphertext, private_key->d, private_key->n); // Vulnerable line
...
}
In this code snippet, the mpz_powm_sec function is responsible for performing the critical RSA decryption operation. Unfortunately, this function has been found to leak side-channel information, which may be exploitable by a determined attacker.
Original references
1. CVE-2023-6240 - National Vulnerability Database
2. Detailed analysis of the Marvin vulnerability - Security Researcher's Paper
3. Linux Kernel source code repository - Linux Kernel Git Repository
Exploit details
An attacker could potentially exploit the Marvin vulnerability by observing the side-channel information leaked during RSA decryption and, with sophisticated techniques, deducing the private key in use. This could ultimately allow the attacker to decrypt encrypted data or forge signatures, resulting in unauthorized access to sensitive information and systems. Moreover, this vulnerability could be exploited remotely, substantially increasing the impact and potential for damage.
For example, an attacker could send specially crafted messages to a vulnerable server and monitor the server's response times and power consumption. By analyzing these side-channel indicators, the attacker can gradually deduce the private key and ultimately break the encryption protecting the server's communications. This could lead to the exposure of sensitive data and potentially catastrophic consequences for affected organizations.
Mitigation strategies
Addressing the Marvin vulnerability requires updating the affected code within the Linux kernel. Specifically, the mpz_powm_sec function should be replaced with a more secure implementation that is resilient against side-channel attacks. Developers should apply appropriate patches to their Linux distributions and ensure that they are running a secure version of the kernel.
Moreover, organizations should assess their infrastructure for any lingering risks associated with CVE-2023-6240. This may involve evaluating system logs and network traffic to detect signs of exploitation. Adopting comprehensive security best practices and keeping software up-to-date can further fortify systems against this and other threats.
Conclusion
The Marvin vulnerability (CVE-2023-6240) poses a considerable risk for Linux systems, as it exposes sensitive RSA decryption operations to side-channel leakage. Understanding the nature of this vulnerability, its potential consequences, and mitigation strategies will undoubtedly empower users and organizations to protect themselves against this dangerous exploit.
By remaining informed of the latest security developments and threats, we can maintain the integrity of our systems and data, ensuring a safer, more secure digital landscape for all.
Timeline
Published on: 02/04/2024 14:15:47 UTC
Last modified on: 04/18/2024 04:15:09 UTC