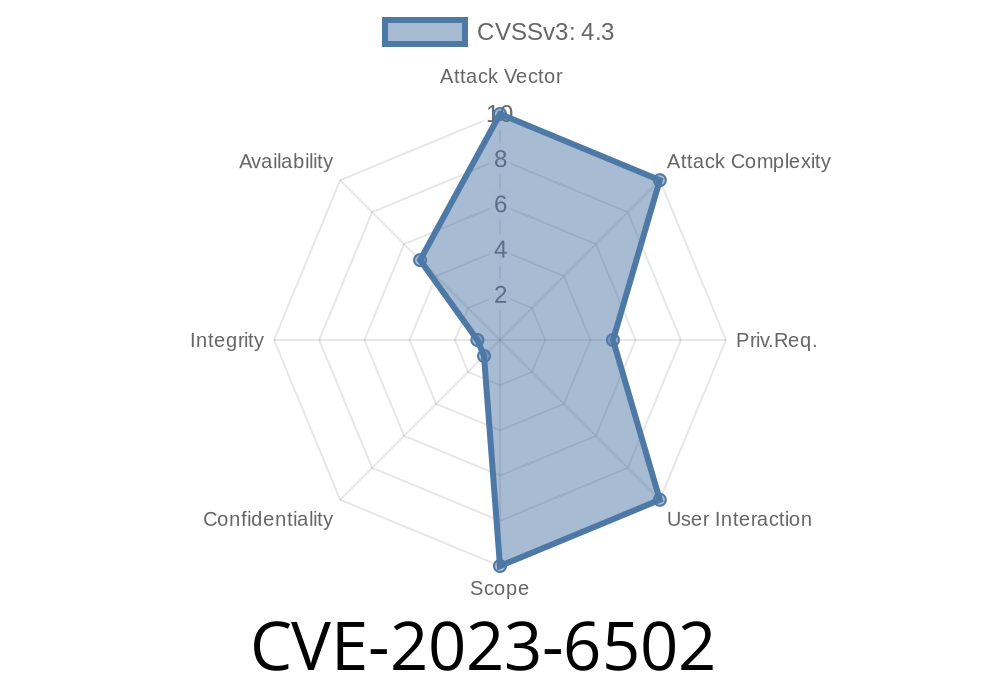
In early 2024, security researchers identified a new vulnerability labeled CVE-2023-6502 that affected several versions of GitLab CE/EE. This flaw opened the door for attackers to take down GitLab servers by simply crafting a nasty wiki page. If your organization relies on GitLab for code projects, CI/CD, or collaboration, you’ll want to pay attention. In this exclusive article, we’ll break down exactly what went wrong, how attackers exploited it, and what you can do to protect yourself.
What is CVE-2023-6502?
CVE-2023-6502 is a Denial of Service (DoS) vulnerability in GitLab CE/EE’s wiki module. Specifically, any version:
What could an attacker do?
An attacker could send a specially crafted wiki page, causing the server to work too hard, crash, or become unresponsive. This takes GitLab offline for everyone—huge headaches for teams that depend on it.
How Did the Vulnerability Happen?
The issue occurred in how GitLab handled user-generated content in wiki pages. The server tried to parse and render any input in the wiki, even if it could tie itself in processing "knots."
Attackers found that by creating certain types of complex or recursive wiki markup, they could cause GitLab’s wiki processor to enter an endless (or very long) loop, using up server resources and eventually bringing the service down.
Exploit Details
Attackers didn’t need special permissions—anyone who could add or edit a wiki page could try to exploit this (although some permissions may depend on project settings).
Example of a Malicious Wiki Page
Below is a simplified version of what an attacker’s malicious wiki page might look like (don’t try this on a production server!):
<!-- A deeply nested, self-referencing markdown snippet -->
{{#repeat:10000}}
* Nested list item
{{#if:1|More nesting!}}
{{/repeat}}
> Note: GitLab wiki supports some template syntax as well as markdown; actual exploits might use more convoluted recursive markup or advanced features.
When GitLab receives this, its wiki processing engine gets bogged down parsing and expanding all the nested/recursive structures. System resources shoot up, and eventually the service times out or goes offline.
Real-World Impact
- System unresponsive: Users can’t push/pull code, review merge requests, or deploy via CI/CD.
- Incident response: Admins must restart services, clear offending content, and patch systems—an annoying and potentially costly distraction.
Steps
1. Read GitLab’s Security Release Announcement
Backup your GitLab instance.
3. Apply the patch/upgrade.
Reference links
- GitLab Data on CVE-2023-6502
- GitLab Security Release Notes
Conclusion
The CVE-2023-6502 vulnerability reminds us that even the friendliest-looking features—like wiki markdown—can become powerful attack tools in the wrong hands. The GitLab team responded quickly, and you should too: always keep your systems up to date, monitor user-generated content, and pay attention to surprise slowdowns that could mean someone is poking at your systems.
Did you find this article useful? Let us know—and always stay patched!
References:
- CVE-2023-6502 NVD Entry
- GitLab Security Blog
Timeline
Published on: 05/23/2024 11:15:22 UTC
Last modified on: 05/24/2024 01:15:30 UTC