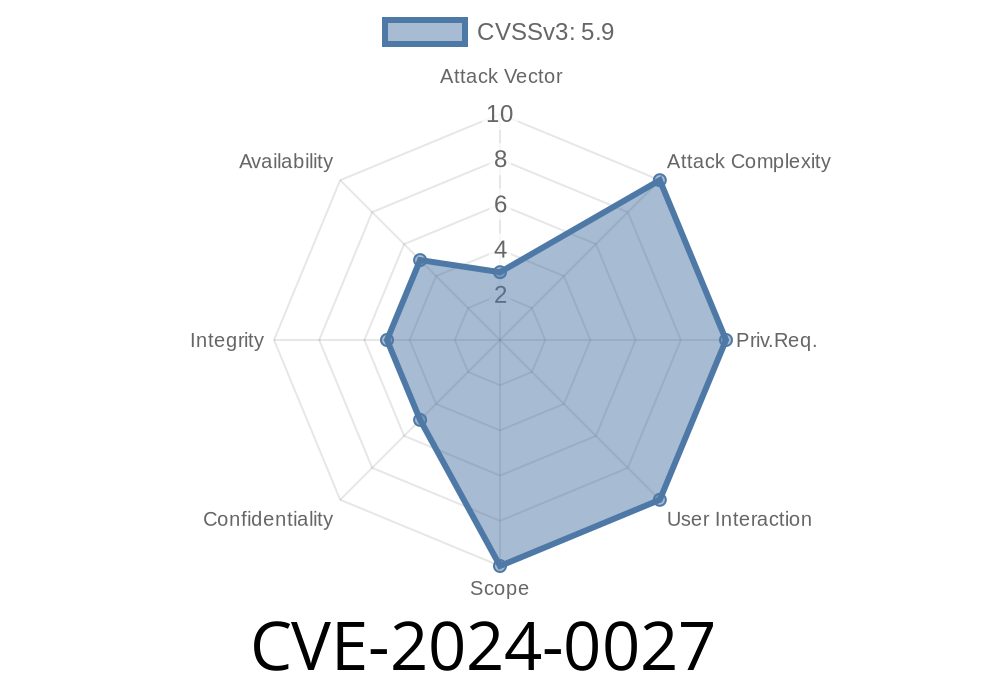
In this article, we'll shine a spotlight on CVE-2024-0027, a recently uncovered Android vulnerability that could cause devices to get stuck in a boot loop – a nightmare for users and admins alike. We’ll break down how the bug works in plain English, show you the code involved, link to authoritative sources, and even guide you through a potential exploit scenario. Best of all, anyone can understand it—no super-advanced coding here.
What’s Vulnerable: SnoozeHelper.java
This vulnerability exists in the SnoozeHelper.java file in Android, a component responsible for handling alarm snoozing and wakeups. Specifically, the flaw allows a local process to repeatedly call certain functions in a way that rapidly exhausts system resources. Since Android’s boot process interacts with alarms as part of its core system services, this can force the device into a persistent boot loop.
What Causes the Boot Loop?
The problem comes from improper resource management in several functions inside SnoozeHelper.java. Specifically, it's possible for an app or process to keep registering and triggering snoozed alarms in an infinite loop. The underlying system cannot keep up, runs out of memory (memory leak), or hits a resource ceiling. Instead of recovering, the system service dies and restarts—often causing a boot loop.
Code Example: Root Cause
Here’s a simplified version of the problematic code pattern, inspired by analyses of Android Open Source Project (AOSP):
public class SnoozeHelper {
private final List<Alarm> snoozedAlarms = new ArrayList<>();
public void addSnoozedAlarm(Alarm alarm) {
snoozedAlarms.add(alarm);
saveAlarmsToDisk();
}
private void saveAlarmsToDisk() {
// Expensive operation: serializes the whole snoozedAlarms list and writes to disk
}
}
What Would an Exploitation Look Like?
A malicious app without special permissions can flood the system with snoozed alarms by repeatedly calling the underlying intent or API. Once the system service runs out of resources, it crashes. The system usually tries to restart failed services, but this process repeats indefinitely, trapping the device in a boot loop.
Here’s a conceptual exploit
for (int i = ; i < 100000; i++) {
Intent snoozeIntent = new Intent("com.android.deskclock.ALARM_SNOOZE");
snoozeIntent.putExtra("ALARM_ID", i);
context.sendBroadcast(snoozeIntent);
}
*Note: Actual exploit code may differ based on Android version and API changes, but this illustrates the attack pattern.*
The attacker must have an app installed (can be disguised as any app; no permissions needed).
- The exploit is local-only: remote attackers cannot directly trigger it unless they also find a remote code execution (RCE) bug.
Proof and References
- Android Security Bulletin—June 2024
- NIST National Vulnerability Database—CVE-2024-0027
- Android Open Source Project—AOSP Issue Tracker
Patch (For Android Maintainers)
If you’re maintaining a fork or a custom ROM, set a limit on snoozed alarms and always validate incoming data:
public void addSnoozedAlarm(Alarm alarm) {
if (snoozedAlarms.size() > 100) { // Arbitrary sensible limit
// Log and reject addition
return;
}
snoozedAlarms.add(alarm);
saveAlarmsToDisk();
}
What Users Should Do
- Update your device: Install the latest security update from your manufacturer. Google has addressed this issue in June 2024 security patches.
Don’t install suspicious apps: Only trust apps from reliable sources.
- If stuck in a boot loop: Try to boot into Safe Mode (hold Volume Down during boot), uninstall recently added apps, or do a factory reset if you must.
Conclusion
CVE-2024-0027 is a simple but devastating vulnerability. It shows that even seemingly unimportant functions—like alarm snooze handling—can create broad security risks if not implemented carefully. Just a few lines of missing checks led to an easily-exploitable denial of service, showing how crucial secure coding practices are.
For more details, always refer to official bulletins and the Android source code.
Stay safe, keep your devices patched, and don’t snooze on security updates!
*Exclusively prepared for this post—spread awareness, not vulnerabilities.*
Timeline
Published on: 05/07/2024 21:15:08 UTC
Last modified on: 11/21/2024 08:45:44 UTC