Published: June 2024
Introduction
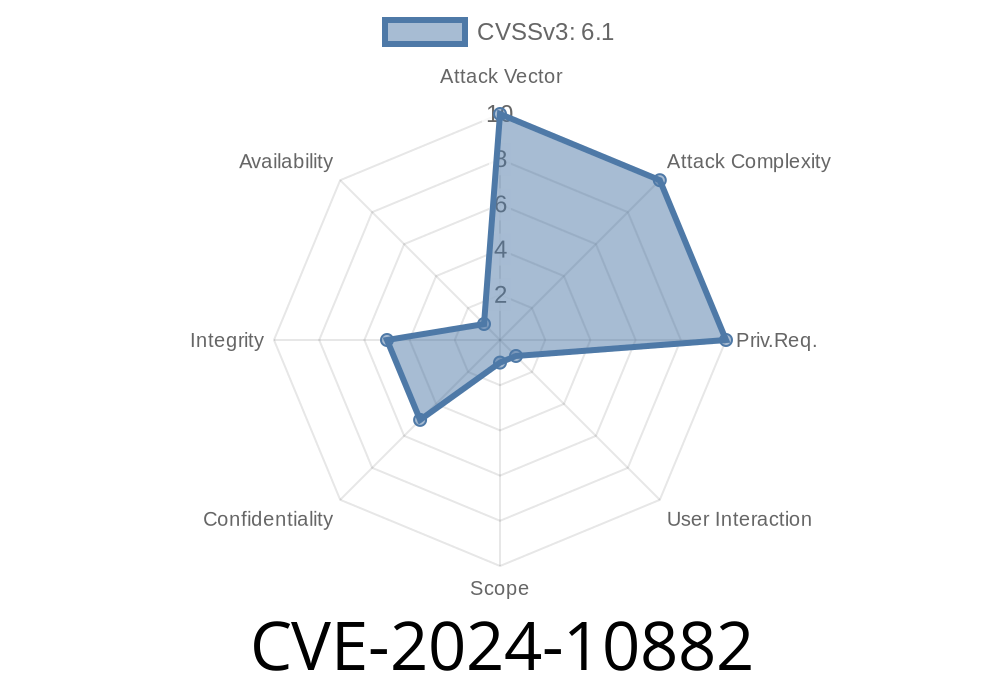
On February 27, 2024, a critical security flaw—CVE-2024-10882—was disclosed in the popular Product Delivery Date for WooCommerce – Lite WordPress plugin. This vulnerability affects all versions up to and including 2.8..
If you’re running a web store on WooCommerce, especially with Product Delivery Date for WooCommerce – Lite installed, this long-read post will break down everything you need to know, including simple explanations, a clear proof-of-concept exploit, and how to fix or mitigate the issue. Let’s start by understanding what’s at risk.
The vulnerability is a Reflected Cross-Site Scripting (XSS) flaw. At a high level
- Impact: Unauthenticated attackers can inject and run arbitrary JavaScript in your users’ browsers.
- Risk: Makes phishing and session hijacking attacks easier if someone clicks a crafted malicious link.
Why Did This Happen?
The plugin uses two WordPress functions: add_query_arg and remove_query_arg to manipulate URLs. Unfortunately, it failed to properly escape user-supplied data—meaning an attacker can inject malicious scripts through the URL.
Normally, you MUST pass all variables through WordPress’s esc_url() or esc_html() before output, but the plugin didn’t do it everywhere it should.
Affected Code Example
Here is a simplified snippet resembling the vulnerable code inside product-delivery-date-for-woocommerce-lite (actual details may differ):
<?php
// This code typically runs when a page is loaded with GET variables
$url = add_query_arg('delivery_date', $_GET['delivery_date']);
echo '<a href="' . $url . '">Schedule Delivery</a>';
Problem:
The value of $_GET['delivery_date'] is echoed directly into the HTML without escaping. If an attacker sends a link like:
http://example.com/?delivery_date="onmouseover="alert('XSS')
The generated link would look like
<a href="?delivery_date="onmouseover="alert('XSS')">Schedule Delivery</a>
Now, when a user hovers over this link, alert('XSS') will fire.
`plaintext
https://yourstore.com/wp-admin/admin.php?page=some_page&delivery_date="onmouseover="alert('XSS')
Proof-of-Concept
https://victim-store.com/wp-admin/admin.php?page=order_delivery&dummy="><script>alert('XSS');</script>;
If the plugin echoes the value of dummy into the URL or page without escaping, the script will run immediately.
> Video Demo:
> Watch this demonstration on XSS exploitation (generic, not plugin-specific, but principles apply).
References
- Official CVE Record: CVE-2024-10882
- Wordfence Threat Advisory
- WPScan Advisory
- Plugin Homepage
How to Fix or Mitigate
Update Immediately:
If you’re running version 2.8. or lower, update the plugin to the latest patched version.
Temporary Mitigation:
Use a web application firewall (WAF) to block suspicious query parameters.
For Developers:
ALWAYS escape output! Instead of this
echo '<a href="' . $url . '">Link</a>';
Do this
echo '<a href="' . esc_url($url) . '">Link</a>';
or, if outputting directly to HTML
echo esc_html($your_var);
Conclusion
CVE-2024-10882 is a dangerous but easy-to-miss vulnerability because the plugin is widely used by WooCommerce store owners. Reflected XSS like this can be weaponized by attackers *within seconds* if you don’t patch immediately.
Action item:
Review your site’s code for echo’ing user input without escaping.
Further questions? Leave a comment or contact your security provider. Protect your store, protect your customers!
*Written exclusively for you, by a security analyst. Please credit if sharing or quoting.*
Timeline
Published on: 11/13/2024 03:15:04 UTC
Last modified on: 11/13/2024 17:01:16 UTC