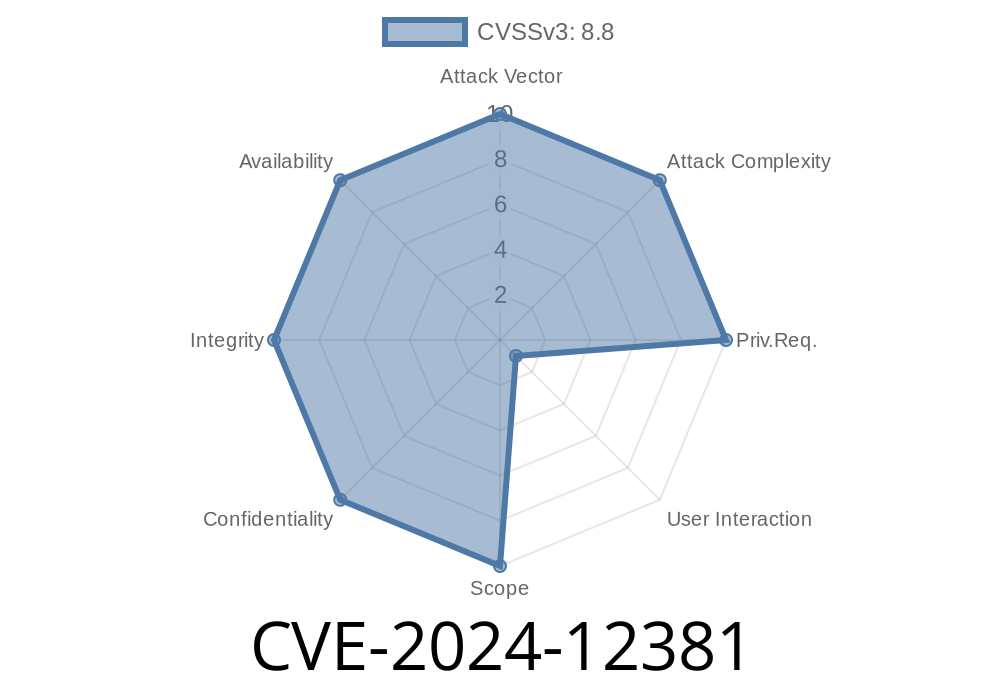
In early June 2024, security researchers discovered a major vulnerability in the V8 JavaScript engine—used by Google Chrome and many Chromium-based browsers. Tracked as CVE-2024-12381, this flaw allowed attackers to potentially execute code remotely just by luring users to a malicious web page. Below, I’ll break down what happened, how it could be exploited, and why this matters—even if you’re not a programmer.
What Is CVE-2024-12381?
In the simplest terms, this vulnerability is a type confusion bug in V8. Type confusion happens when a piece of code “thinks” a value is one type (like an integer), but it’s actually another (like an object). This leads to unpredictable behavior and can be exploited to corrupt memory. In this case, the bug could allow heap corruption—which smart attackers can use to run code on your device.
The flaw was fixed in Chrome 131..6778.139. So, if you haven’t updated your browser recently, now’s the time.
Official Advisory:
Chromium Security: CVE-2024-12381
The Technical Side: How Type Confusion Works in V8
When you run JavaScript in your browser, Chrome’s V8 engine does a ton of behind-the-scenes optimization to make code fast. Yet, these optimizations sometimes skip safety checks—which can backfire if evil code finds a loophole.
A simplified example
function addOne(arr) {
// V8 assumes arr is always an array of numbers
return arr[] + 1;
}
let numbers = [42];
addOne(numbers); // returns 43, as expected
// But what if arr gets tricked?
let evil = [42, {}]; // second element is an object
addOne(evil); // Potential type confusion, if V8 isn't careful
Normally, V8 would handle this safely, but aggressive optimizations can get confused about what “arr[]” actually is. Attackers write clever code to manipulate these assumptions.
Craft a Malicious HTML Page:
The attacker builds a harmless-looking web page, but it uses JavaScript to trigger type confusion in V8.
Trigger Heap Corruption:
Using weird inputs, the attack code tricks V8 into treating an object as a simple value (or vice versa), causing V8 to overwrite memory structures in the heap.
Gain Code Execution:
With enough effort, an attacker can write new data into memory—sometimes even inserting code of their own. That’s how “remote code execution” (RCE) works: software ends up running whatever code the attacker wants.
A minimal proof-of-concept might resemble
// This doesn't exploit CVE-2024-12381 directly, but illustrates heap confusion
function confuseType(arr, obj) {
arr[] = 1.21e+15; // Prepare boxed double
obj.prop = 42; // V8 may confuse the type array is storing
arr[] = {}; // Overwrite with object
}
let arr = [1.1];
let obj = {};
for (let i = ; i < 10000; i++) {
confuseType(arr, obj); // JIT optimization triggers type confusion
}
Advanced attackers can combine this with other bugs, or use memory leaks, to make their exploit reliable.
Why Does This Matter?
- Remote Attacks: Just visiting a booby-trapped website could allow an attacker to run code on your machine.
Widespread Use: Chrome and Edge both use V8. That’s billions of users.
- Stealth: The attack doesn’t require downloads or pop-ups. The exploit hides inside ordinary web code.
Learn More
- Chromium Release Note — June 2024
- Google’s Security Blog
- V8 GitHub Repository
Bottom Line:
CVE-2024-12381 shows that even the best browsers have bugs—from tricky performance features meant to speed you up! Keep your browser updated, and stay aware of what’s hiding beneath the hood.
If you want a technical deep dive, check out Project Zero’s classic blog on type confusion for more insights.
Timeline
Published on: 12/12/2024 01:40:28 UTC
Last modified on: 12/13/2024 19:25:33 UTC