*Last updated: June 2024*
*By WP Security Insights Team*
Introduction
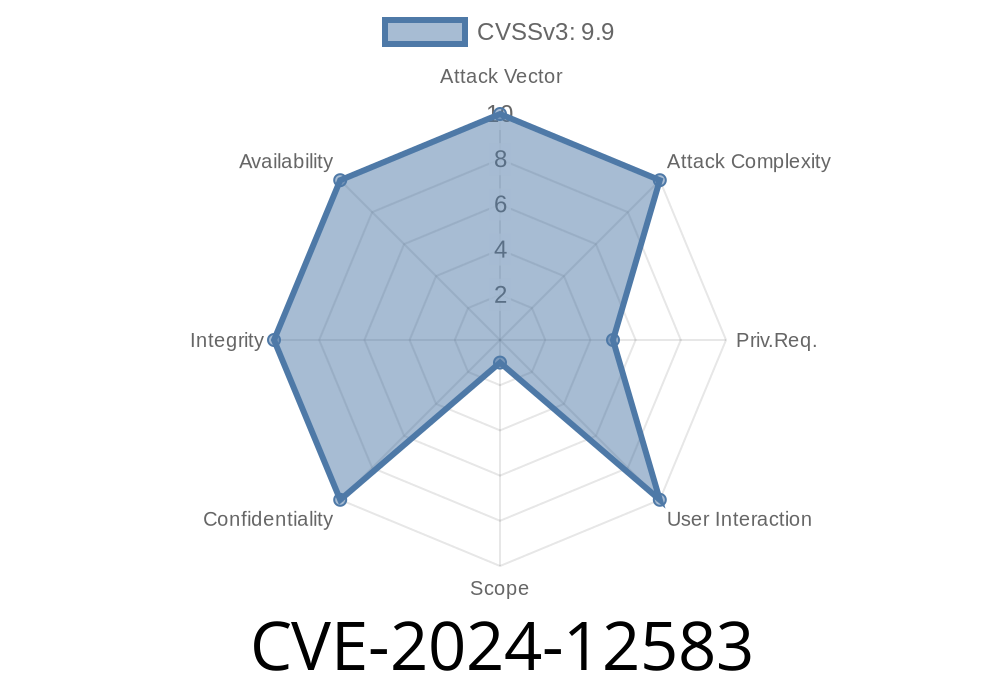
CVE-2024-12583 is a critical vulnerability affecting the widely used Dynamics 365 Integration plugin for WordPress. Attackers can exploit this flaw to read arbitrary files and execute code remotely by abusing the plugin’s integration with the Twig template engine. The root cause is insufficient input sanitization in the plugin's render function. This post will walk you through the vulnerability details, reference original sources, and show proof-of-concept code snippets in clear American English.
Who Is Affected?
Product: Dynamics 365 Integration plugin
Vulnerable Versions: All versions up to and including 1.3.23
Requirements: Authenticated user with at least Contributor access
Where’s the Vulnerability?
The plugin lets users render content using the Twig templating engine. Unfortunately, there’s no check or filter on the input passed to Twig via the render() PHP function. As a result, a trusted but low-privileged user (like a WordPress Contributor) can inject malicious Twig code into templates or shortcodes. Twig interprets these expressions on the server, which leads to a Server-Side Template Injection (SSTI).
Why Is This Dangerous?
- Remote Code Execution (RCE): An attacker can use Twig’s ability to call PHP functions, letting them run arbitrary PHP code.
- Arbitrary File Read: Twig also allows reading local files on the server, which can reveal database credentials, configuration files, or even site backups.
Proof of Concept (PoC)
> Note: Only test this on systems you have permission to audit!
1. Reading Files
Suppose you are a Contributor and can add content with Dynamics 365 Integration shortcodes. Try the following payload in a shortcode block, widget, or custom template:
{{ source('/etc/passwd') }}
What does this do?
This tells Twig to read the contents of the /etc/passwd file (on Linux servers). Replace with wp-config.php to pull sensitive WordPress credentials.
2. Remote Code Execution
Twig’s system function or PHP’s built-in functions (via object chains/CVE chains) can be leveraged for RCE. As a simple direct example:
{{ system('id') }}
If system is not available, use PHP’s object chaining features, like {{ (''|filter('phpinfo')) }} or more sophisticated payloads.
3. Example Exploit Request
Assuming you can submit a post with the plugin’s shortcode, your payload might look like this in WordPress:
[d365_integration_template template="{{ source('wp-config.php') }}"]
When the post is viewed, this template variable is rendered on the server, disclosing the requested file’s contents.
Remediation
- Upgrade: Update the plugin to 1.3.24 or later (see plugin’s changelog).
- Sanitization: The vendor now properly validates/sanitizes fields passed to Twig.
References
- Plugin Vulnerability at Patchstack
- NVD CVE-2024-12583
- WordPress Plugin Directory
Conclusion
CVE-2024-12583 is a perfect demonstration of why unsanitized template rendering is dangerous. If you use this plugin, patch immediately and audit for suspicious templates or posts created by contributors. Encourage your security team to review access controls and monitor for similar template injection bugs elsewhere.
Stay safe, patch often, test responsibly!
*If you found this post helpful, please share it in your security circles.*
Timeline
Published on: 01/04/2025 09:15:06 UTC