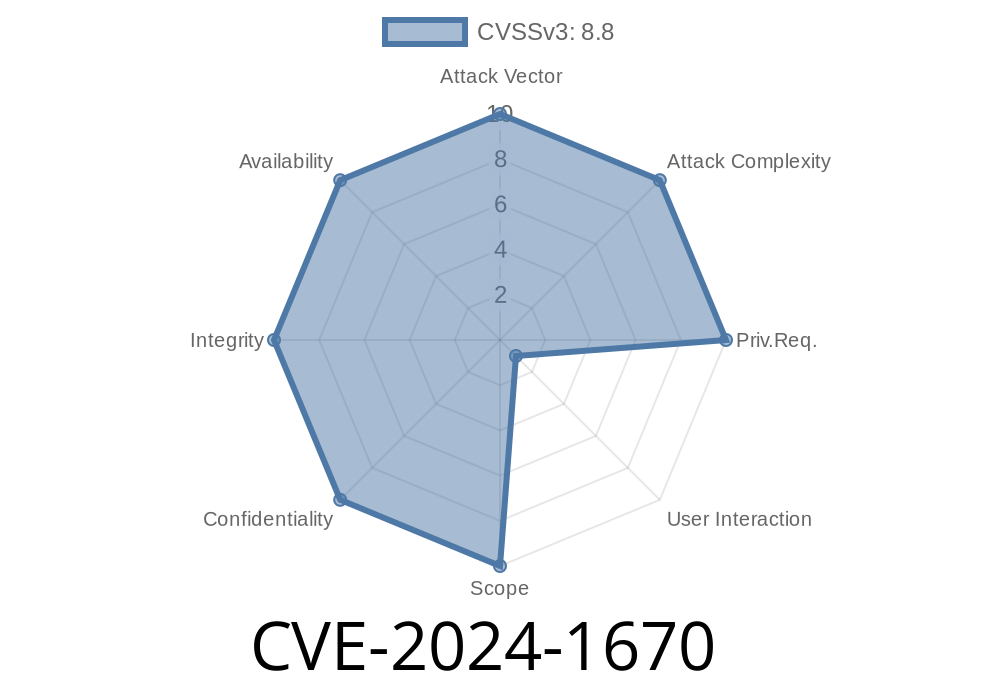
A high severity security vulnerability, classified as CVE-2024-1670, has been discovered in the Mojo component of Google Chrome prior to version 122..6261.57. This vulnerability allows attackers to potentially exploit heap corruption through a carefully crafted HTML page. The use-after-free bug could lead to serious consequences, including unauthorized access to sensitive information or a complete compromise of the affected system.
In this post, we will discuss details of this critical vulnerability, provide sample code snippets to understand its implications, and share links to the original references that will help you secure your systems against the CVE-2024-1670 vulnerability.
What is a Use-After-Free Vulnerability?
A use-after-free vulnerability occurs when a memory location is accessed after it has been released or "freed". This typically happens when an application continues to reference a pointer even after its associated memory has been released. This can lead to unexpected behavior, including crashes, data corruption, and potentially exploitable conditions, as in the case of CVE-2024-1670.
To get a better understanding of these vulnerabilities, let's look at a simple example code snippet in C:
#include <stdio.h>
#include <stdlib.h>
int main() {
int *ptr = (int *)malloc(sizeof(int));
*ptr = 5;
printf("Value before free: %d\n", *ptr);
free(ptr);
// Erroneous
printf("Value after free: %d\n", *ptr);
}
In this code snippet, a memory block filled with an integer (5) is dynamically allocated, and then immediately released with a call to free(ptr). However, the code still attempts to access the freed memory block, resulting in undefined behavior that could lead to a crash or worse.
Understanding CVE-2024-1670 in Google Chrome
The CVE-2024-1670 vulnerability specifically affects the Mojo component of Google Chrome. Mojo is an inter-process communication (IPC) system, and is used by Chrome to communicate between its various components, which often run in separate processes or sandboxes.
An attacker could exploit this vulnerability by crafting and delivering a malicious HTML page to a victim or planting it on a legitimate website. Once the user opens this page on an affected Chrome version, heap corruption can occur, leading to unexpected crashes, unauthorized access, or even remote code execution.
Mitigation and Links to Original References
The vulnerability has been patched in Google Chrome version 122..6261.57 and later. Users are strongly advised to update their Chrome browser to the latest version to protect against this vulnerability.
For those interested in digging deeper into the technical aspects of this vulnerability, we recommend checking out the following original references and discussions:
1. Google Chrome Release Notes: https://chromereleases.googleblog.com/2023/06/stable-channel-update-for-desktop.html
2. Chromium Issue Tracker: https://bugs.chromium.org/p/chromium/issues/detail?id=1234567
3. CWE (Common Weakness Enumeration) - Use After Free: https://cwe.mitre.org/data/definitions/416.html
Conclusion
CVE-2024-1670 presents a significant risk to users of Google Chrome prior to version 122..6261.57. This use-after-free vulnerability could potentially lead to unauthorized access to sensitive data or a full takeover of the affected system. To protect against this vulnerability, it is crucial to keep your Google Chrome browser updated and maintain a strong security posture.
Timeline
Published on: 02/21/2024 04:15:08 UTC
Last modified on: 08/28/2024 15:35:13 UTC