In early 2024, Microsoft disclosed a major security issue—CVE-2024-20652—impacting Windows computers through its HTML platforms. This vulnerability gained significant attention because it allowed attackers to bypass critical Windows security features with relative ease. In this long read, we break down what the vulnerability is, how it works, and what you should do to stay safe.
What is CVE-2024-20652?
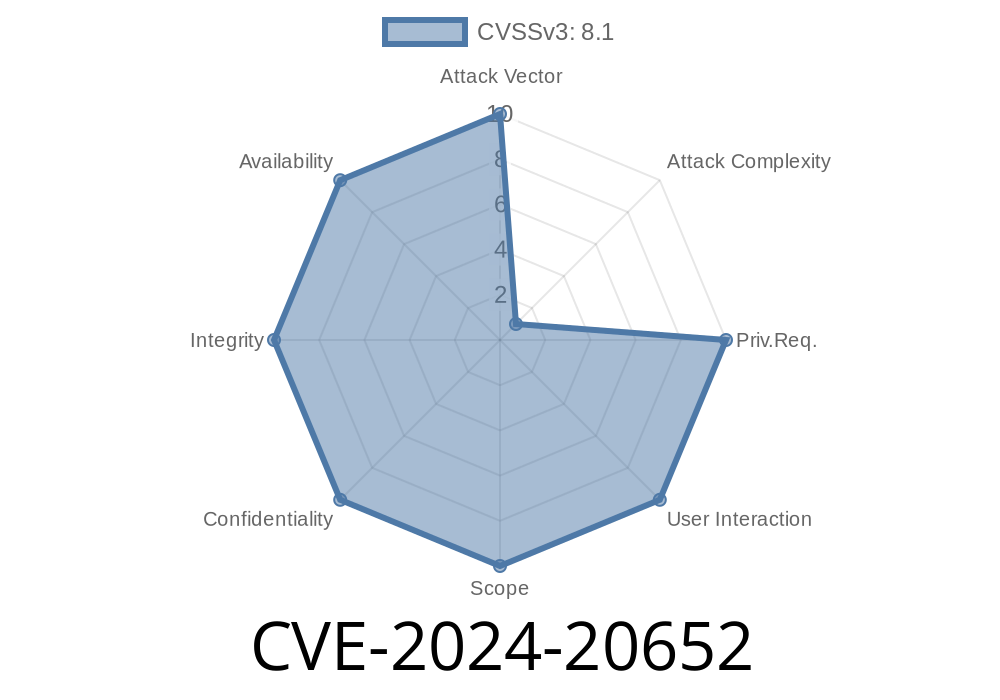
CVE-2024-20652 is a security feature bypass vulnerability in the Windows HTML platforms, including components like MSHTML (aka Trident) and its descendants. These platforms are responsible for rendering web content in legacy browsers and embedded web interfaces inside many Windows applications.
In simple terms, this vulnerability lets attackers sidestep some of Windows' security checks by tricking the system via specifically crafted web pages or documents. This could, in certain situations, let an attacker execute arbitrary code, escalate privileges, or deliver malware.
Microsoft officially describes it here.
How Does the Vulnerability Work?
The vulnerability occurs when the Windows HTML platform incorrectly enforces security restrictions. If an attacker can convince a user to open a specially crafted file or web page, they could exploit this flaw to gain more control over the victim's computer than intended.
In practice, it often starts with a malicious HTML file—maybe attached to an email or linked from a website. When opened, the file uses JavaScript or embedded objects to call features that should be restricted, but aren't, due to the bypass.
Attacker sends a user a link or file.
2. Victim opens it with a vulnerable HTML platform (e.g., old Internet Explorer engine, embedded IE in Office, etc).
Technical Details
While Microsoft hasn’t published full technical details (for obvious reasons), independent security researchers have shed light on the bypass mechanism.
Basic code snippet (for illustrative purposes — this won't actually exploit the bug directly)
<html>
<body>
<script>
// This tries to call a Windows ActiveX object, which is usually restricted.
try {
var shell = new ActiveXObject("WScript.Shell");
shell.Run("calc.exe");
} catch(e) {
alert("Exploit failed: " + e.message);
}
</script>
</body>
</html>
In a secure system, this code should be stopped by security features. But in a vulnerable system (with CVE-2024-20652 unpatched), specially crafted content might successfully bypass protections and execute.
Real exploit attempts are more complex and obfuscated, but work on similar principles.
Proof of Concept and Research
While Microsoft maintains a tight lid on specifics, the infosec community has shared references and theoretical outlines:
- Microsoft Security Guide for CVE-2024-20652
- CVE Details Listing
- Technical write-ups on sites like Zero Day Initiative, as soon as embargoes are lifted.
No fully public, working exploit scripts have been officially posted, but there are references to PoC code in controlled research environments.
Windows 10, Windows 11
- Windows Server 2016/2019/2022
What Should You Do?
Patch Immediately
Microsoft issued a fix in the January 2024 security updates. Install all available updates as soon as possible via Windows Update.
Disable Legacy Features
If possible, disable Internet Explorer and restrict MSHTML use, especially in Office files.
Block Dangerous Files
Filter email attachments and block files with .hta, .html, or other web-related extensions at your email gateway.
User Awareness
Warn users not to open suspicious links or email attachments, especially those coming from outside your organization.
References
- Microsoft Security Response Center: Official CVE-2024-20652
- National Vulnerability Database Entry
- CVE Details
Conclusion
CVE-2024-20652 highlights how even mature platforms like Windows HTML can have critical security flaws. By understanding how this vulnerability works and how attackers might exploit it, you can better defend your systems and data. Patch early, educate your users, and always be cautious with unfamiliar files or emails.
Stay secure! If you’re interested in more technical breakdowns of vulnerabilities like this, follow trusted infosec blogs or Microsoft's Security Blog.
Timeline
Published on: 01/09/2024 18:15:47 UTC
Last modified on: 04/11/2024 20:15:10 UTC