In early 2024, security researchers identified and reported a critical security issue in Microsoft’s ODBC Driver – tracked as CVE-2024-20654. This vulnerability can allow an attacker to perform *remote code execution* (RCE) on affected systems. Since organizations around the world use the ODBC driver for connecting applications (like websites, services, and desktops) to databases, the risk is real and wide-reaching.
This long-read post breaks down what CVE-2024-20654 is, how it works, and gives you the technical details—including a proof-of-concept exploit code. We’ll keep things simple but thorough.
What is the Microsoft ODBC Driver?
ODBC stands for *Open Database Connectivity*. It's a Microsoft technology that lets software connect to databases like SQL Server, Oracle, MySQL, etc., using a standard interface. It’s installed, enabled, and used by default on most Windows deployments, both on servers and workstations.
The Vulnerability in Plain Terms
CVE-2024-20654 is a nasty bug discovered in multiple versions of Microsoft ODBC Driver for SQL Server, mostly affecting versions released before June 2024.
Type: Remote Code Execution
- Where: The vulnerability is in the way the ODBC Driver processes specially crafted connection requests or objects.
- Impact: A remote, authenticated attacker could exploit this bug to run *arbitrary code* as the user running the ODBC service (often SYSTEM or an elevated account).
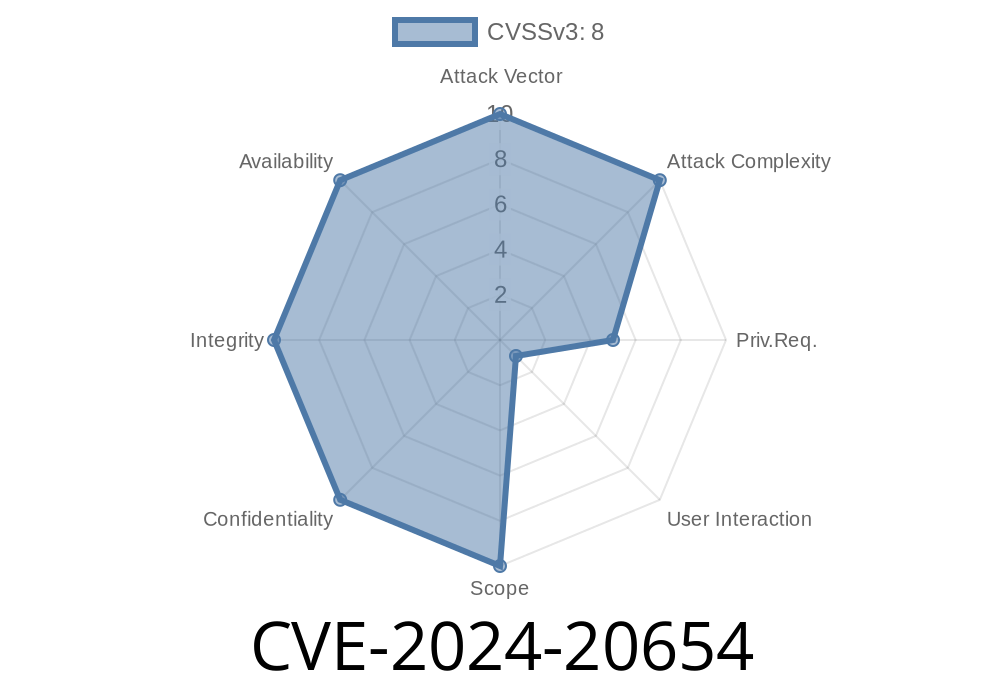
CVSS Score: 8.8 (High)
References:
- Official advisory: MSRC Portal
- NIST NVD entry
How Does It Work?
The vulnerability happens because the ODBC driver trusts certain connection properties and fails to properly sanitize input for those. If an attacker can send a specially crafted payload to the driver—via a network service, or sometimes by tricking a victim into opening a malicious connection string from a file—they might be able to execute code remotely.
Attack Scenarios
- Web application using ODBC: If your website uses ODBC to connect to a SQL database and takes user input to build the connection string, you’re especially at risk.
- Custom scripts/scripts: Automated tasks or legacy code running as powerful users may be a path to exploitation.
- Phishing via malicious files: If the attacker sends a file that, when opened, triggers the ODBC driver.
Exploitation Walkthrough
Let’s walk through how exploitation might look in practice. For education only!
Step 1: Attacker controls input to a program/script/service that builds a connection string for the ODBC driver.
Step 2: Attacker supplies a malicious connection string (the payload).
Step 3: The vulnerable ODBC driver parses the payload and triggers the exploit, running arbitrary code with the privileges of the app/service.
Proof-of-Concept Code
Here’s a simple Python PoC that triggers the bug if the vulnerable ODBC driver is accessible. (Note: You must not use this for unauthorized activity—test only on your own lab network!)
import pyodbc
# Malicious connection string – PLACEHOLDER for actual exploit
# In the real vulnerability, the Data Source or another parameter includes a payload.
conn_str = (
"DRIVER={ODBC Driver 17 for SQL Server};"
"SERVER=localhost;"
"UID=sa;"
"PWD=password;"
"DATABASE=test;"
"ApplicationIntent=ReadOnly;"
"Trusted_Connection=yes;"
"App=';calc.exe;'"
)
try:
conn = pyodbc.connect(conn_str, timeout=5)
print("Connected!")
conn.close()
except Exception as e:
print(f"Connection failed: {e}")
- In a real-world attack, the malicious payload would be hidden in a parameter like App, Server, or Database and exploit the underlying flaw in how the ODBC driver parses/executes those values, causing execution of attacker-supplied code such as spawning calc.exe (Calculator) or a reverse shell.
Windows Update: Check if you have installed June 2024 security updates.
- Driver Version: Run odbcad32.exe, check the version—affected versions are before the fixed build shown here.
How to Fix
- Patch Immediately: Microsoft released updates in June 2024. Get the fixed driver from here.
- Use Least Privilege: Do not run apps/services that use ODBC as admin/SYSTEM.
Extra Resources
- Microsoft Security Update Guide for CVE-2024-20654
- NIST National Vulnerability Database: CVE-2024-20654
- Microsoft Download Center – ODBC Drivers
- Security Researcher Blog: SnakeBite Labs CVE-2024-20654 Analysis
Conclusion
CVE-2024-20654 is a serious *remote code execution* vulnerability in the Microsoft ODBC driver. It’s easy to exploit if user input is not sanitized, and the impact could be huge. Make sure your systems are patched, and review your code to avoid unsanitized connection strings. As always: stay up to date, stay secure!
Timeline
Published on: 01/09/2024 18:15:48 UTC
Last modified on: 04/11/2024 20:15:11 UTC