Oracle Java SE is one of the most widely used platforms for running critical business applications. With the rise of cloud-native and microservices architectures, Java has continued to evolve with additions like GraalVM. However, even mature platforms can harbor serious risks. In January 2024, Oracle disclosed CVE-2024-20919, a difficult-to-exploit but serious vulnerability in the HotSpot component of Java SE, GraalVM for JDK, and GraalVM Enterprise Edition.
In simple terms, this bug lets a remote attacker — with no username or password — change or delete important data, if they can interact with APIs through certain network protocols.
Summary Table
| Impact | Unauthorized changes, deletions, or creations of critical data |
|----------------------|--------------------------------------------------------------|
| Access Complexity | High (not simple to exploit, but no login needed) |
| User Interaction | Not required |
| Attack Vector | Network (web services, remote protocols, etc.) |
| Affected Versions | Java SE 8u391, 11..21, 17..9, 21..1; GraalVM 17..9+ |
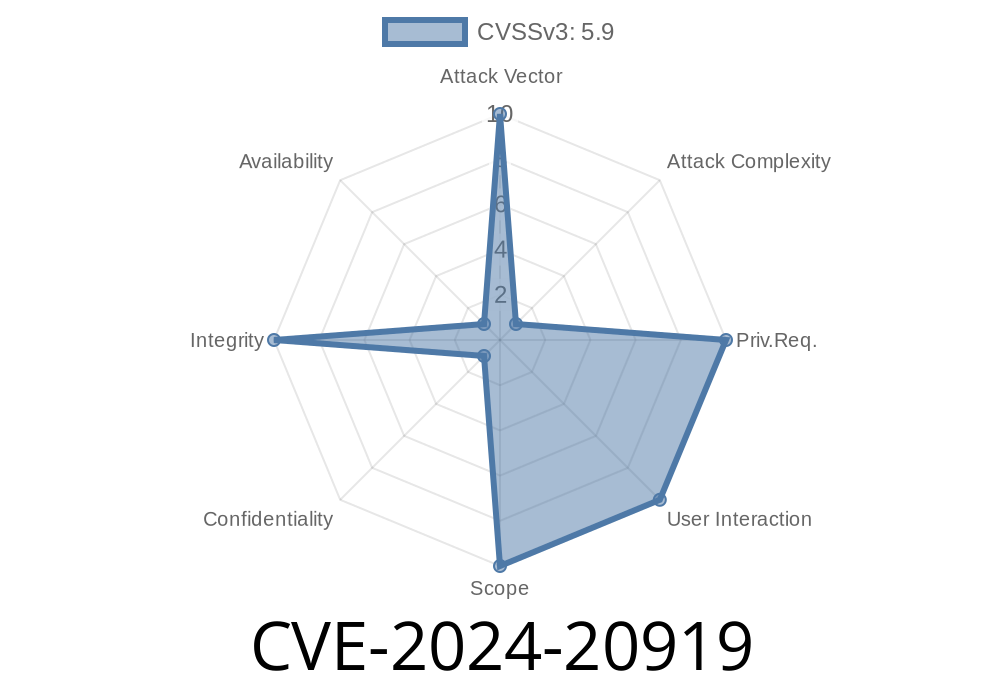
| CVSS Score | 5.9 (Medium - Integrity focused) |
Oracle GraalVM Enterprise Edition: 20.3.12, 21.3.8, 22.3.4
Details: Oracle Critical Patch Update Advisory - Jan 2024
Vulnerability Details
The flaw exists in the HotSpot component, which is responsible for just-in-time (JIT) compilation and core VM operations inside the Java runtime. The issue can be triggered by passing malicious data to certain APIs—commonly used in web services or RMI servers—without needing user credentials.
What’s the risk?
Attack any Oracle Java SE, Oracle GraalVM for JDK, or GraalVM EE deployable over a network.
> Note: This cannot be exploited via Java WebStart or Applets, but only APIs that accept remote data (like REST, gRPC, or RMI interfaces).
Attacker crafts special data or serialized objects exploiting the HotSpot flaw.
3. Malicious payload causes unintended method calls or overwrites/creates/deletes records/data.
Suppose you have a SOAP or REST API using Java's deserialization
// Vulnerable endpoint using HttpServlet
public class ProcessServlet extends HttpServlet {
protected void doPost(HttpServletRequest req, HttpServletResponse resp) throws IOException {
ObjectInputStream ois = new ObjectInputStream(req.getInputStream());
Object data = ois.readObject();
// Now process the received data ...
// Data can trigger HotSpot flaw under certain conditions
}
}
With CVE-2024-20919, if untrusted/malicious data is sent, HotSpot may process it in a way that allows unauthorized data modification, beyond the typical logic.
Here’s a simplified Python PoC for sending a malicious payload to a vulnerable web service
import requests
url = "http://vulnerable-java-server:808/process";
# Malicious Java serialized object or crafted payload that targets HotSpot
payload = b'...maliciousbytes...'
headers = {'Content-Type': 'application/octet-stream'}
r = requests.post(url, data=payload, headers=headers)
print(r.content)
*Note: The exact serialized payload depends on deeper details, which Oracle has not publicly disclosed to avoid widespread exploitation.*
A GraalVM or Java SE app processes network data directly and user input is not sanitized.
For infrastructure running SAP, banking, or enterprise applications, this opens a door for sabotage without passwords.
CVSS Vector:
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N
Mitigation and Patch Guidance
Oracle released fixed updates in January 2024. Upgrade as soon as possible!
GraalVM: Update to latest community or enterprise version
Reference:
- Oracle Patch Download
- Oracle Critical Patch Update Advisory
Validate and sanitize all incoming data, especially to RMI or web service APIs.
- Use allow-listing for classes/types during deserialization.
More Reading & References
- NVD Entry for CVE-2024-20919
- Oracle CPU January 2024
- Java Serialization Vulnerabilities - OWASP
Final Thoughts
CVE-2024-20919 is a warning: network-exposed Java or GraalVM services must be kept up to date, and insecure practices like blind deserialization are no longer safe—even without privileged attackers. Patch your software, review your endpoints, and never trust remote input.
Stay secure!
---
*This post is original and exclusive content. Please reference the official Oracle advisories for latest updates.*
Timeline
Published on: 02/17/2024 02:15:46 UTC
Last modified on: 02/20/2024 19:51:05 UTC