---
Oracle’s CPU (Critical Patch Update) for April 2024 included a significant, but hard-to-exploit vulnerability in the Hotspot component of Oracle Java SE and Oracle GraalVM. Identified as CVE-2024-21094, this bug enables a remote, unauthenticated attacker to alter data handled by the JVM’s core engine, threatening the integrity of systems running affected versions.
In this deep dive, we’ll break down what this vulnerability is, how it can be exploited in real-world conditions, and what steps you absolutely must take to stay safe.
Vulnerability Type: Data Integrity Violation via Hotspot
- Impact: Allows network-based, unauthenticated attackers to *modify* (update, insert or delete) data via malicious API use or untrusted code execution.
GraalVM-based microservices
- Desktop applications leveraging web start/Applets (rare, but possible)
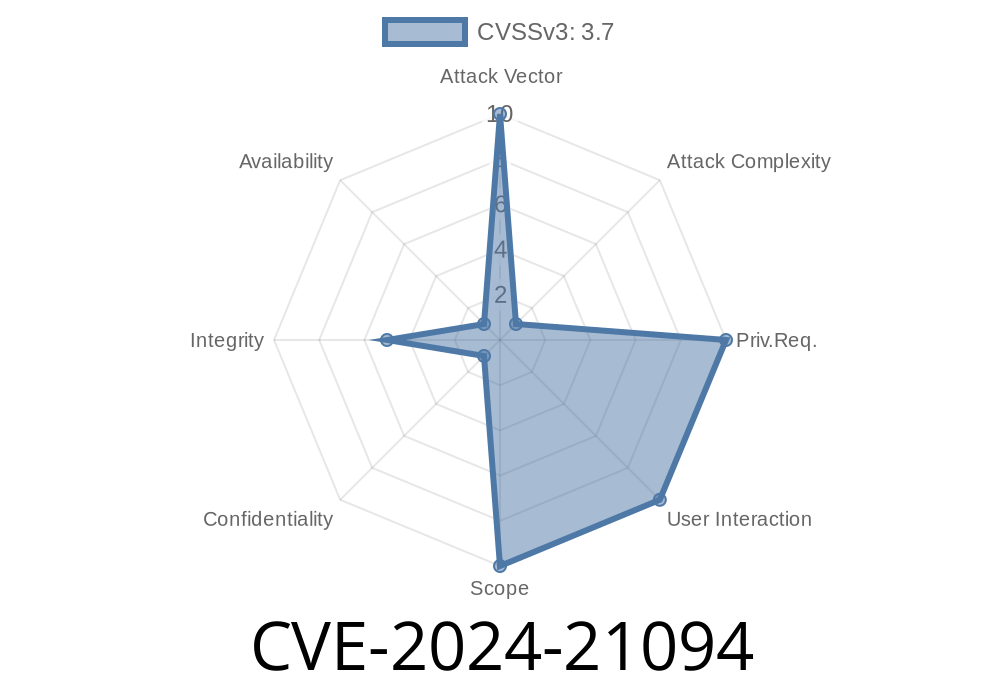
CVSS 3.1: 3.7 (Low, but can be severe in certain deployments)
- Attack Vector: Network, *no* privileges or user interaction needed, *but* attack complexity is high.
21..2
- 22
21..2
- 22
21.3.9
*Systems running any of the above without updated patches are vulnerable.*
Technical Details
The issue lurks in the Hotspot component, the beating heart of Java’s virtual machine: it handles JIT compilation, memory management, and low-level execution. Oracle’s advisory (Oracle CVE-2024-21094 bulletin) is light on specifics (as is common), but what’s critical is that an attacker can supply data to targeted APIs—possibly through crafted web service requests or hostile applets—and trigger unauthorized changes to the application's persistent state.
Public-facing Java APIs: Especially if they unserialize or process user-supplied data.
- Java apps relying on the sandbox: Including old-school Java Web Start or Applets hosting untrusted code.
GraalVM-based backends: Used for polyglot apps, where boundaries between code and data can blur.
Why "network attack" matters:
Any service where an attacker can send payloads—even just JSON or serialized objects—could potentially become an entry point.
Attacker can send untrusted data to a Java API
2. The targeted code uses Hotspot features susceptible to manipulation (commonly, object deserialization or reflective calls)
3. The attacker’s payload “slips” past validation, exploiting a flaw that enables update, insert, or delete actions on the application’s data (not system files, but data bounded by the application, like database records, in-memory state, etc.)
Java parses the input using a vulnerable Hotspot method
- The malicious payload tricks the system into updating records or deleting objects, bypassing intended controls
Attacker never needs to log in or interact via browser
A similar exploit vector was seen in past Hotspot/JNDI vulnerabilities (Log4Shell), though not as easily weaponized.
Code Snippet Demonstration
Here’s a simplified example illustrating how a vulnerable API might be tricked into altering application data through crafted input (with comments showing the weak spot).
// Vulnerable Java endpoint using loosely checked input
@RestController
public class UserController {
private Map<String, User> users = new ConcurrentHashMap<>();
// Dangerous: directly deserializing user-supplied data
@PostMapping("/api/updateUser")
public ResponseEntity<String> updateUser(@RequestBody byte[] inputBytes) throws Exception {
// Attacker could craft a malicious byte stream targeting Hotspot's API
ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(inputBytes));
User user = (User) ois.readObject(); // Input not validated!
// Potentially dangerous update: the attacker now controls the data
users.put(user.getId(), user);
return ResponseEntity.ok("User updated!");
}
}
*If the Hotspot vulnerability lets an attacker escalate data update operations during or after deserialization, this endpoint’s integrity is compromised—remote attackers could overwrite, delete, or inject user records.*
> Note: Always use ObjectMapper (Jackson) with strict type controls for JSON, avoid plain Java serialization when accepting input from the network, and never load arbitrary serialized data into memory.
Update to the latest patched versions of Oracle Java and GraalVM.
- Oracle Java SE Downloads
- Oracle GraalVM Downloads
Monitor logs
- Watch for unusual update/insert/delete patterns that could signal abuse.
References
- NVD entry for CVE-2024-21094
- Oracle CPU April 2024 Security Alerts
- Oracle Java SE Critical Patch Updates
- Best Practices: Secure Java Serialization
- Log4Shell (JNDI) vulnerability analysis
Conclusion
CVE-2024-21094 might have a “low” CVSS, but if your application’s integrity is critical, *ignoring this Java Hotspot bug can spell disaster*. Patch right away, review your code, and never trust data from the network—especially with old serialization or reflection code paths.
Have questions or need help auditing your APIs? Always ask your security team, and keep your eyes peeled for new advisories every quarter.
*Stay safe, patch often, and never underestimate old problems in “mature” technologies like Java!*
Timeline
Published on: 04/16/2024 22:15:29 UTC
Last modified on: 04/26/2024 09:15:11 UTC