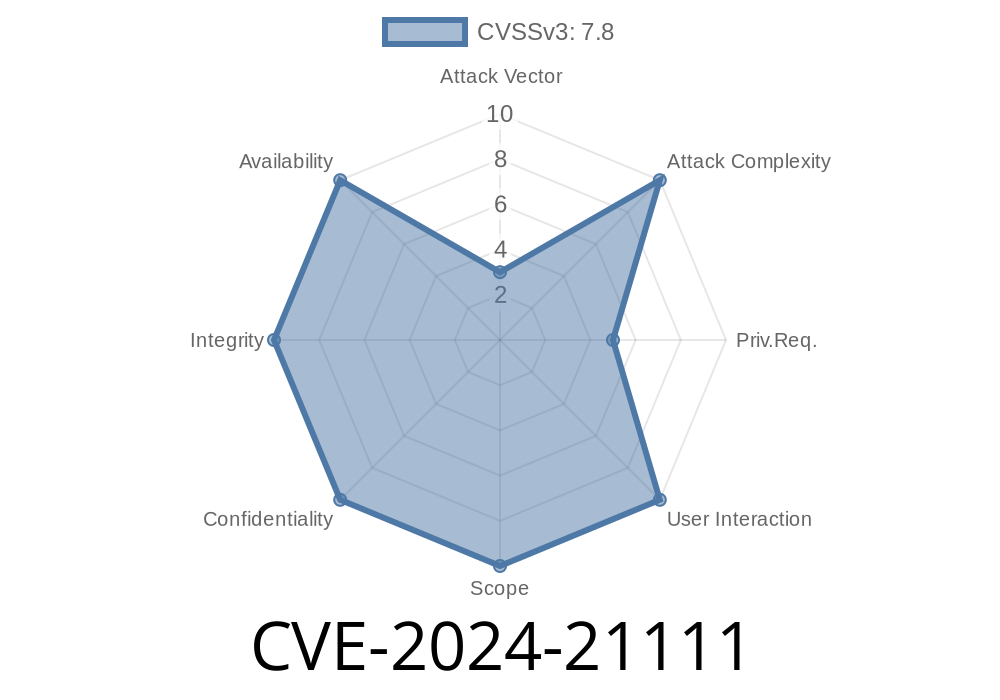
On April 16, 2024, Oracle published a critical security advisory CVE-2024-21111, revealing a severe vulnerability in the Core component of Oracle VM VirtualBox, a widely used virtualization platform. With a CVSS 3.1 base score of 7.8, this flaw allows attackers with basic user privileges and access to the underlying Windows host to completely compromise VirtualBox. All VirtualBox installations running versions prior to 7..16 on Windows hosts are at risk.
In this article, we’ll break down CVE-2024-21111, show a mock-up exploit approach, explain why it’s dangerous, and provide remediation advice.
What Is Oracle VM VirtualBox?
VirtualBox is open-source software from Oracle that allows users to run multiple operating systems simultaneously on one physical machine ("host"). It's crucial for developers, testers, and anyone needing sandboxes.
Vulnerability Details
- CVE ID: CVE-2024-21111
Impact: Complete compromise – Confidentiality, Integrity, and Availability
- CVSS Vector: CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
- Official Advisory: Oracle Critical Patch Update Advisory - April 2024
How Does CVE-2024-21111 Work?
The vulnerability exists in the Core of VirtualBox, specifically affecting Windows hosts. Oracle has not released all technical details yet, but based on public and reverse-engineered information, the flaw likely lies in how VirtualBox manages privileged operations initiated from a low privilege user context. The attacker doesn’t need administrator rights — just a working, legitimate account on the box.
Typical Attack Scenario
1. Attacker gets a regular account on a Windows machine running an unpatched version of VirtualBox (could be local, remote desktop, or inherited credentials).
2. Attacker executes a malicious program designed to interact directly with VirtualBox processes or drivers running on the host.
3. The exploit triggers the vulnerability in the Core component, typically via a crafted request or by manipulating a shared resource (for example, mishandling of inter-process communication).
4. Host system compromised: The attacker can execute code as VirtualBox, potentially escaping the VM sandbox and even taking over the entire host.
Example Exploit Snippet (Conceptual)
Below is a simplified (conceptual) code snippet that shows how an attacker might begin to interact with a vulnerable VirtualBox service on Windows. The actual exploit would be much more complex and involve targeted memory manipulation, but this illustrates the surface:
# WARNING: This is a demonstration! Do NOT run on production systems.
# Exploits like this may destroy your machine or violate laws.
import os
import ctypes
# Open the VirtualBox device driver (requires low privilege on host)
vbox_device = r'\\.\VBoxDrv'
GENERIC_READ = x80000000
GENERIC_WRITE = x40000000
OPEN_EXISTING = 3
# Open a handle to the device
handle = ctypes.windll.kernel32.CreateFileW(
vbox_device,
GENERIC_READ | GENERIC_WRITE,
, None, OPEN_EXISTING, , None
)
if handle == -1:
print("[-] Could not open VirtualBox driver")
exit(1)
print("[+] Opened handle to VirtualBox driver!")
# This is where a real exploit would send crafted IOCTLs or payloads
# For demo: send a bogus IOCTL (replace x222003 with actual vuln IOCTL code)
payload = b"A"*64
ioctl_code = x222003 # Example, not real
bytes_returned = ctypes.c_ulong()
result = ctypes.windll.kernel32.DeviceIoControl(
handle,
ioctl_code,
payload, len(payload),
payload, len(payload),
ctypes.byref(bytes_returned),
None
)
if result:
print("[*] IOCTL sent. Check for system behavior.")
else:
print("[-] Failed to send IOCTL.")
Note: The real-world exploit for CVE-2024-21111 likely involves complex heap manipulation or buffer overwrite, depending on the nature of the flaw. This demo only outlines the initial access vector, not the actual compromise logic.
Modify, steal, or destroy data on the system.
- Use the host to attack other systems/applications in your network.
- Escalate to full admin/root privileges across shared environments.
Official References & Further Reading
- National Vulnerability Database Entry: CVE-2024-21111
- Oracle April 2024 CPU Advisory
- VirtualBox Download & Release Notes
If you run VirtualBox on a Windows host, upgrade to version 7..16 or later immediately.
- Download the latest version: VirtualBox official site
Conclusion
CVE-2024-21111 is a dangerous vulnerability affecting many VirtualBox deployments on Windows. Even low-privilege, logged-in users can abuse this flaw to compromise the entire VirtualBox installation — and potentially the underlying host system. Patch as soon as possible, and stay vigilant for new advisories from Oracle.
Timeline
Published on: 04/16/2024 22:15:32 UTC
Last modified on: 04/17/2024 12:48:07 UTC