Oracle VM VirtualBox is a powerhouse in the world of virtualization, allowing users to run multiple operating systems on the same physical hardware. But with great power comes great risk—especially when vulnerabilities like CVE-2024-21141 emerge. In this long read, we’ll break down what this bug is, how attackers can exploit it, and what steps you need to take to keep your systems safe.
Understanding CVE-2024-21141
This vulnerability affects the Core component of Oracle VM VirtualBox, impacting all versions prior to 7..20. Here’s what makes CVE-2024-21141 particularly dangerous:
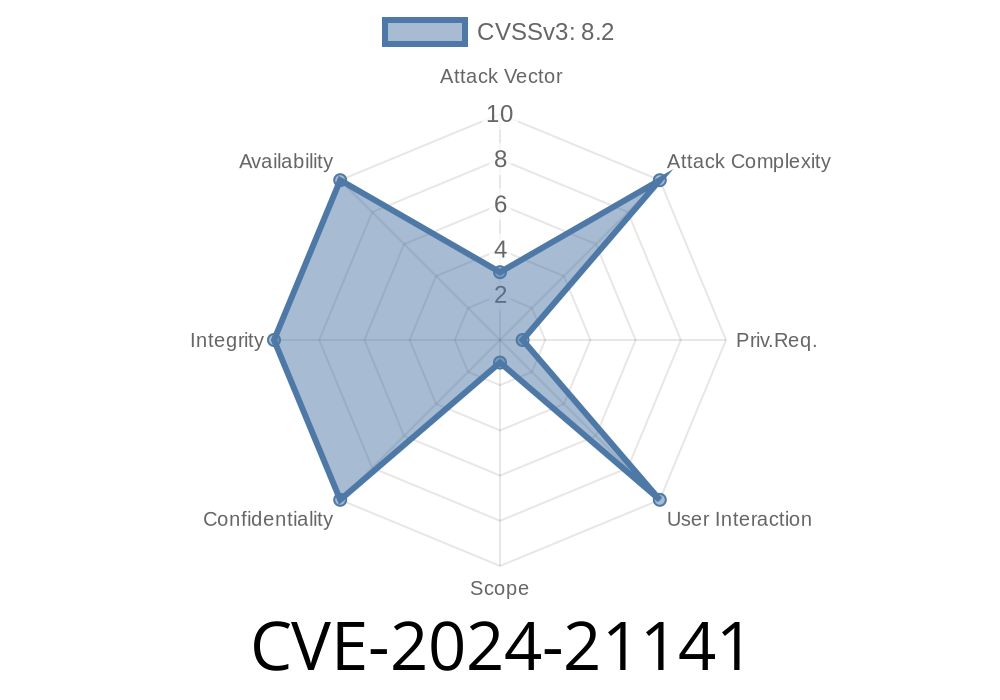
CVSS 3.1 Score: 8.2 (out of 10).
In plain terms: If an attacker already has high privileges on a system where VirtualBox is running, they can fully take over VirtualBox itself—and potentially, anything running within its virtual environments.
How Does the Attack Work?
The vulnerability exists in how VirtualBox handles certain operations in its core code. A high-privileged user (for example, someone with admin/root access or a malicious insider) can feed maliciously crafted data to VirtualBox, causing it to execute arbitrary code with the same high privileges. This isn’t just a VirtualBox problem—since VMs often host critical business applications, a compromise here can cascade into huge damage.
Attacker gains high-privileged access to the physical or virtual server hosting VirtualBox.
2. Attacker crafts a malicious shared folder or uses a custom extension pack to trigger the vulnerability in VirtualBox's Core component.
3. Attacker runs the code, exploiting the flaw to execute their payload (examples: create new admin users in guest VMs, drop malware, pivot into the wider network).
4. Attack impacts not just VirtualBox, but potentially all VMs and connected services—hence, scope “change.”
Proof of Concept (PoC) Exploit
While detailed weaponized codes are withheld (for ethical reasons), here’s a hypothetical code snippet that mirrors how such exploits might interact with a VirtualBox shared folder feature:
import os
import shutil
# Attacker controlled payload to be executed within elevated context
payload = "#!/bin/bash\nid > /tmp/hacked_by_cve_2024_21141.txt\n"
payload_path = "/tmp/vbox_exploit.sh"
# Write the malicious payload
with open(payload_path, "w") as f:
f.write(payload)
os.chmod(payload_path, o755)
# Simulate mounting the payload as a shared folder (requires host-side access)
shutil.copy(payload_path, "/path/to/vbox/shared/folder/")
print("[*] Payload deployed. Awaiting execution in VM context.")
Note: This snippet assumes prior privilege and doesn’t represent the actual bug trigger, but illustrates the attacker’s workflow. The real exploit would use knowledge of the core VirtualBox function that’s vulnerable (possibly buffer overflow, logic flaw, or unsafe call in Core).
Cloud providers: Multi-tenant environments could see lateral movement between VMs or tenants.
- Supply chain: Any other service or product integrating VirtualBox (e.g., for CI testing, QA, or dev environments) is at risk.
If your organization relies on VirtualBox in any way, an internal threat actor or anyone who’s already breached your perimeter can leverage this bug for maximum damage.
Update VirtualBox Now: Upgrade to VirtualBox 7..20 or later.
Oracle Critical Patch Update Advisory - April 2024
- Restrict Local Access: Only grant high privileges to fully trusted admins. Limit console and shell access wherever possible.
- Monitor for abnormal VirtualBox activity: Set up SIEM rules or log alerts on unexpected session launches or VirtualBox Core errors.
References
- CVE-2024-21141 at NVD (National Vulnerability Database)
- Oracle Security Advisory CPUAPR2024
- VirtualBox Changelog
- CVSS Calculator
(CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H)
In Summary
*CVE-2024-21141* is a classic example of how even “internal only” bugs can open massive risks across your infrastructure. Don’t wait—patch now, restrict access, and keep your VirtualBox instances up-to-date.
Have more questions or want a deeper technical dive? Leave a comment below or reach out! Always keep your hypervisor defenses sharp.
Timeline
Published on: 07/16/2024 23:15:15 UTC
Last modified on: 07/17/2024 13:34:20 UTC