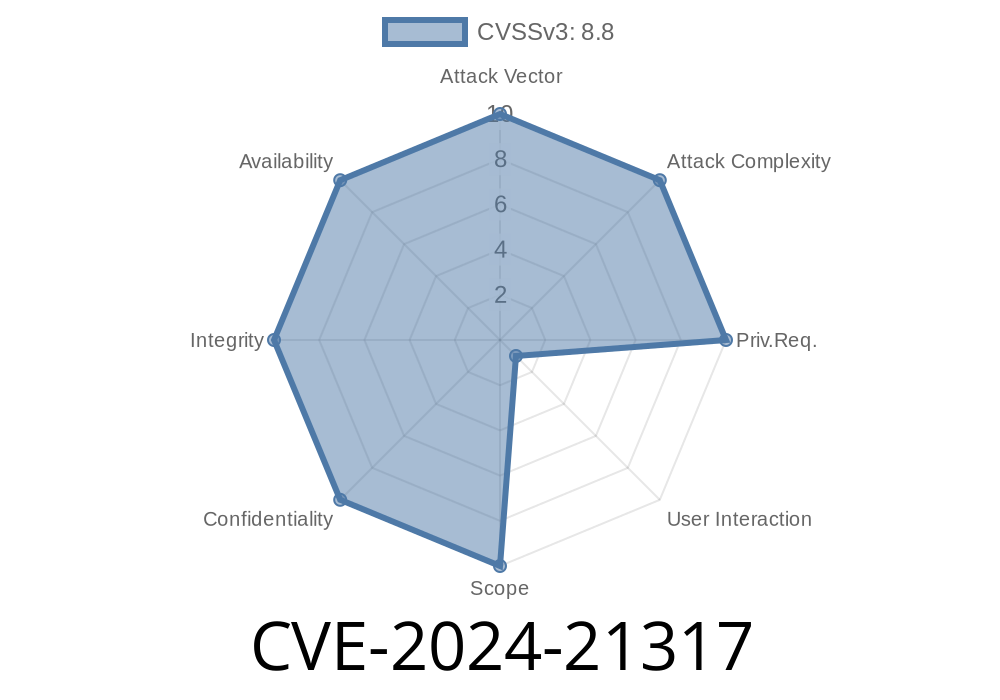
In early 2024, Microsoft disclosed and patched a critical security vulnerability, CVE-2024-21317, affecting the SQL Server Native Client (SQLNCLI) OLE DB provider. This flaw enables remote code execution (RCE) under certain conditions, presenting a serious risk to organizations using vulnerable versions of SQL Server or its client libraries.
In this post, we'll break down the vulnerability in simple terms, explain how it can be exploited, and offer code examples for both understanding and testing. We'll also share relevant links so you can dig deeper.
What is SQL Server Native Client OLE DB Provider?
The SQL Server Native Client (SQLNCLI) is a data access technology used by applications to talk to Microsoft SQL Server databases. OLE DB (Object Linking and Embedding, Database) is one method developers use to connect to SQL data.
By design, the OLE DB provider is a trusted part of your data stack. But in this case, a problem deep within this software layer opens your system up to severe attacks.
What is CVE-2024-21317?
CVE-2024-21317 is a remote code execution vulnerability that exists in the way the SQL Server Native Client OLE DB provider handles specially crafted data structures. An attacker who sends a specially crafted connection string or database response can trigger memory corruption, eventually gaining code execution privileges—often under the context of the SQL Server service or a client application.
Component: Microsoft SQL Server Native Client (SQLNCLI)
- Affected Versions: SQL Server 2012/2014/2016/2017/2019 Native Client (varies by patch status)
Exploit Scenario
Suppose your application connects to SQL Server using the OLE DB provider. An attacker, who can control either the SQL Server itself, a proxy in the middle, or trick an application into connecting to a malicious datasource, could deliver a malformed protocol response or a crafted connection string to exploit this bug.
Exploit Details & Code Snippet
Due to the severity of this vulnerability and its recent disclosure, no full public exploit code is available as of this writing. However, security researchers have demonstrated proof-of-concept triggers that crash the OLE DB client or escalate to full code execution.
Let’s look at a simplified proof-of-concept in Python that acts as a rogue SQL server to trigger the client crash (not full execution):
# WARNING: This is a crash PoC, not a weaponized RCE exploit.
# Requirement: The victim must connect with SQLNCLI OLE DB provider.
import socket
def rogue_sql_server():
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('...', 1433))
s.listen(1)
print("[*] Rogue SQL Server listening on port 1433")
conn, addr = s.accept()
print(f"[*] Connection from {addr}")
# Send a malformed initial handshake that triggers the bug
# Example garbage response (real payload will be crafted by attacker)
malformed_data = b'\x12\x34\x56\x78' * 100
conn.sendall(malformed_data)
conn.close()
if __name__ == '__main__':
rogue_sql_server()
A vulnerable client, connecting to tcp://your_ip,1433 using native OLE DB client, may crash or behave unexpectedly upon receiving this response. With further research, a skilled attacker can deliver a real payload for RCE.
Note: This example does *not* result in code execution. It demonstrates the primitive needed to start research and understand the impact.
Microsoft has released official patches for this vulnerability. It is critical to
- Install all recent security updates for SQL Server and SQLNCLI components from Microsoft here.
Block untrusted connections and verify all connection strings in applications.
For more technical details and official statements, see the Microsoft Security Guidance:
- Microsoft Security Advisory
- Microsoft SQL Server Blog
Patch immediately: Make sure all servers and clients using SQLNCLI are updated.
- Monitor logs: Watch for unexpected connections or crashes involving SQLNCLI/OLEDB.
Conclusion
CVE-2024-21317 is a critical vulnerability in a widely deployed Microsoft database component. The risk of remote code execution makes urgent patching essential for all organizations using SQL Server Native Client OLE DB.
References
- CVE-2024-21317: Official Description & Updates
- NIST NVD Entry
- Microsoft SQL Server Security Blog
Timeline
Published on: 07/09/2024 17:15:11 UTC
Last modified on: 08/13/2024 22:53:26 UTC