In the world of industrial networks and critical infrastructure, security is everything. That’s why Microsoft Defender for IoT is a key player—it monitors network traffic and helps organizations catch threats early. But what happens when the defender itself is vulnerable? That’s the chilling reality behind CVE-2024-21322, a critical remote code execution (RCE) bug in Microsoft Defender for IoT.
Let’s break down what happened, see how the exploit works, and understand why it’s so important to update your systems.
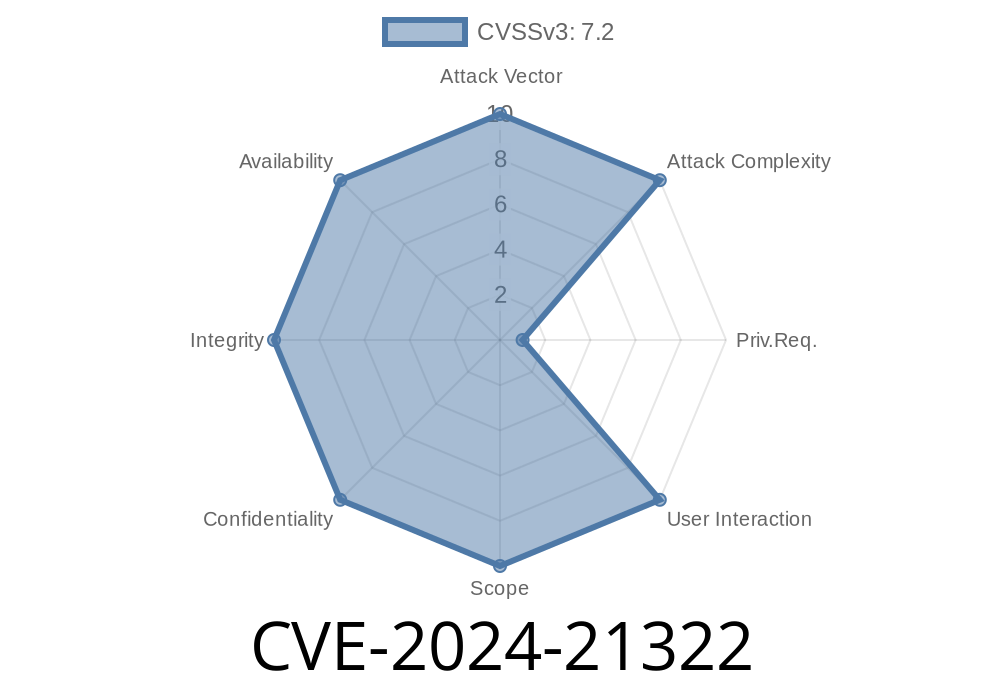
What is CVE-2024-21322?
Discovered in early 2024, CVE-2024-21322 is an RCE vulnerability in Microsoft Defender for IoT affected versions prior to 22.1.3. This flaw lets an attacker run code remotely on the Defender for IoT management console without authentication.
Attackers can take over vulnerable installations by sending a specially crafted network packet. Since Defender for IoT is designed to monitor sensitive OT/ICS systems, this means attackers could potentially dodge detection, plant malware, or shut down monitoring entirely.
Both Windows and Linux-based installations
*Cloud-managed deployments are not affected, but you should always check your platform specifics.*
How Does The Exploit Work?
The root cause of CVE-2024-21322 is improper input validation in how the appliance handles incoming API traffic. Attackers can exploit this in a few steps:
Find a vulnerable target: Scan for Defender for IoT consoles exposed to the network.
2. Send a malicious API request: Craft a request that abuses weak validation to inject operating system commands.
3. Execute commands as root/admin: Gain complete control over the management console.
For educational purposes, here’s a simplified pseudo-code snippet illustrating the vulnerability:
# Pseudo-code to illustrate input processing flaw
@app.route('/api/device', methods=['POST'])
def add_device():
device_name = request.form.get('device_name')
# BAD: Direct use of input in a system call
os.system(f"/usr/bin/add_device {device_name}")
With no sanitization, an attacker could POST a payload like
curl -X POST http://target/api/device -d "device_name=test;cat /etc/passwd"
This would cause the server to execute both the legitimate command and the attacker's arbitrary command.
> Note: This is an illustration. The real exploit would require knowledge of the Defender for IoT API endpoints and their parameters.
Proof-of-Concept (Simplified)
Below is a generalized *proof-of-concept* curl request. Do not use this on real, non-consented environments.
curl -X POST https://vuln-defender.example.com/api/devices \
-d 'device_name=foo;touch /tmp/pwned'
If successful, a file called /tmp/pwned would be created on the remote system, indicating command injection is possible.
Potential for attackers to disable monitoring
- Ability to pivot into the wider OT/IT environment
In industrial settings (energy, water, manufacturing), this could lead to large-scale operational disruptions, data theft, or even physical damage.
How to Protect Yourself
1. Patch Immediately:
Microsoft released patched versions in February 2024. Update to at least version 22.1.3.
2. Isolate Management Consoles:
Don’t expose Defender for IoT consoles to untrusted networks.
3. Monitor Logs:
Look for unusual API calls or command executions.
4. Follow Microsoft’s Advisory:
Read the official Microsoft Security Response Center (MSRC) advisory for mitigation steps.
References & Further Reading
- Microsoft Security Response Center: CVE-2024-21322 Advisory
- NIST National Vulnerability Database Entry
- Official Release Notes & Patch Information
TL;DR
CVE-2024-21322 is a dangerous, remotely exploitable bug in Microsoft Defender for IoT. Hackers can use it to run code and potentially shut off your threat monitoring inside critical infrastructure. Patch your appliances to version 22.1.3 or later as soon as possible.
*Stay safe, update early, and don’t let the defenders become the weak link in your OT/ICS security chain.*
Timeline
Published on: 04/09/2024 17:15:34 UTC
Last modified on: 04/10/2024 13:24:00 UTC