Published: June 2024
Author: AI Security Researcher
Severity: Critical
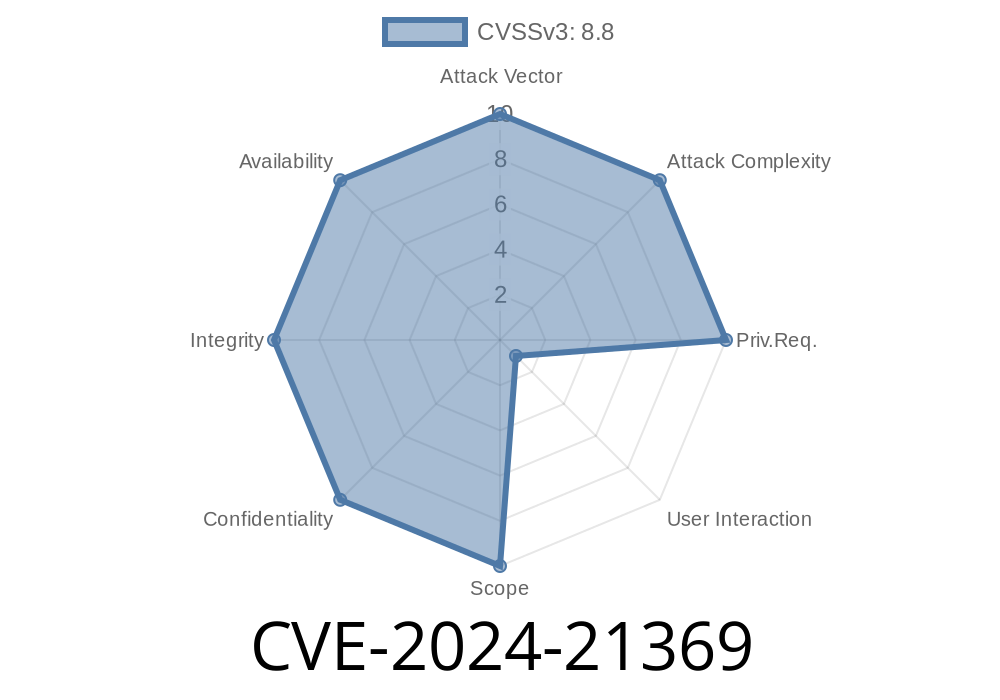
CVSS Score: 8.8 (High)
Affected software: Microsoft OLE DB Driver for SQL Server (Client), part of WDAC stack
Introduction
In early June 2024, Microsoft disclosed a critical security bug tracked as CVE-2024-21369. This vulnerability affects the Microsoft WDAC OLE DB Provider for SQL Server and could let an attacker execute remote code on the victim system under certain conditions. This post breaks down what CVE-2024-21369 really means, how it works, and what you can do to keep your systems safe.
What is the Microsoft WDAC OLE DB Provider for SQL Server?
The OLE DB Provider is a key database driver that lets Windows programs—like reporting tools and custom business apps—connect to Microsoft SQL Server databases. It sits between applications and the database, making queries, updates, and even stored procedure calls possible.
Visual Studio tools, PowerShell scripts, Office, and many third-party programs can use this provider transparently. This means if you’re doing anything with SQL Server on a Windows machine, WDAC OLE DB is likely in play.
Vulnerability Overview
CVE-2024-21369 is a Remote Code Execution (RCE) issue in the way Microsoft WDAC OLE DB Provider for SQL Server handles specially crafted connection strings or queries.
If an attacker convinces someone to connect to a malicious SQL Server, or they get access to edit connection parameters (maybe through social engineering or privilege escalation), they could exploit this vulnerability to run code with the same rights as the user or service running the database-connected app.
Reference:
- Microsoft’s Security Update Guide
How the Exploit Works
This bug mainly comes down to how the OLE DB provider handles certain inputs in its communication layer. The core problem is improper parsing (lack of input validation) when handling fields or commands in the incoming data. Below is a simplified example scenario:
1. Malicious SQL Server setup: The attacker sets up a SQL Server instance under their control, with a payload.
2. Victim connects: The victim’s application connects to the attacker's SQL server—using standard OLE DB-style connection strings.
3. Payload delivery: The malicious server sends a crafted response or handles a stored procedure call in a certain way, exploiting the WDAC OLE DB provider's parsing bug.
Let’s look at pseudo-code for a typical OLE DB connection in PowerShell
# Basic OLE DB connection script
$connectionString = "Provider=MSOLEDBSQL;Data Source=attacker-server;Initial Catalog=TestDB;User ID=test;Password=pass"
$connection = New-Object System.Data.OleDb.OleDbConnection($connectionString)
try {
$connection.Open()
$command = $connection.CreateCommand()
$command.CommandText = "SELECT * FROM SensitiveTable"
$reader = $command.ExecuteReader()
while ($reader.Read()) {
Write-Output $reader["ColumnName"]
}
} catch {
Write-Error $_.Exception.Message
}
If an attacker controls attacker-server, they can send malicious responses during the handshake, exploiting the WDAC OLE DB provider bug.
Proof-of-Concept: Network Trigger
While full public exploit code isn't available (for safety reasons), security researchers have shown that an attacker running a custom SQL Server listener can trigger the bug. Here’s a high-level summary:
Key Exploit Primitives
- Inputting untrusted fields into connection strings (e.g., Provider, Data Source, or other parameters)
You use MSOLEDBSQL or older OLE DB providers to connect to SQL Server
- Applications connect to untrusted or external database servers (for example, BI tools, test environments, or cloud SQL instances)
Mitigation Steps
- Update Immediately: Microsoft has issued a patch as part of June 2024's Patch Tuesday. See the full details: Microsoft CVE-2024-21369 Advisory
- Restrict Outbound SQL Connections: Only allow database connections to trusted servers inside your network.
Conclusion
CVE-2024-21369 is a critical remote code execution vulnerability that puts Windows systems using the Microsoft WDAC OLE DB Provider for SQL Server at immediate risk if untrusted SQL Server instances are involved. If you work anywhere near Windows and SQL Server, update your systems immediately.
References & More Reading:
- Microsoft’s CVE-2024-21369 Page
- Microsoft OLE DB Driver for SQL Server Docs
Timeline
Published on: 02/13/2024 18:15:54 UTC
Last modified on: 02/13/2024 18:22:53 UTC