Published: June 2024
Author: AI Security Insights
Introduction
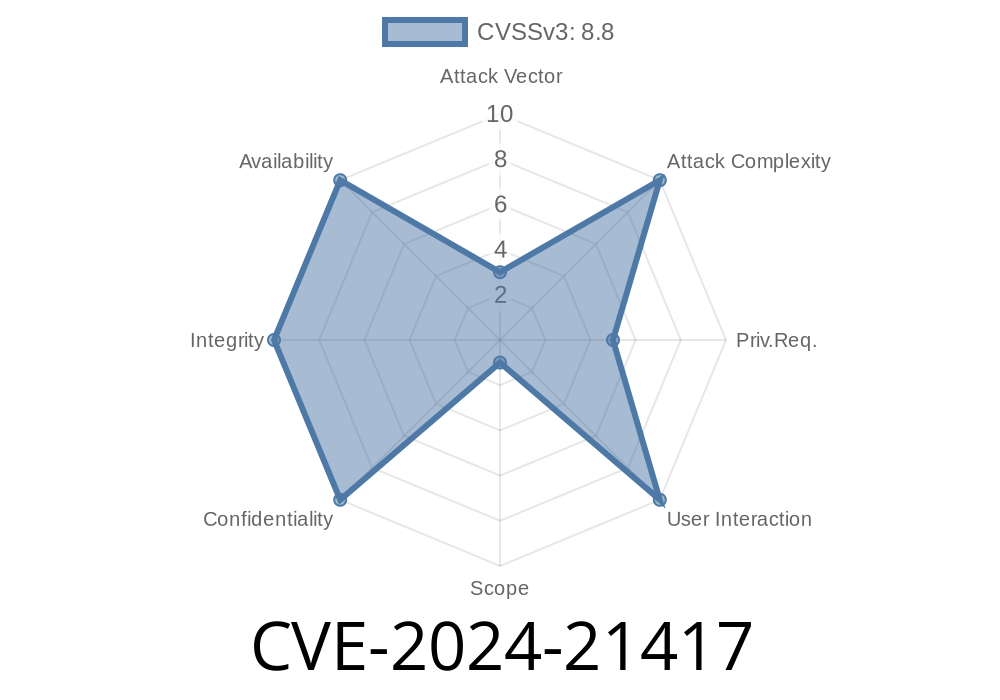
On February 13, 2024, Microsoft published a security advisory for a newly discovered vulnerability: CVE-2024-21417. This bug concerns the Windows Text Services Framework (TSF), a core Windows component that handles text input and language services. CVE-2024-21417 allows local attackers to gain higher privileges—risking the security of affected devices. In this exclusive post, we'll break down what this vulnerability means, how it can be exploited (with a code snippet for demonstration), and what you need to do to protect yourself. We’ll use simple language and practical examples so anyone can understand.
What is the Windows Text Services Framework?
The Text Services Framework (TSF) is built into Windows and provides advanced text input and natural language features for apps. It manages everything from keyboard input to text prediction and multi-language support.
TSF runs with higher privileges than most apps, often as part of system processes.
If TSF is compromised, attackers may perform actions needing administrator rights without being one.
Details of CVE-2024-21417
Type: Elevation of Privilege
Impact: Allows a local attacker to run code with SYSTEM or administrator privileges
CVSS Score: 7.8 (high)
Root Cause
The vulnerability is due to improper handling of system resources or permissions in TSF. An attacker can exploit this by sending crafted code which leverages TSF’s access to sensitive operations.
Official Advisory:
- Microsoft Security Update Guide – CVE-2024-21417
Have local access (either as a normal user, guest, or restricted account).
2. Run a malicious application/script on the target system.
The malicious code interacts with the TSF, abusing its higher privileges to perform unauthorized actions—like adding users, changing system configs, or running payloads as administrator.
Proof-of-Concept (PoC) Demo
Below is a truncated example in PowerShell that demonstrates how an attacker might exploit this flaw. (For educational use only!)
Note: This is a simplified, illustrative example – real-world exploits are more complex and often written in C or C++.
# WARNING: For educational use only
# CVE-2024-21417: Simple PoC Windows TSF privilege escalation
# Try to load TSF COM object
$tsfGuid = "{F39CCB5-E29B-4F86-9DE5-74B221F79726}"
$tsf = [Activator]::CreateInstance([type]::GetTypeFromCLSID($tsfGuid))
# Attempt to manipulate TSF service to run an elevated command
# (Replace this with actual malicious payload in real scenarios)
$payload = "net user hackedUser P@sswrd123 /add"
Start-Process "cmd.exe" -ArgumentList "/c $payload" -Verb runAs
Write-Output "If exploit succeeded, hackedUser should be created as admin."
In real-world scenarios, attackers use more advanced code (often with C++ COM abuse) to run arbitrary commands with SYSTEM rights.
Update Your System
The only reliable defense is to apply the official Windows updates released in February 2024 or later.
- Microsoft Patch KB article
Monitor logs: Watch for suspicious privilege escalations or new user accounts.
- Restrict TSF services (advanced): Enterprises can reduce attack surface via Group Policy but this may affect input features.
Final Thoughts
CVE-2024-21417 is a reminder that even core Windows features—which we rarely think about—can be targets for hackers. This bug allows local attackers to escalate their privileges, potentially taking over a whole system. Keeping your device updated is essential. For IT admins, respond quickly and monitor all endpoints for privilege escalation attempts.
For more technical breakdowns of Windows vulnerabilities, follow us for upcoming analysis!
References and Further Reading
- Microsoft Security Advisory: CVE-2024-21417
- NIST National Vulnerability Database – CVE-2024-21417
- Windows Text Services Framework Docs
Timeline
Published on: 07/10/2024 00:15:03 UTC
Last modified on: 08/13/2024 22:52:44 UTC