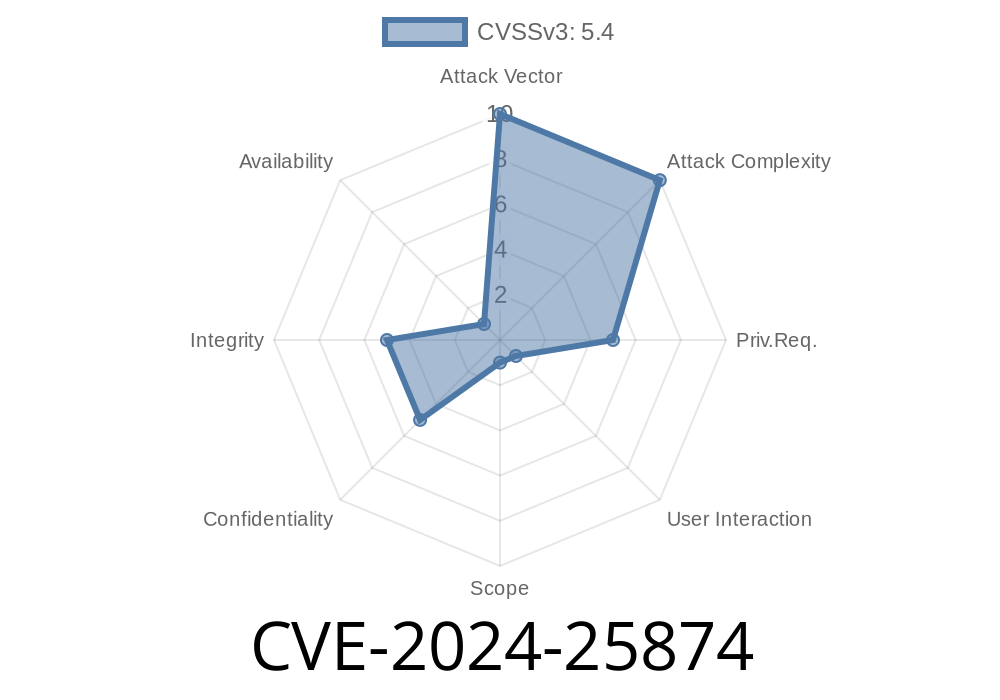
The recently discovered CVE-2024-25874 exposes a critical Cross-Site Scripting (XSS) vulnerability in Enhavo CMS v.13.1. Attackers can exploit this flaw in the New/Edit Article module, specifically by injecting malicious code into the Create Tag text field. This post breaks down how the vulnerability works, why it’s dangerous, and how attackers can exploit it. If you manage a site using Enhavo CMS, you’ll find instructions and example code right here to help you understand and mitigate the risk.
What is CVE-2024-25874?
CVE-2024-25874 is a stored XSS vulnerability in the New/Edit Article module of Enhavo CMS, an open-source content management system popular for its headless and flexible capabilities.
Vulnerable Version: Enhavo CMS v.13.1
- Vulnerable Component: Articles → Create/Edit → Tag field
Exploit Type: Stored Cross-Site Scripting (Stored XSS)
- CVE Link: CVE-2024-25874 on NVD *(link may be updated as NVD publishes details)*
How the Vulnerability Works
When users create or edit an article in Enhavo CMS, they can add tags through a Create Tag input box. The problem is that inputs are not sanitized properly, allowing attackers to inject JavaScript or HTML code.
Attacker logs in (or compromises an editor’s account).
2. They create/edit an article.
In the Create Tag field, attacker enters malicious JavaScript code (see code below).
4. When any user (including admins or visitors) loads the article with that tag, the script executes in their browser.
Below is a simple XSS payload an attacker might use. They insert this into the Tag field
<script>alert('XSS by CVE-2024-25874!');</script>
Go to the article creation page:
/admin/article/new or similar in your Enhavo instance.
`html
Save the article.
5. Visit the article in the admin or front-end. You will see a pop-up alert – proof your scripts are running.
Privileged escalation: Attackers could pivot to take over more powerful accounts.
Stored XSS is highly dangerous because it impacts every user who views the infected article or tags section.
Ensure that the input for tag names is properly sanitized on both the client and server sides.
- Use libraries such as DOMPurify for JavaScript or the htmlspecialchars() function for PHP.
The maintainers are expected to release a patch soon. Update as soon as a fix is available.
- Monitor Enhavo’s GitHub for security updates.
More About Enhavo CMS
- Official website: https://enhavo.com
- GitHub repository: https://github.com/enhavo/enhavo
- Issues and security advisories: Enhavo GitHub Issues
Conclusion
CVE-2024-25874 is a high-severity XSS bug in Enhavo CMS v.13.1, caused by unsafe handling of tag input in the New/Edit Article module. Attackers can run JavaScript in victim browsers – a risk for all users and site administrators.
Patch immediately. Until a fix rolls out, sanitize all user input and audit your CMS for malicious tags. Stay aware of security bulletins from both Enhavo CMS and major vulnerability databases.
Sources
- Official Enhavo CMS
- CVE-2024-25874 at NVD
*If you have questions about detection or patching, feel free to comment below or check the Enhavo community forums.*
Timeline
Published on: 02/22/2024 14:15:46 UTC
Last modified on: 08/27/2024 19:35:17 UTC