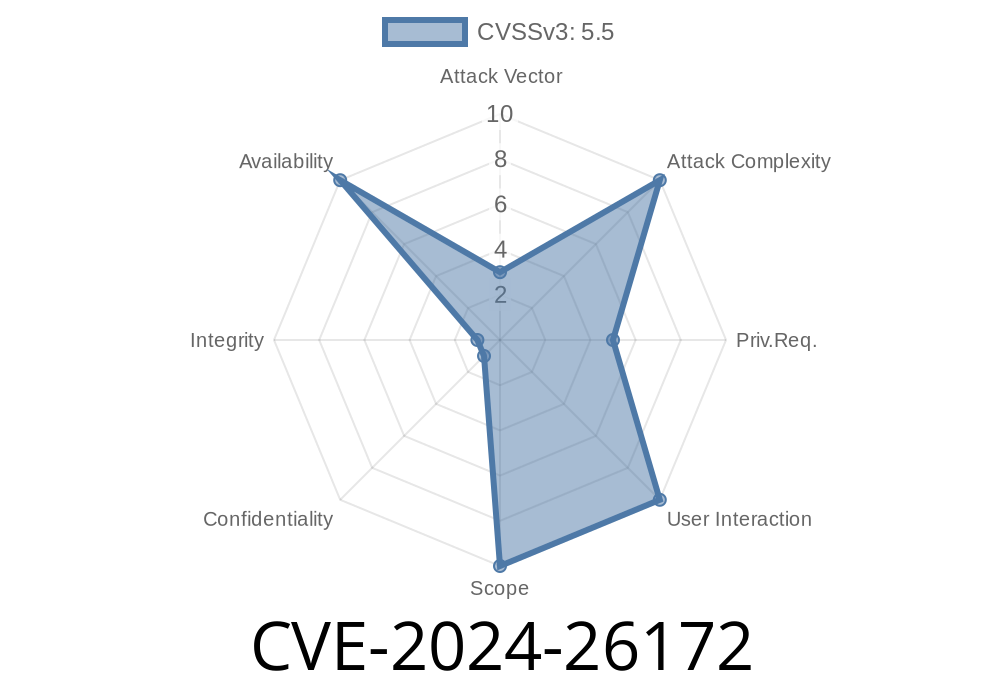
In February 2024, Microsoft disclosed and patched a significant vulnerability in the Desktop Window Manager (DWM) Core Library, labeled CVE-2024-26172. This flaw, primarily affecting Windows 10, Windows 11, and corresponding server editions, allows a local attacker to exploit the affected system and potentially access sensitive information.
This post breaks down what CVE-2024-26172 is, how an attacker can exploit it, why it's dangerous, and what you should do to protect your systems. We’ll also provide code snippets, detailed explanations, and links to relevant resources.
What is DWM and Why is it Important?
The Desktop Window Manager (DWM) is a critical Windows process that manages visual effects on the desktop—think transparency, live taskbar thumbnails, and even virtual desktops. Since DWM runs with high privileges and handles lots of inter-process data, bugs in it can be attractive for attackers.
What is CVE-2024-26172?
CVE-2024-26172 is an *information disclosure* vulnerability. It means attackers could potentially read sensitive information that they normally shouldn't be able to. In the context of this vulnerability, DWM's core library failed to manage memory properly, possibly leaking kernel memory or data from other processes to a less-privileged user.
Impact: Information Disclosure (not code execution)
Microsoft Advisory:
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-26172
NVD Reference:
https://nvd.nist.gov/vuln/detail/CVE-2024-26172
How Does the Vulnerability Work?
When a Windows application interacts with DWM, it sends drawing data, window content, and other graphical metadata. Due to an insufficient initialization or validation routine, DWM might mistakenly copy memory regions—including sensitive content—back to userland in certain responses or returned structures.
Example Vulnerable Scenario
When you call certain API functions or system calls, you expect Windows to fill out structures only with your data. With this flaw, uninitialized memory may also be included.
Consider the following pseudocode (simplified for clarity)
typedef struct {
int windowId;
BYTE imageBuffer[2048]; // Might contain leftover bytes!
} DWM_RENDER_RESULT;
DWM_RENDER_RESULT result = {};
HRESULT hr = DwmGetSomeData(windowHandle, &result);
if (SUCCEEDED(hr)) {
// Process result.imageBuffer
// But imageBuffer might leak other process memory!
}
Here, imageBuffer may include memory from previous DWM interactions (possibly from other windows or even processes), which may have sensitive data like passwords, documents, or security tokens.
Make multiple calls to DWM-related APIs, collecting the returned buffers.
3. Scan returned buffers for interesting data types, such as file paths, snippets of text, or authentication tokens.
Proof-of-Concept Code
While no public working exploit exists, here’s a basic Python snippet using ctypes that demonstrates the idea (note: Windows APIs would need to be properly imported—this is illustrative only):
import ctypes
# Hypothetical structure representing a DWM data buffer
class DWM_RENDER_RESULT(ctypes.Structure):
_fields_ = [("windowId", ctypes.c_int),
("imageBuffer", ctypes.c_byte * 2048)]
# Load DWM DLL (in reality, would require more setup)
dwmapi = ctypes.windll.dwmapi
result = DWM_RENDER_RESULT()
window_handle = ... # Obtain a window handle here
hr = dwmapi.DwmGetSomeData(window_handle, ctypes.byref(result))
if hr == : # S_OK
# Save imageBuffer bytes for later analysis
with open("leaked_data.bin", "wb") as f:
f.write(bytes(result.imageBuffer))
Attackers could automate this to collect large amounts of data and analyze it offline.
Real-World Impact
- Credential Leakage: Data from sensitive applications (password managers, browsers) might be exposed.
Document Exposure: Bits of sensitive corporate documents might leak from editor windows.
- Token/Session Information: Authentication details or session tokens could be partially reconstructed.
How to Defend Yourself
- Patch Immediately! Microsoft has patched this vulnerability in security updates released February 13, 2024. Install all Windows updates (especially:
Windows 10: KB5034763
- Windows 11: KB5034765 / KB5034766
- Check official update guide)
Restrict Local Access: Prevent unauthorized users or malware from running code locally.
- Monitor for Suspicious Behavior: Watch for programs accessing large amounts of DWM memory or rapidly enumerating windows.
Reference Links
- Microsoft CVE-2024-26172 Official Advisory
- National Vulnerability Database: CVE-2024-26172
- Windows Update Catalog
- Understanding DWM
Conclusion
CVE-2024-26172 is not as flashy as a remote code execution vulnerability, but information leaks can be just as disastrous, especially in shared environments or multi-user kiosks.
Keep your Windows systems updated, minimize local privilege, and always be alert for unexpected Windows security bulletins. If you manage critical infrastructure or handle sensitive workflows, ensure your patch cadence is rapid.
Timeline
Published on: 04/09/2024 17:15:36 UTC
Last modified on: 04/10/2024 13:24:00 UTC